ADMiner
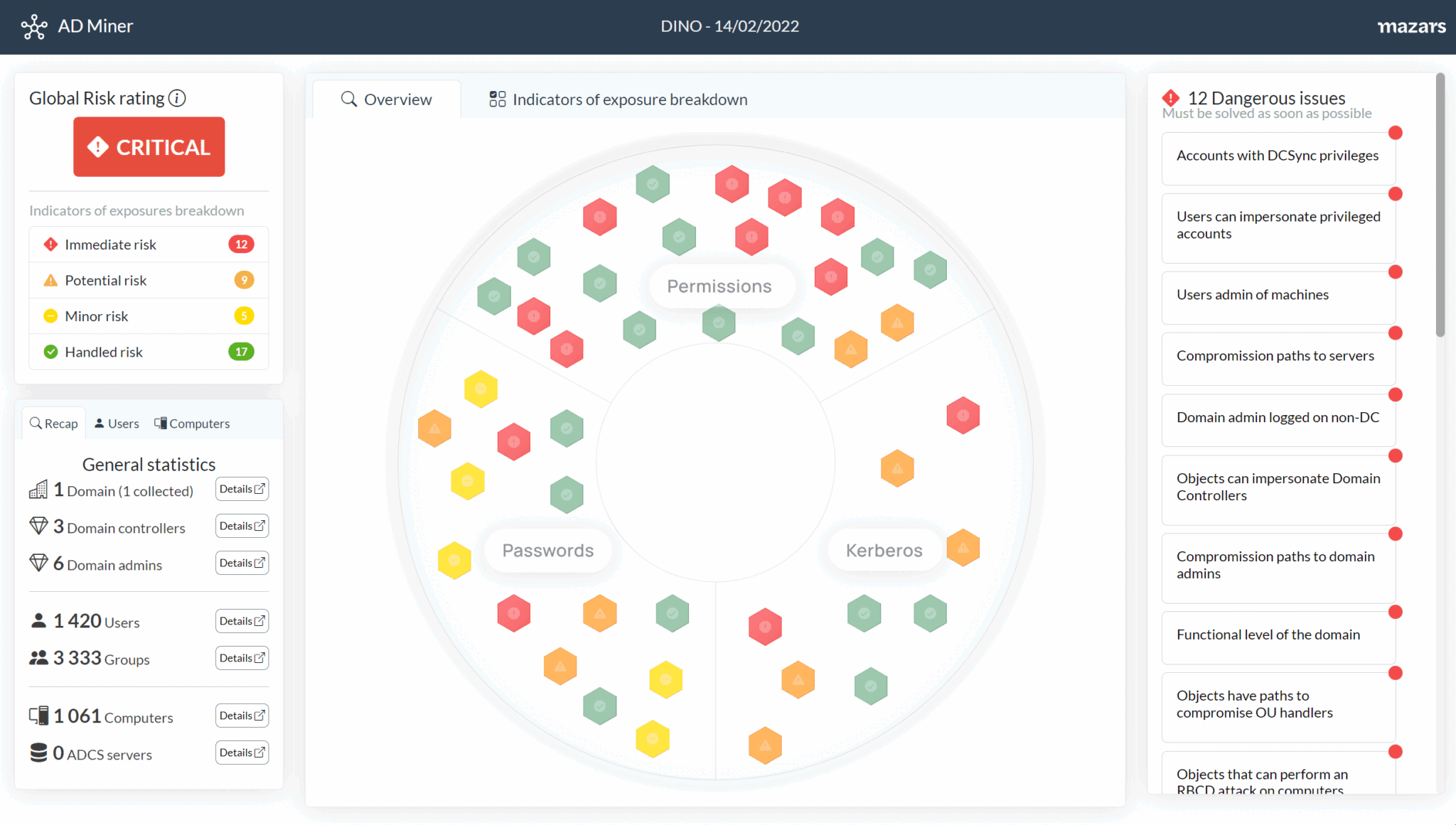
ADMiner is an Active Directory audit tool that leverages cypher queries to crunch data from the BloodHound graph database (neo4j) and gives you a global overview of existing weaknesses through a web-based static report, including detailed listing, dynamic graphs, key indicators history, along with risk ratings.
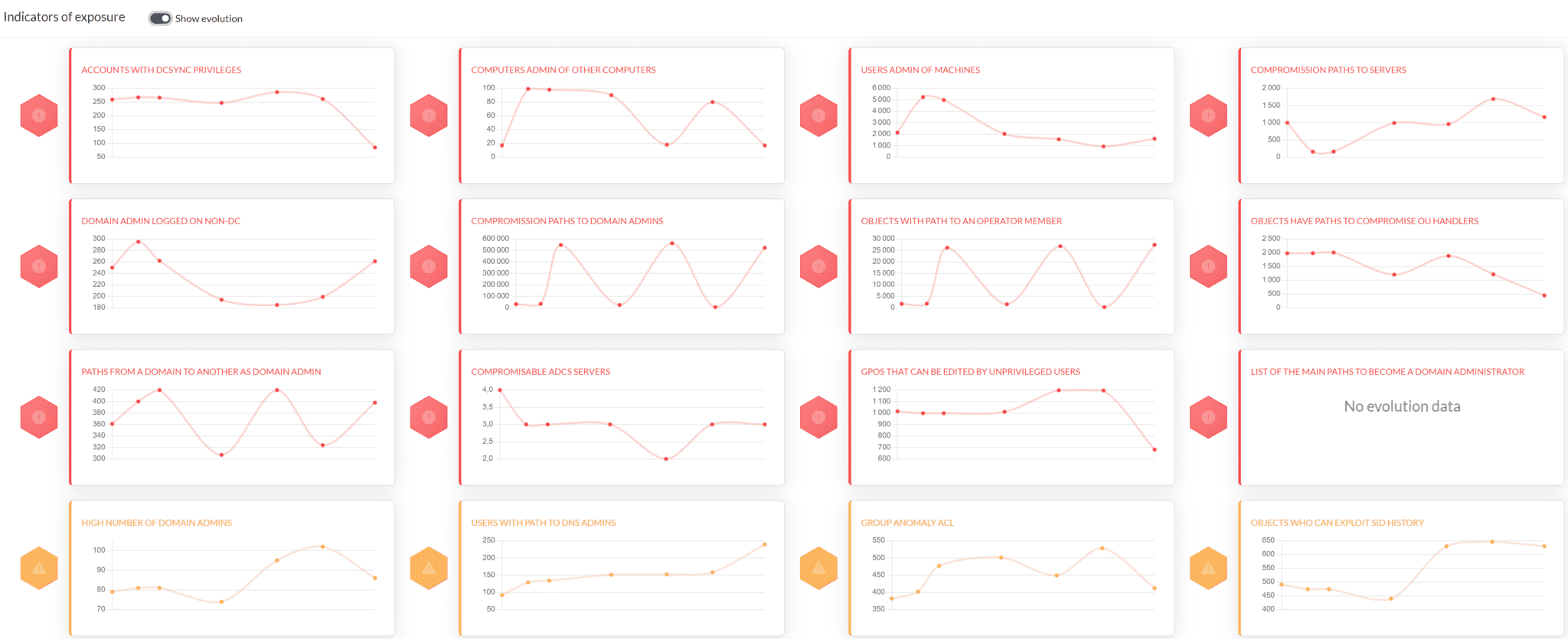
You can also observe indicators over time to help measure mitigation efficiency.

Implemented controls
The following provides a list controls that have already been implemented in AD Miner :
| Dormant accounts | Tier 0 sessions violation | Control path cross domain from DA to DA |
| Ghost computers | Machine accounts with admin privs | Control paths to GPOs |
| Accounts without password expiration | Obsolete OS | Control paths to servers |
| Accounts with old passwords | Inadequate number of domain admins | Control paths to OU |
| Accounts with clear-text passwords | RDP access | Control paths to GMSA passwords |
| Kerberoastable accounts | Domain functional level | Control path to AdminSDHolder container |
| AS-REP Roastable accounts | Users with admin privs | Users with path to DNS Admins |
| Accounts with SID history | Machine accounts with high privs | ACL anomalies on group objects |
| LAPS status | Non tier 0 with DCSync capabilities | Objects with path to an Operator Member |
| LAPS access | Unconstrained delegations | ADCS local admin privs |
| KRBTGT password age | Constrained delegations | Empty groups/OU |
| DC Shadow to DA | Role-based constrained delegations | |
| DC Shadow to all | Control paths to domain admins |
Changelog v1.1
Bug Fixes
- better request for low privilege impersonation (#121) (71ceb57)
- bug with u.name (#123) (26cb9d8)
- bugs with charts and azure data (#114) (7523229)
- correct spelling of GPLink to take it into account when computing paths (337320d)
- fix typo in request leading to missing DCs (#118) (3867f20)
Features
Performance Improvements
Install
git clone https://github.com/Mazars-Tech/AD_Miner.git
pip install -r requirements.txt
Use
Copyright (C) 2023 Mazars Cybersecurity Audit & Advisory team
Source: https://github.com/Mazars-Tech/