Operation process
A new threat has emerged, dubbed VenomRAT (AsyncRAT), this Remote Access Trojan (RAT) represents a sophisticated blend of stealth and malicious intent, cleverly masquerading as benign entities to infiltrate unsuspecting users’ systems.
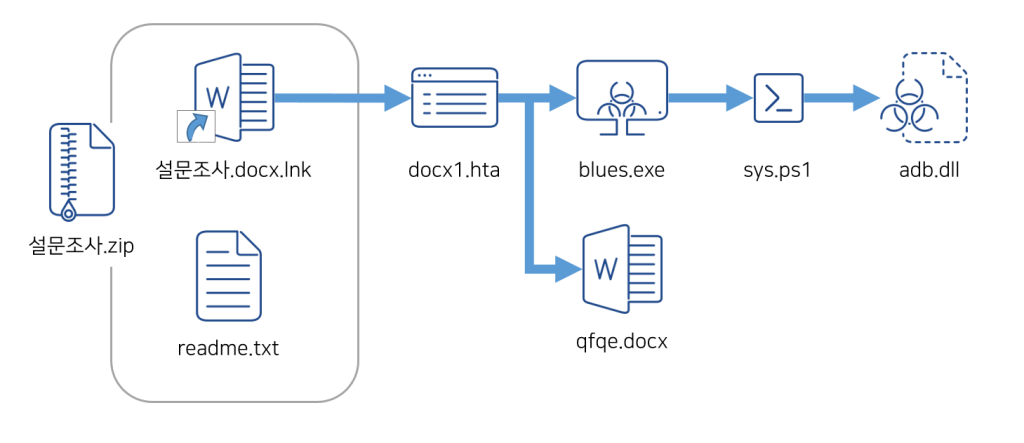
The AhnLab Security Intelligence Center (ASEC) has recently uncovered a cunning method of distribution employed by VenomRAT: a shortcut file (.lnk) disguised as a legitimate Word document titled ‘Survey.docx.lnk’. Nestled within a compressed archive alongside a legitimate text file, this file serves as a Trojan horse, inviting the unwary to unwittingly unleash the malware upon their devices. This executable file, known as ‘blues.exe’, further cloaks its nefarious nature by posing as a certificate from a Korean IT company.

The insidious operation of VenomRAT unfolds in multiple stages, each meticulously designed to evade detection and maximize impact. Initially presented as a ‘survey’, the compressed file lures users into opening it, containing both a benign text file and the malicious LNK file. The latter harbors a command that, once executed, connects to an external URL via mshta to run additional script codes.
These scripts, embedded with obfuscated strings, unravel to reveal PowerShell commands that orchestrate the download of further malicious files into the %appdata% folder, setting the stage for their execution. Among the downloaded files, ‘qfqe.docx’ stands out as a legitimate-looking Word document packed with survey information, designed to lull users into a false sense of security.
The ‘blues.exe’ file, a downloader-type malware disguised as a legitimate certificate, performs the next act in this malicious ballet. Upon execution, it beckons additional scripts via PowerShell, pulling them from a shadowy internet corner. These scripts, in turn, fetch ‘adb.dll’, a file teeming with encoded shellcode that, once decrypted, unleashes VenomRAT’s full spectrum of capabilities.
VenomRAT’s ultimate execution reveals its true colors: a keylogger and a thief of user PC information. Beyond these sinister activities, it stands ready to perform a variety of malicious behaviors, all at the behest of its remote operator. This capability to receive and execute commands remotely underscores the RAT’s versatility and the grave threat it poses.
With malicious shortcut files continuing to circulate, camouflaged as ordinary documents, the importance of vigilance has never been more pronounced. Users must exercise caution, recognizing that the seemingly innocuous ‘.lnk’ extension could veil a dire threat. AhnLab’s findings serve as a stark reminder of the persistent and evolving dangers that lurk within the security domain, urging users and cybersecurity professionals alike to remain ever-watchful.