Yobi
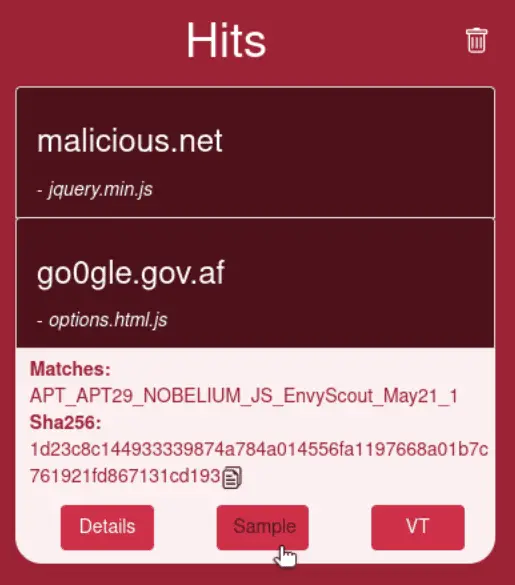
Yobi is a basic Firefox extension which allows to run public or private YARA rules on all scripts and pages rendered by the browser. Yobi saves files that trigger its rules and allows further inspection of them.
Yobi is completely serverless – no telemetry or other information is collected.

What can Yobi do?
- Capture any file requested by the web browser and identified as malicious by a YARA rule.
- Use custom YARA rules.
- Download the malicious files (as zip, default password is “infected”).
- Query the file hash in VirusTotal.
YARA rules
YARA rules are fetched from a repository of JS rules I created: js-yara-rules. The repo consists of free JS rules I found on the internet and some I wrote myself. Feel free to create pull requests for additional relevant rules.
You can change the yara rules the extension uses under Add-ons->Yobi->Preferences
Right now, YARA version 4.0.5 is used. libyara-wasm will be updated shortly and Yobi will then run the latest YARA versions.
Yobi’s Inner Workings
Execution Flow
Yobi uses the Gecko webrequests feature browser.webRequest.onBeforeRequest which enables it to intercept any request and response. Yobi saves the buffer and forwards it. The YARA rules run asynchronously to that and alert whether a match is found.
Dependencies
Yobi Depends on the following libraries:
- libyara-wasm – A porting of the whole YARA engine to wasm
- SJCL – JS encryption library used for calculating sha256.
- jszip – A compact JS library to create zip files. used PR 6969 that added the option to encrypt the archive.
- Bootstrap
- jQuery
Why doesn’t Yobi block the malicious scripts?
Preventing any script to run before running YARA rules on it would create a significant delay for the user.=
Install
Manual Installation
- clones the repo: git clone https://github.com/imp0rtp3/Yobi.git
- Go to about:debugging in Firefox or other Gecko-based browsers, click “This Firefox”-> Load Temporary Add on and select manifest.json.
- Done!
Download
Copyright (C) 2021 imp0rtp3