Image: Mikko Kenttälä
In a recent analysis, security researcher Mikko Kenttälä exposed a critical zero-click vulnerability chain in macOS, potentially affecting millions of users. This exploit, dubbed the “Zero-Click Calendar Invite,” allows attackers to execute malicious code on a victim’s machine remotely, without any user interaction.
The vulnerability chain involves a series of exploits that target the macOS Calendar application. By sending a specially crafted calendar invite, an attacker can bypass security measures and gain unauthorized access to the victim’s system. Once inside, the attacker can execute arbitrary code, potentially leading to data theft, system compromise, or even complete control over the device.
Kenttälä’s analysis details the intricate steps involved in the exploit chain, highlighting the sophistication and severity of the vulnerability. The attack leverages a combination of file manipulation, privilege escalation, and social engineering techniques to achieve its goals.
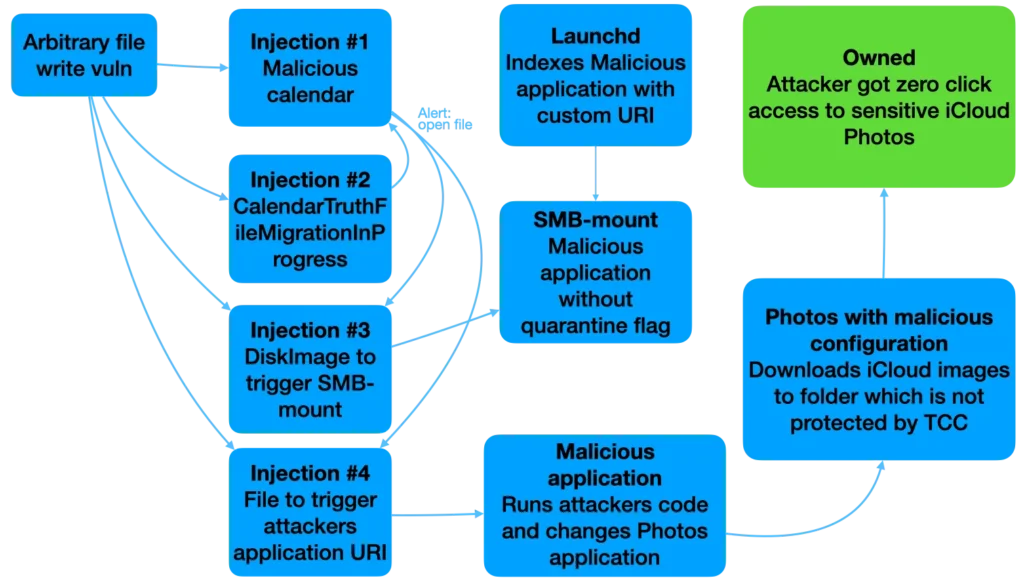
The first phase of the attack chain begins with a flaw in how macOS Calendar handles file attachments. By sending a malicious calendar invite, an attacker can craft file paths to add or delete arbitrary files inside the Calendar app’s sandbox. This is made possible through a directory traversal attack, in which the attacker manipulates file paths to place attachments in unintended locations.
This vulnerability tracked as CVE-2022-46723 (CVSS 9.8), was critical enough to warrant immediate attention. By itself, it allows attackers to remove or overwrite existing files within the Calendar environment.
Building on the arbitrary file write vulnerability, the second phase of the attack enables remote code execution (RCE) when the victim upgrades their macOS system. Kenttälä discovered that during a version upgrade (e.g., from Monterey to Ventura), the exploit could trigger malicious files embedded within the calendar.
This sophisticated exploit bypasses several security mechanisms, including Apple’s Gatekeeper, by using a Samba server trick to mount and execute files without triggering quarantine warnings. Once the payload is executed, the attacker gains the ability to manipulate the system’s Calendar data remotely.
Perhaps the most alarming aspect of this exploit is its ability to access sensitive iCloud Photos data. By manipulating macOS’s Photos configuration, the attacker can change the System Photo Library to an unprotected directory. This enables access to iCloud-synced photos, which are downloaded to the attacker’s chosen location. The final payload, a script called PhotosPoC.sh, kills any running Photos applications and imports a new configuration, syncing the victim’s iCloud photos to a compromised directory.
Once the photos are stored locally, they can be exfiltrated via external servers using a simple curl command. This attack chain provides the attacker full access to the victim’s private photos, which can be stolen and shared without any user awareness.
Apple acted swiftly to patch these vulnerabilities, with fixes rolling out between October 2022 and September 2023. As part of their security updates, Apple has mitigated the arbitrary file write vulnerability and strengthened the protections around the Calendar and Photos apps to prevent such attacks.
Related Posts:
- Mac App Store discovers cryptocurrency Miner in “Calendar 2” application
- Google Warns: Calendar Service Hijacked for Malware Control
- OpenAI announces a bug bounty program, providing a bug bounty ranging from $200 to $20,000