CVE-2023-46604: Apache ActiveMQ Remote Code Execution Vulnerability

In the labyrinthine world of open-source software, Apache ActiveMQ stands as a beacon of reliable message brokering. As the most distinguished multi-protocol, Java-fueled message broker, ActiveMQ’s supremacy lies in its versatility. Its compatibility with an array of industry-standard protocols opens doors to a myriad of client choices, spanning numerous platforms and languages. From JavaScript, C, C++, and Python, to .Net, the gamut is comprehensive, enabling seamless integration of multi-platform applications through the omnipresent AMQP protocol.
Recently, the formidable ActiveMQ, a brainchild of the Apache Software Foundation, found itself ensnared by an XML external entity injection vulnerability. The flaw is tracked as CVE-2023-46604. This oversight predominantly sprouted from ActiveMQ’s default configuration. Post installation, port 61616 was inherently active, and its associated TcpTransport function omitted pivotal data checks. This vulnerability allows an attacker to execute arbitrary code on the victim’s system, which could give the attacker complete control over the system.
A spectrum of ActiveMQ versions bore the brunt of this exposure:
- Apache ActiveMQ < 5.18.3
- Apache ActiveMQ < 5.17.6
- Apache ActiveMQ < 5.16.7
- Apache ActiveMQ < 5.15.16
- Apache ActiveMQ Legacy OpenWire Module 5.18.0 before 5.18.3
- Apache ActiveMQ Legacy OpenWire Module 5.17.0 before 5.17.6
- Apache ActiveMQ Legacy OpenWire Module 5.16.0 before 5.16.7
- Apache ActiveMQ Legacy OpenWire Module 5.8.0 before 5.15.16
“Apache ActiveMQ is vulnerable to Remote Code Execution.The vulnerability may allow a remote attacker with network access to a broker to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath,” read the CVE-2023-46604 security advisory.
Understanding the gravity of this revelation, Apache wasted no time. They leaped into action, fortifying this vulnerability by judiciously curbing the deserialization class to only encompass subclasses of Throwable. Those utilizing the jeopardized versions are strongly recommended to promptly migrate to:
- Apache ActiveMQ >= 5.18.3
- Apache ActiveMQ >= 5.17.6
- Apache ActiveMQ >= 5.16.7
- Apache ActiveMQ >= 5.15.16
For those with a proclivity towards the technical minutiae, comprehensive details of this flaw have been disclosed.
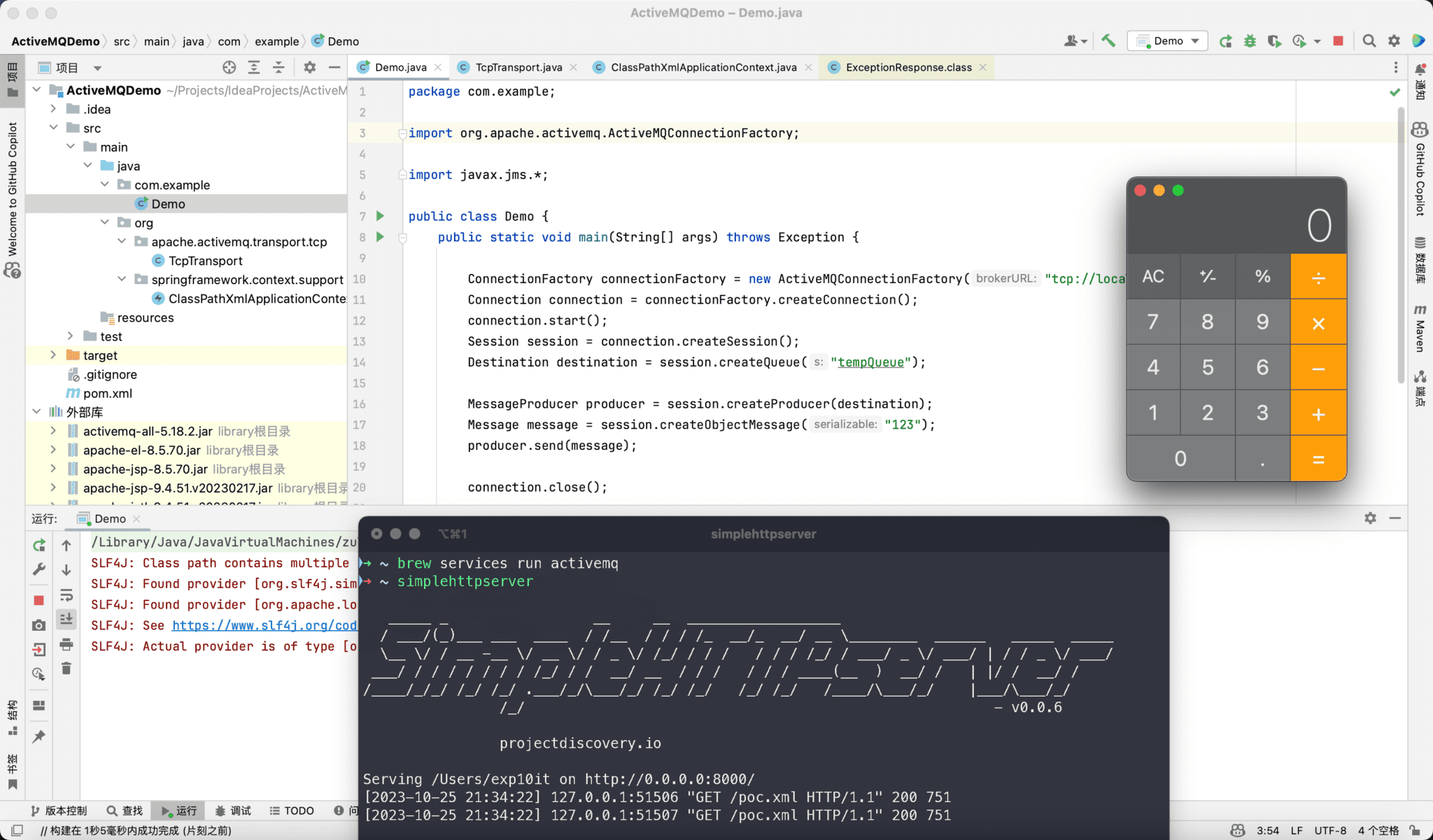
Image Credit: seebug
To gauge the potential impact of this vulnerability, Qi Anxin CERT replicated the Apache ActiveMQ remote code execution vulnerability. Their findings, encapsulated in a screenshot, bear testimony to the exigency of the situation.
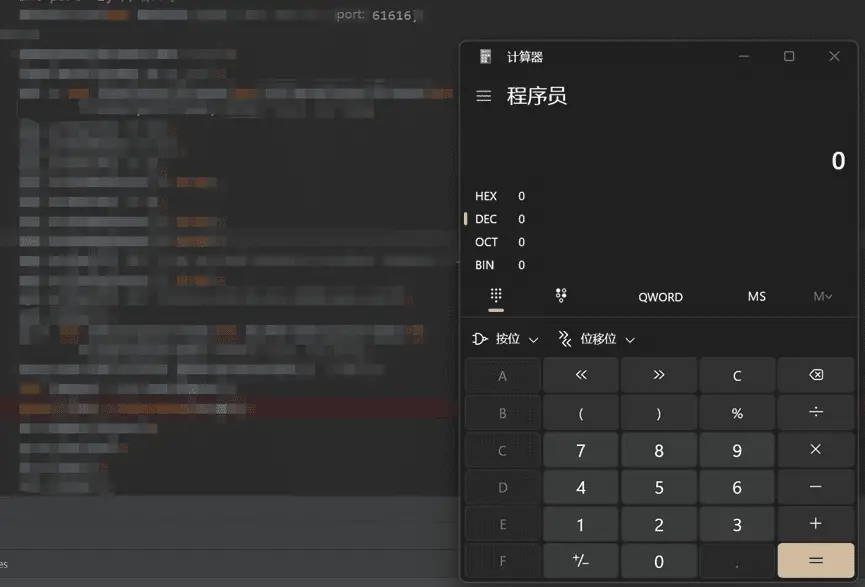
Image Credit: Qianxin
Furthermore, data gleaned from ZoomEye unveils a staggering number: 372,996 assets lie in the line of fire, predominantly situated in the territories of China, the United States, and various other nations.
Organizations can protect themselves from the Apache ActiveMQ CVE-2023-46604 vulnerability by taking the following steps:
- Update to the latest version of ActiveMQ as soon as possible.
- Block port 61616 on the firewall if ActiveMQ is not needed.
- Implement a web application firewall (WAF) to block malicious traffic.
- Use a vulnerability scanner to regularly scan for vulnerabilities in ActiveMQ and other systems.





