ACLight v2.0: advanced discovery of Privileged Accounts
ACLight
A script for an advanced discovery of Privileged Accounts – includes Shadow Admins.
The tool was published as part of the “Shadow Admins” research – more details on “Shadow Admins” are in the blog post.
Overview
ACLight is a tool for discovering privileged accounts through advanced ACLs (Access Lists) analysis. It includes the discovery of Shadow Admins in the scanned network.
The tool queries the Active Directory (AD) for its objects’ ACLs and then filters and analyzes the sensitive permissions of each one. The result is a list of domain privileged accounts in the network (from the advanced ACLs perspective of the AD). You can run the scan with just any regular user (could be a non-privileged user) and it automatically scans all the domains of the scanned network forest.
Just run it and check the result.
You should take care of all the privileged accounts that the tool discovers for you. Especially – take care of the Shadow Admins – those are accounts with direct sensitive ACLs assignments (not through membership in other known privileged groups).
ACLight2
This is ACLight2 – the new version of ACLight scan. It’s much quicker, has a new scan architecture and better results.
It solves scalability and performance issues from the previous version.
In addition, ACLight2 is built on a recursive scan and provides multi-layered privileged accounts analysis.
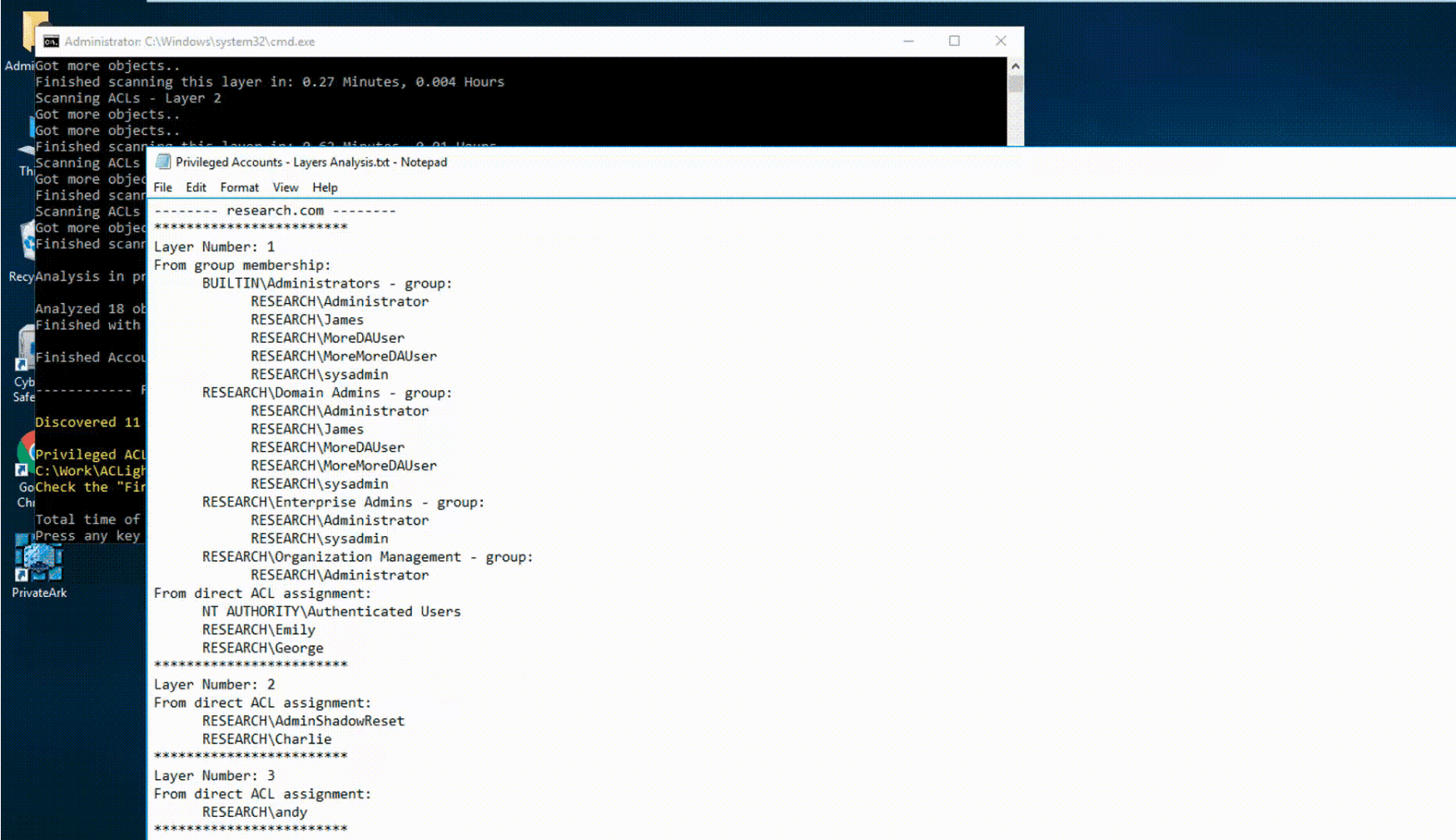
As a first step, the scan starts by building the first layer of privileged accounts. Those are the accounts who have direct privileges over the domain’s sensitive objects. Then, as a second step, the tool continues and scans the ACLs over those newly discovered privileged accounts from layer 1 and builds an optional second layer of new privileged accounts who have privileges over the accounts from the first layer. This second step is recursive, the tool keeps scanning for more optional layers of privileged accounts until all the privileged accounts chains are being enumerated.
Download
git clone https://github.com/cyberark/ACLight.git
Usage
Option 1:
- Double click on “Execute-ACLight.bat”.
Option 2:
- Open PowerShell (with -ExecutionPolicy Bypass)
- Go to “ACLight2” main folder
- “Import-Module ‘.\ACLight2.psm1’”
- “Start-ACLsAnalysis”
Choose the target domain:
By default, ACLight automatically scans all the domains of the scanned network forest. You can use the “Domain” parameter if you are interested in scanning only one specific domain:
- Start-ACLsAnalysis -domain “DomainName.com”
Demo

Reading the results files:
- First, check the scan’s executive summary “Privileged Accounts – Layers Analysis.txt” – It’s an important and straight-forward list of the most privileged accounts that were discovered in the scanned network.
- “Privileged Accounts Permissions – Final Report.csv” – This is the final summary report, in this file you will find what are the exact sensitive permissions each account has.
- “Privileged Accounts Permissions – Irregular Accounts.csv”, similar to the final report with only the privileged accounts that have the direct assignment of ACL permissions (not through their group membership).
Copyright (c) 2017
All rights reserved.
Source: https://github.com/cyberark/





