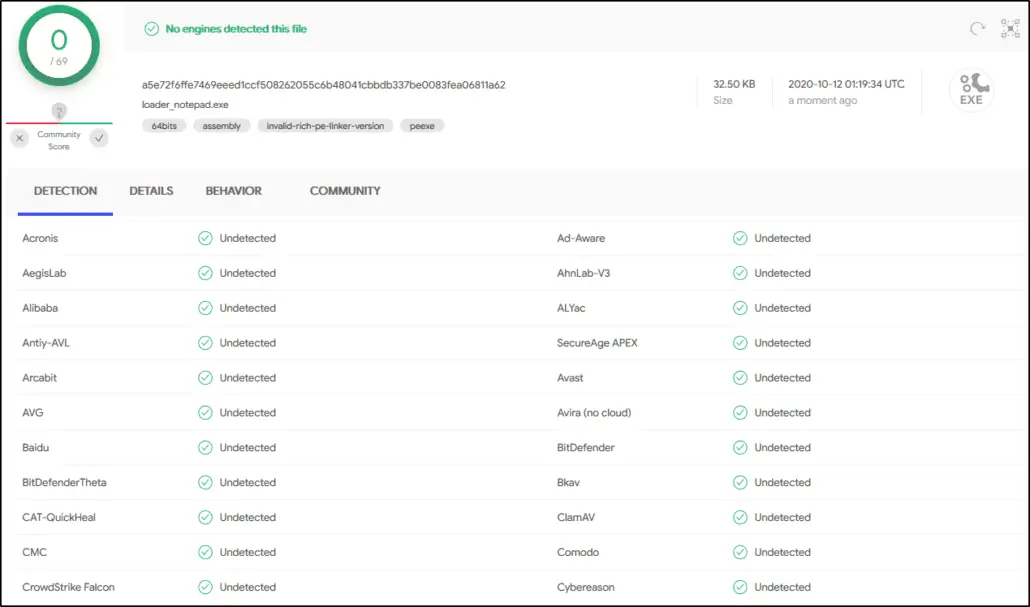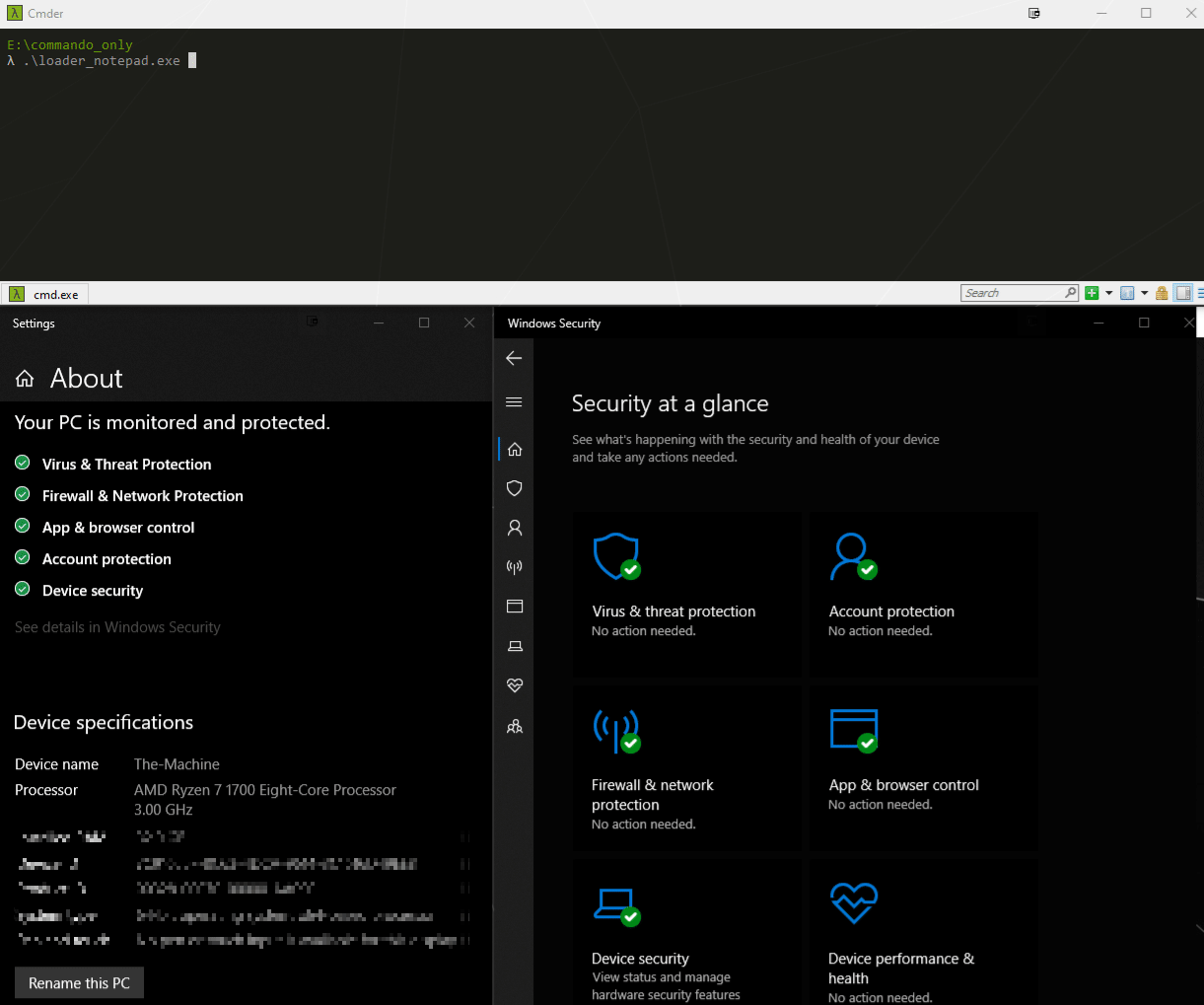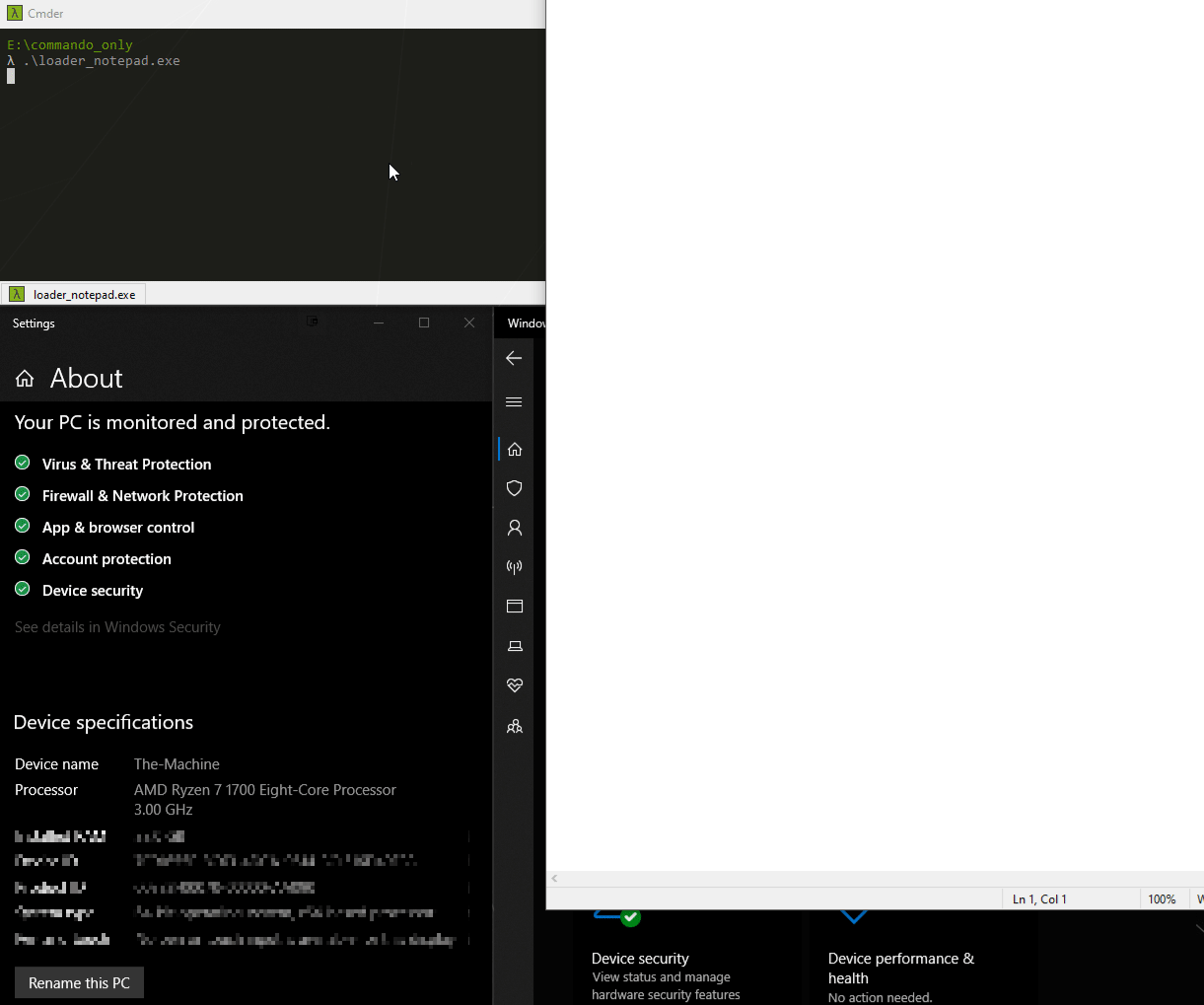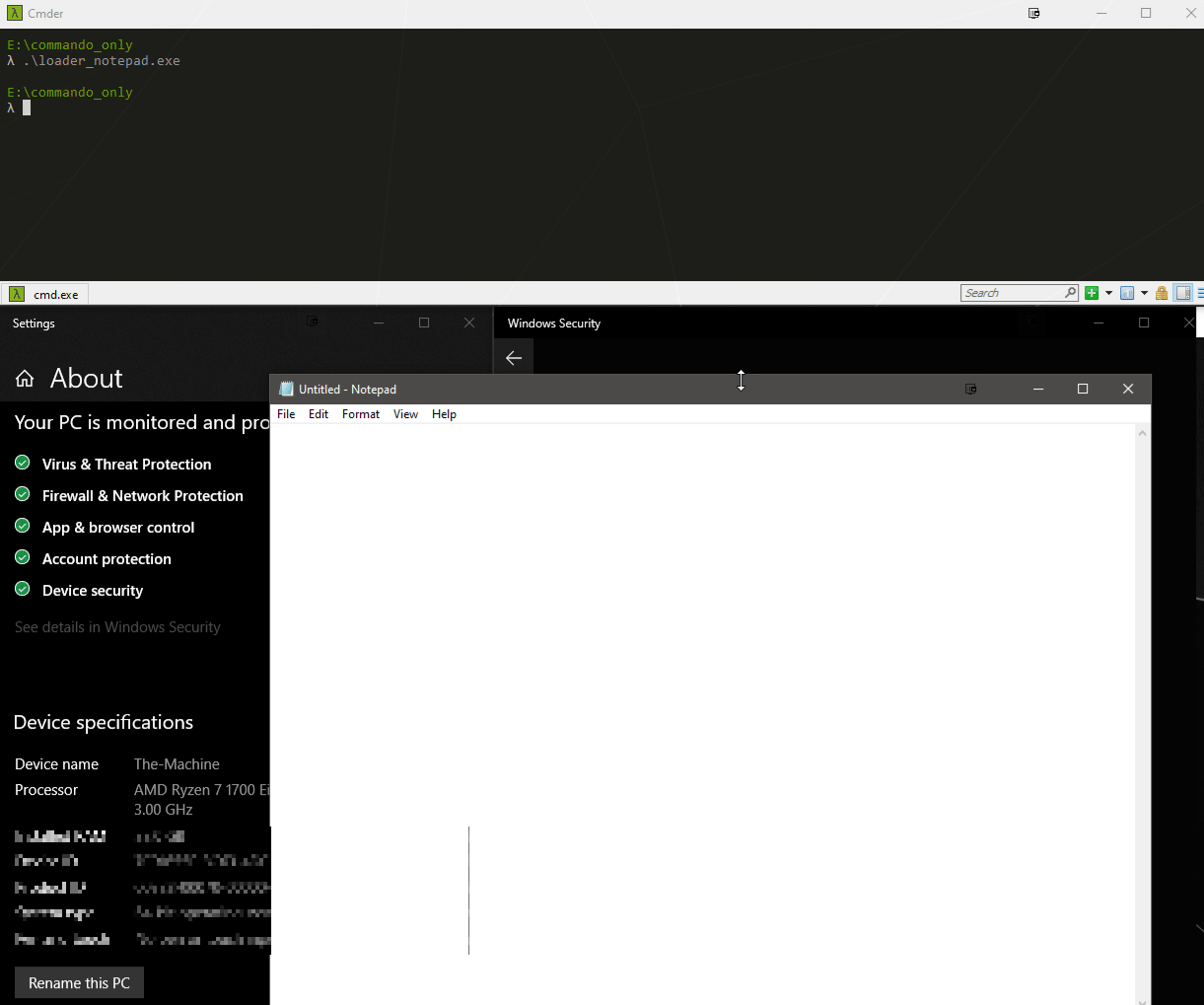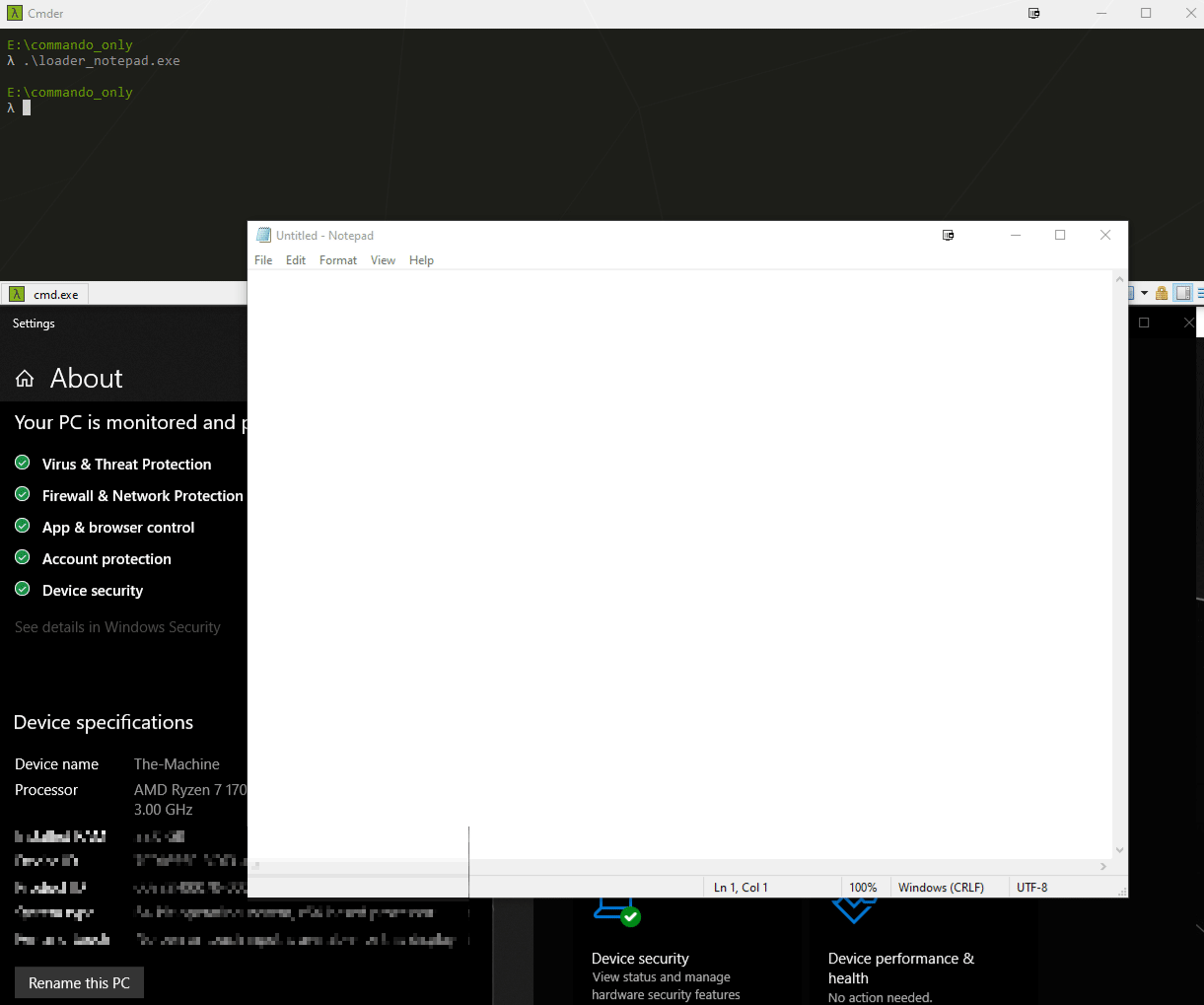
Alaris
Alaris is a new and sneaky shellcode loader capable of bypassing most EDR systems as of today (10/14/2020). It uses several known TTP’s that help protect the malware and it’s execution flow. Some of these features are:
- Shellcode Encryption (AES-CBC 256)
Within this loader is an embedded AES (128, 192, 256) (ECB, CTR, CBC) implementation. Not relying on Windows Crypto API’s or known libraries, such as Crypto++, helps limit our noise and overall footprint.
- Direct x86 Syscalls (Does not use NtDLL.dll)
- Prevents 3rd party (non-Microsoft Signed) DLL’s from hooking or injecting both the parent and child processes.
- Parent Process ID spoofing
- Overwrites it’s own shellcode after execution.
The TTPs used within Alaris are common among Red Teams and used within several C2 frameworks (Cobalt Strike for example). It is a simple and small example of how you can customize these tactics to circumvent several different detection mechanisms as well as make your code look more “legitimate” in the context of Microsoft applications.
Tutorial
Copyright (C) 2020 cribdragg3r