Attack chain and execution flow for Anatsa campaigns
Cybersecurity researchers at Zscaler ThreatLabz have uncovered a sophisticated Android banking trojan called Anatsa (also known as TeaBot) that is actively targeting Android users through seemingly harmless apps in the Google Play Store.
Anatsa is a known Android banking malware targeting applications from over 650 financial institutions, primarily in Europe. Recently, Anatsa has expanded its targets to include banking applications in the US, UK, Germany, Spain, Finland, South Korea, and Singapore. Anatsa employs a dropper technique, where the initial application appears clean upon installation but subsequently downloads a malicious payload from a command-and-control (C2) server, disguised as an innocuous application update. This method allows the malware to evade detection and be uploaded to the official Google Play Store.

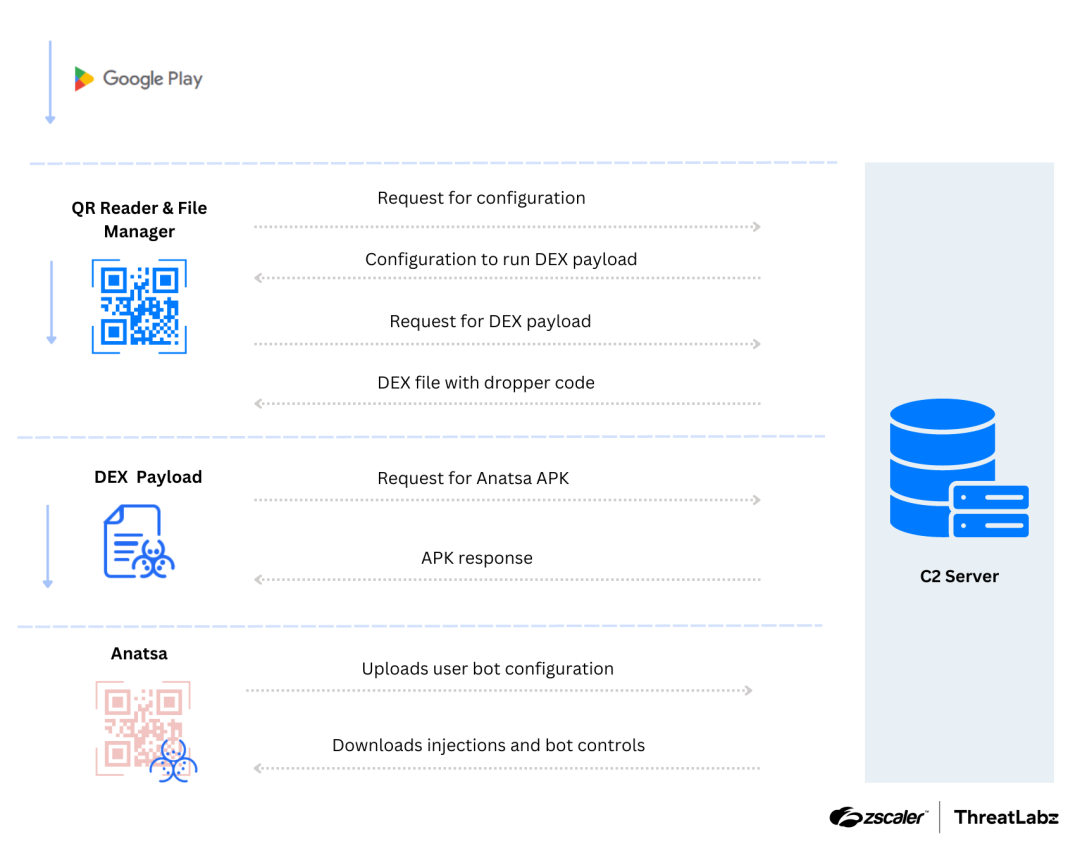
Recently, researchers identified two malicious payloads associated with Anatsa distributed via the Google Play store. These campaigns impersonated PDF reader and QR code reader applications, which collectively amassed over 70,000 installations, deceiving victims into believing these applications were legitimate. The figure below displays these PDF and QR code reader applications, which, upon installation, initiate the infection process.

Anatsa utilizes remote payloads retrieved from C2 servers to execute further malicious activities. The dropper application contains encoded links to remote servers from which the next stage payload is downloaded. This payload includes configuration files retrieved from the remote server to execute subsequent stages. Anatsa performs a series of checks to detect analysis environments and malware sandboxes before downloading the final payload.
In this campaign, Anatsa malware injected uncompressed raw manifest data into the APK and intentionally corrupted the compression parameters in the manifest file to hinder analysis. To statically analyze the payload, the headers of the ZIP file must be fixed alongside the compressed data. Once the APK is loaded, the malware requests various permissions, including SMS and accessibility options, commonly associated with mobile banking trojans. The malware conceals the final DEX payload within asset files, decrypting it during runtime using a static key embedded within the code.
Upon execution, the malware decodes all encoded strings, including C2 communication, and registers the infected device. Anatsa downloads a target list, scans the victim’s device for installed applications, and communicates this information to the C2 server. The server then provides a fake login page for the banking application, designed to deceive the user into providing their banking credentials, which are sent back to the C2 server.
The scale of this threat is alarming. Zscaler ThreatLabz has identified over 90 Anatsa-infected apps in the Play Store, collectively amassing over 5.5 million installations. What’s more, the attackers are constantly evolving their tactics, making it difficult for security measures to keep up. They even deliberately corrupt the malware’s code to hinder analysis and detection.
Analysis of Google Play Store trends reveals a disturbing pattern. While “tools” is the most frequently exploited app category, Anatsa and another potent banking trojan called Coper are also found among the malware families lurking in the store. This highlights the growing sophistication and pervasiveness of mobile threats.