APT29’s Espionage Campaign Exploits WinRAR Flaw, Targets Embassies
In September 2023, the infamous Russian-linked cyber-espionage group APT29 flexed its muscle again, this time targeting embassies of several nations with a well-crafted attack. The group exploited a critical vulnerability in WinRAR (CVE-2023-38831) to gain a foothold in targeted systems. This attack highlights the ongoing threat of sophisticated state-sponsored attacks and the need for constant vigilance.
The Attack Unraveled
-
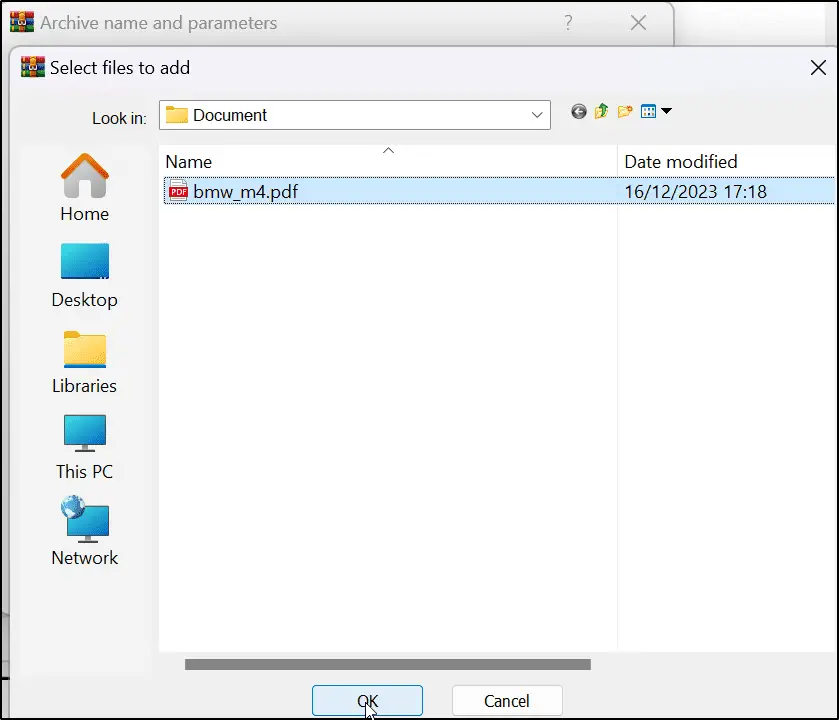
The Lure: Masquerading an internal sale of a BMW vehicle, APT29 distributed over 200 emails, embedding the RAR file that served as the Trojan horse for their intrusion.
-
The Trap: The emails contained a weaponized RAR archive. Upon opening the attached PDF detailing the vehicle, a hidden PowerShell script was surreptitiously downloaded and executed in the background.
-
The Breach: Through this initial access point, APT29 likely implanted additional tools to exfiltrate valuable data and potentially gain deeper control over the compromised networks.
Espionage in a Geopolitical Context
The targets – embassies of Azerbaijan, Romania, Greece, and Italy – were not random. This attack seems fueled by a desire for intelligence regarding Azerbaijan’s activities in the Nagorno-Karabakh conflict. The other targeted nations hold significant diplomatic ties with Azerbaijan.
The WinRAR Vulnerability
CVE-2023-38831 was a Remote Code Execution (RCE) flaw in WinRAR versions before 6.23. It allowed attackers to execute malicious code on a victim’s machine simply by getting them to open a specially crafted RAR file. Although patched in August 2023, there’s evidence of its exploitation months earlier. Other groups, like APT28, have also used it. This highlights the value of zero-day vulnerabilities for state-backed hackers.
Global Cyberwarfare Trends
This incident is a stark reminder that cyberespionage thrives during times of crisis and conflict. Sadly, these conflicts increasingly spill over into cyberspace, due to the lower costs and potential for misdirection compared to conventional warfare.
Technical Spotlight: Exploiting CVE-2023-38831
While your insightful article includes a well-explained exploitation guide, let me simplify it for broader understanding:
-
The Setup: A seemingly innocent PDF file is bundled with a hidden folder sharing the same name (plus a trailing space). Inside the folder lurks a malicious .cmd file.

Image: securitycafe
-
The Trick: When the victim opens the PDF in WinRAR, a quirk in how WinRAR extracts files makes it run the hidden .cmd script first.
-
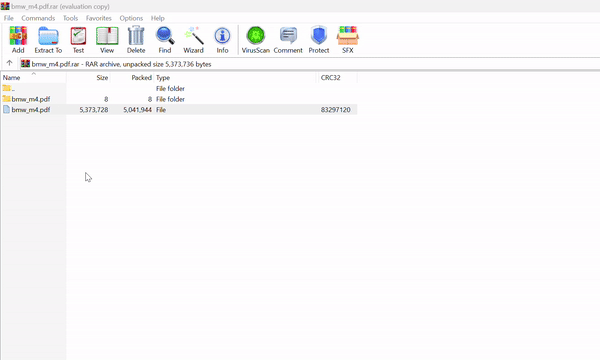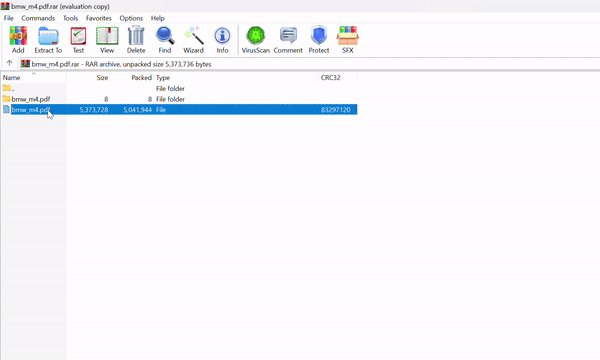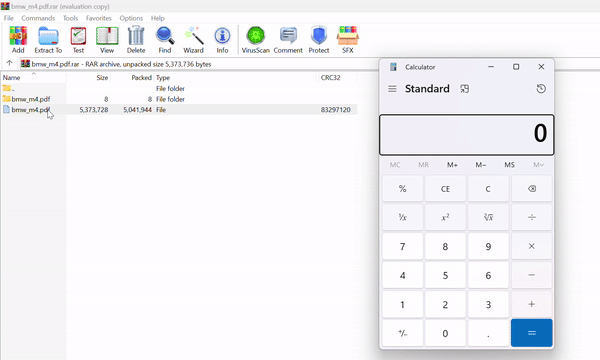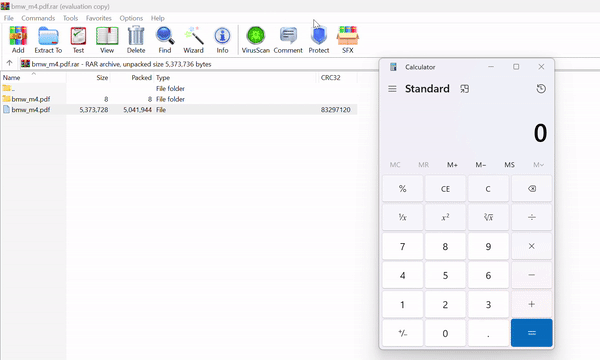
The Payload: This .cmd file could do anything from launching a simple calculator (proof-of-concept) to downloading full-fledged malware.

Image: securitycafe
The Wider Picture
The APT29 attack underscores the reality of persistent, state-backed threats. Staying protected requires not only technical measures but also awareness of geopolitical motivations driving these threat actors.