altprobe v1.0.2 releases: automation, continuous monitoring, orchestration, threat detection, and response
Altprobe
The repository includes Alertflex collector and installation scripts for security sensors (Suricata NIDS, Wazuh HIDS, Falco CRS).
Alertflex project is a cybersecurity solution for automation, continuous monitoring, orchestration, threat detection, and response. Alertflex works as a Security Event Manager with SOAR capabilities and designed for use in Hybrid IT infrastructure (on-premises and cloud-based).
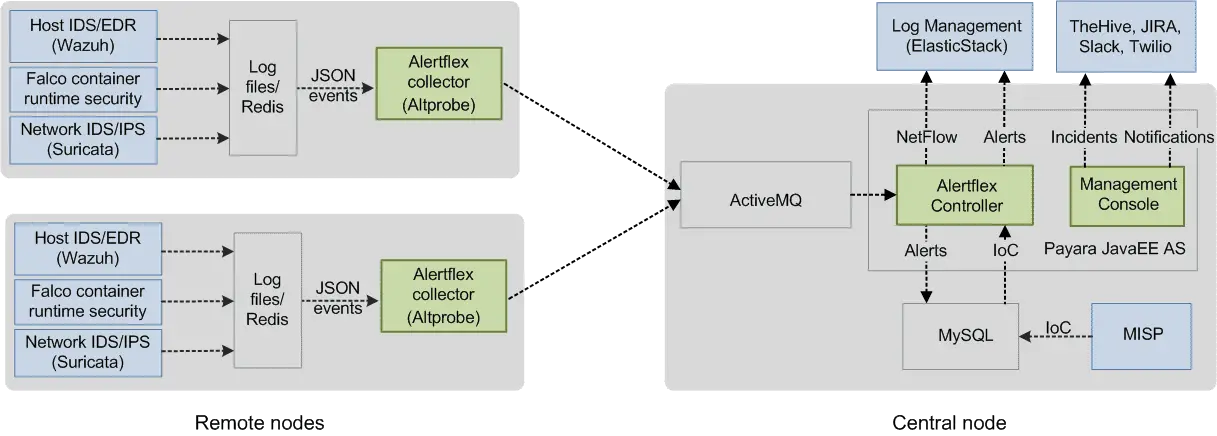
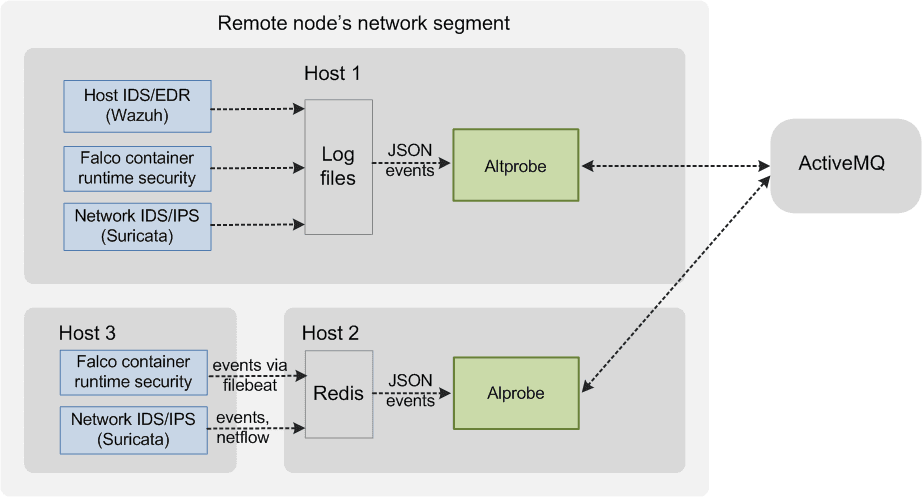
For working inside a distributed environment of Hybrid IT, the solution consists of separate software components Collector, Controller, Management Console. Alertfle Collector (Altprobe) is placed in the network domain where security sensors are installed (Container Runtime Security, Host IDS, File Integrity Monitor, Network IDS). Together with security sensors, Collector logically forms the Remote node.
Architecture
High-level design
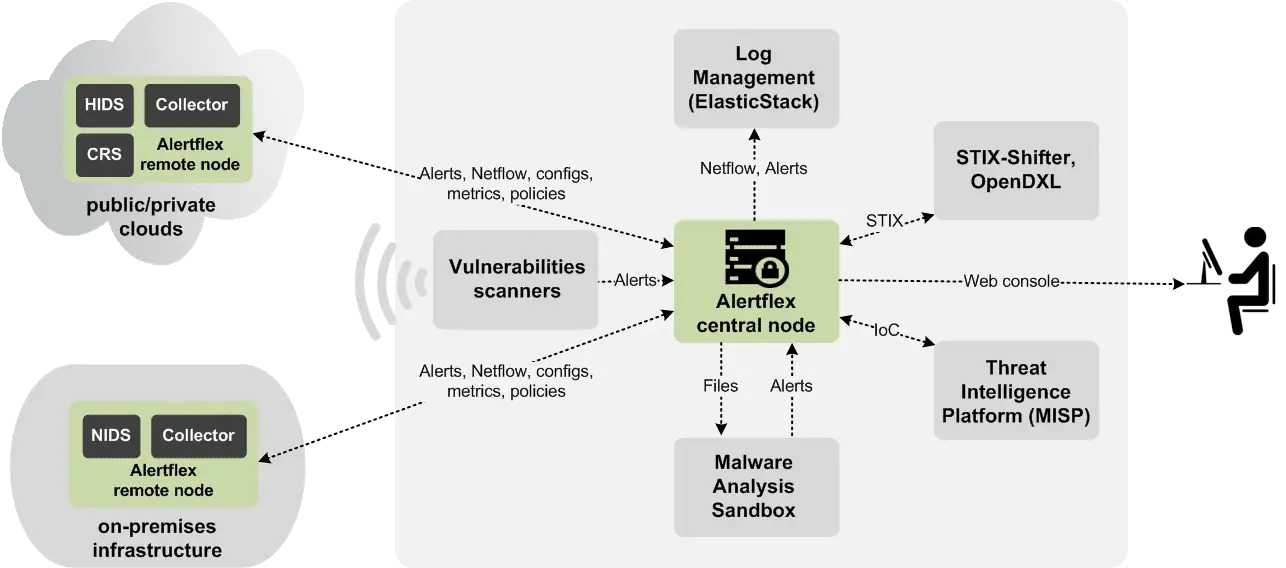
Alertflex project is a continuous security monitoring solution designed for use in Hybrid Clouds (on-premises and cloud-based IT infrastructure). By monitoring events near real-time from well-known open-source security applications, Alertflex gives companies end-to-end security visibility, implements CTI, EDR, NTA and SOAR technology stack.
Low-level design
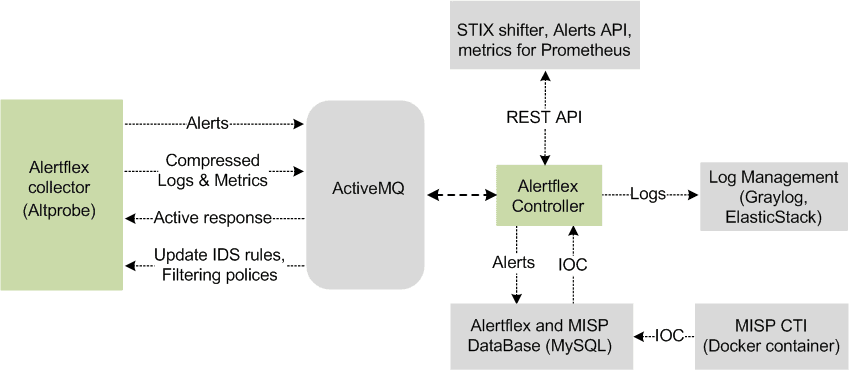
The Alertflex is based on five levels of security event management technology: Collection, Streaming, Analysis, Storage, Access. For working in a distributed environment of Hybrid Clouds, the solution consists of separate software components Collector, Controller, Management Console. Collector (Altprobe) is placed in the network domain where security sensors are installed (Container Runtime Security, Host IDS, File Integrity Monitor, Network IDS). Together with security sensors, Collector logically forms the Collector node. Alertflex Controller and Management Console make up the central node. The central node could be placed inside of monitored IT infrastructure or outside. To exchange messages between the Collector node and the Central node, the ActiveMQ or Amazon MQ message broker is used. The security of connections between nodes is implemented on the basis of support for SSL / TLS protocols built into ActiveMQ. The solution can be easily scaled from the stand-alone appliance configuration to the distributed configuration for multi-clouds.
Central node
The minimum configuration of the central node includes Alertflex Java EE applications (Controller, Management console) which work under Payara/GlassFish AS and third-party open-source components ActiveMQ, Redis, MySQL. It can be installed on the stand-alone server or virtual machine with Linux Centos 7 or Ubuntu 18.04 version. The high availability of the central node is based on cluster configurations of third-party components and microservices architecture Alertflex applications. Below shown a detailed scheme of Cnode:
Collector node
Collector node is based on the micro-segmentation model. It can include several alertflex collectors (Altprobe) and security sensors/IDS. The minimum configuration of such a node includes one installed collector on a computer/virtual machine in the node segment. The configuration can be expanded by installation several Alertflex collectors on different computers/VM inside of the node segment. It allows connecting several security sensors inside one network segment controlled by the node and using a single network and agents namespace. Alertflex collector can directly read security events from IDS logs or use the Redis server for receiving events from IDS which are installed on other hosts. See an example of such configuration below:
Install & Use
Copyright (c) 2005 – 2006 Swiss Federal Institute of Technology (ETH Zurich), Department of Computer Science (http://www.inf.ethz.ch), Christian Plattner. All rights reserved.
Source: https://github.com/olegzhr/