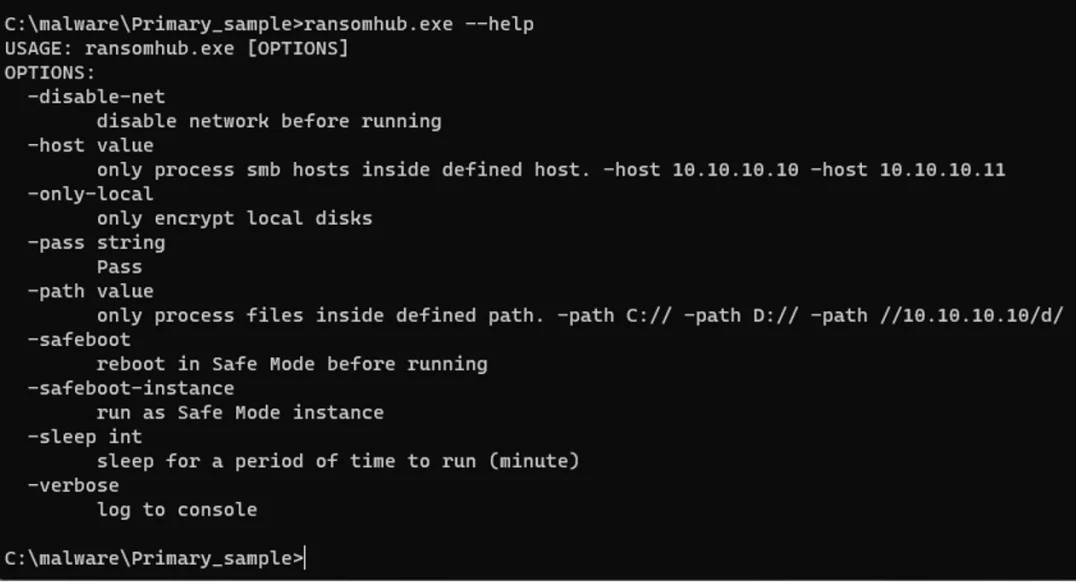
RansomHub command-line help menu
A new ransomware threat, dubbed RansomHub, has rapidly ascended to become one of the most prolific ransomware groups currently active. Symantec’s Threat Hunter team has uncovered a strong link between RansomHub and the older Knight ransomware, suggesting that RansomHub is essentially a rebranded and updated version of its predecessor.
RansomHub appears to have evolved from Knight ransomware, which was originally known as Cyclops. The source code for Knight was sold on underground forums in February 2024 after its developers shut down their operations. This code likely fell into the hands of other threat actors who modified and relaunched it as RansomHub. Despite the significant similarities, it is believed that the original creators of Knight are not behind RansomHub.
Both RansomHub and Knight exhibit striking resemblances in their code, ransom notes, and even the unique technique of restarting endpoints in safe mode before encryption. This tactic was previously observed in other ransomware strains like Snatch and Noberus, raising questions about potential connections between these groups.
In recent investigations, Symantec found that RansomHub attackers gained initial access by exploiting the Zerologon vulnerability (CVE-2020-1472), which grants domain administrator privileges. They then utilized dual-use tools such as Atera and Splashtop for remote access and NetScan for network discovery. The RansomHub payload used iisreset.exe and iisrstas.exe to stop all Internet Information Services (IIS) services before deploying the ransomware.
RansomHub’s swift rise can be attributed to its ability to attract former affiliates of the recently closed Noberus (also known as ALPHV or BlackCat) ransomware group. Notably, an affiliate known as Notchy is now working with RansomHub. Additionally, tools linked to another Noberus affiliate, Scattered Spider, were used in recent RansomHub attacks.
Since its first appearance in February 2024, RansomHub has quickly established itself as a dominant player in the ransomware landscape. In the past three months, it has become the fourth most prolific ransomware operator in terms of attack numbers. The group’s high-profile targets include the UK auction house Christies.
RansomHub’s rapid ascent and significant impact highlight the evolving nature of ransomware threats. Organizations are urged to patch vulnerabilities promptly, monitor for suspicious activities, and educate employees on the risks of phishing and other common attack vectors