Second Powershell script | Image: McAfee
In the ever-evolving landscape of cybersecurity threats, one campaign has recently caught the attention of McAfee Labs. This sophisticated VBS script-driven campaign employs obfuscated Visual Basic Scripting (VBS) to deliver a range of malware, transcending beyond its initial AgentTesla roots. With a focus on stealthy and versatile delivery mechanisms, this campaign has become a multifaceted threat, distributing malware such as Guloader, Remcos RAT, Xworm, and Lokibot.
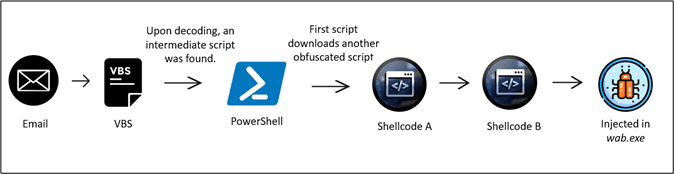
At the core of this campaign is an elaborate infection process that starts with a VBS file delivered via email.
- Stage 1: Activation of VBS Script
The infection process kicks off when the recipient opens an email attachment, a ZIP file masquerading as an innocuous invoice. Inside this ZIP file lies a heavily obfuscated VBS script, meticulously designed to deter analysis. The script is laden with garbage variables, decoy functions, and unnecessary comments, all aimed at making it challenging to decipher.
After removing redundancies and comments, the script becomes more streamlined and efficient. Strings are concatenated and formatted, making it appear intriguingly complex. A key function, “Mikr9,” is used to convert strings into a readable format, unveiling the malicious intent hidden within.
- Stage 2: PowerShell Phases

The deobfuscated VBS script triggers the execution of the first-stage PowerShell. Subsequently, the campaign utilizes the BitsTransfer utility to fetch a second-stage PowerShell script, which is base64 encoded and decoded for execution.
Upon decoding the second-stage PowerShell, a detailed analysis reveals its functionality. It loads the VirtualAlloc() function and prepares for the execution of concealed shellcode.
- Stage 3: Shellcode-A Execution
The first shellcode, extracted from the PowerShell script, is executed. Its primary task is to copy the second shellcode, Shellcode B, into memory. Shellcode B is then decrypted using an XOR operation, rendering it executable within the system’s memory.
- Stage 4: Shellcode-B Injection
Shellcode B is designed to establish a new process named “wab.exe” and injects the content decrypted from the second shellcode into this process. “wab.exe” then connects to a specified URL to fetch the encrypted Remcos RAT payload.
Upon decryption, the Remcos RAT malware communicates with a remote IP address and initiates malicious activities, including keylogging and capturing screenshots.
This VBS script-driven campaign exemplifies the ingenuity of modern cybercriminals in deploying malware. It starts with an innocuous-looking email attachment and progresses through intricate stages of obfuscation and execution. The malware payloads are concealed within shellcodes and injected into legitimate processes, making detection challenging.
As cybersecurity threats continue to evolve, organizations and individuals must stay vigilant. Employing robust email filtering, antivirus solutions, and regular security updates can help mitigate the risks associated with campaigns like these. Understanding the inner workings of such campaigns empowers defenders to better protect against these stealthy and multifaceted threats.