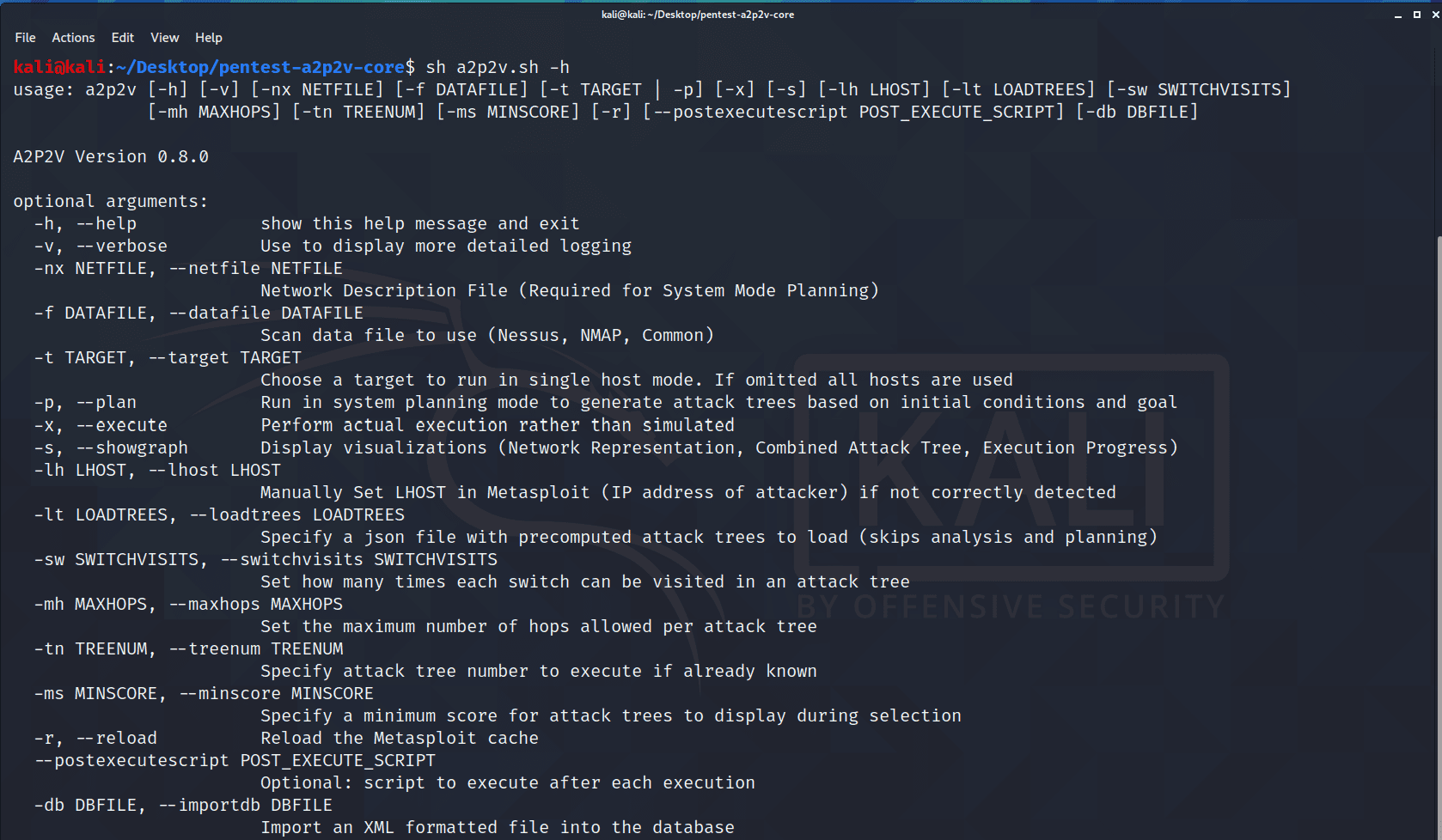
A2P2V
Automated Attack Path Planning and Validation (A2P2V) is a planning and cyber-attack tool that provides the capability for users to determine a set of ranked attack sequences given a specific attacker goal. The aim of the tool is to simplify the process so that non-security experts can generate clear, actionable intelligence from basic inputs using as much automation as possible and generating easy to interpret reporting.
The system uses known network topology and system vulnerability information to determine all sets of attack sequences to obtain the attacker goal and outputs the required steps (as Metasploit commands) for the selected sequence.
The input to the system includes:
- Initial conditions: modeling the knowledge and current access of the attacker
- Attacker goal: indicating a change in state (e.g. change the temperature on an ICS system) or remote access to a specific target host
- Vulnerability information: results of Nessus or Nmap scans or data custom (CVS) input format
- Network topology: a custom XML format describing host information and network connectivity
- Capability details: a custom XML format describing a set of known services and exploits specified using a PAP (Pre-condition, Action, and Post-condition) model.
Changelog v1.1
Added
- Add script “metasploitpap.py” and “capabilitydb.py”
- Add .common2 format sample file to the “lab_config” directory
- Add YAML-formatted attack database
Changed
- Introduce PyYAML library
- Remove XML-formatted attack database
- Refactor into some methods to support YAML-formatted attack database
- Change license references to SPDX license identifier
Fixed
- Modify the script “run_msfrpcd.sh”
- for the users who is not installed metasploit locally
- Modify some typo
Install & Use
Copyright (C) 2018-2021 Toshiba Corporation and Perspecta Labs, Inc.