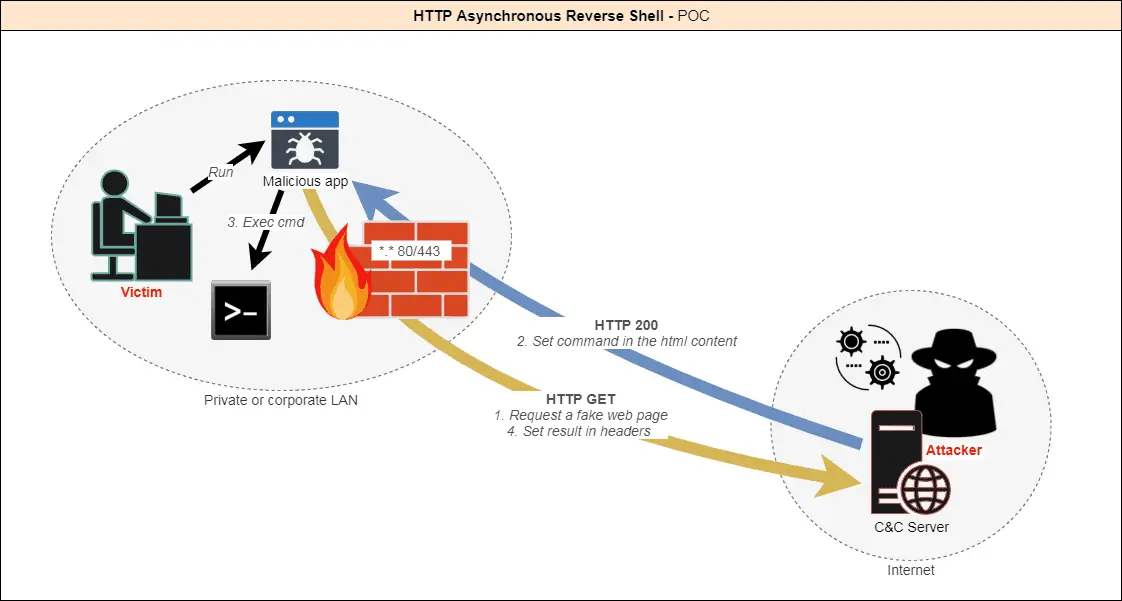
HTTP Asynchronous Reverse Shell
Why?
Today there are many ways to create a reverse shell in order to be able to remotely control a machine through a firewall. Indeed, outgoing connections are not always filtered.
However, security software and hardware (IPS, IDS, Proxy, AV, EDR…) are more and more powerful and can detect these attacks. Most of the time the connection to a reverse shell is established through a TCP or UDP tunnel.
I figured that the best way to stay undetected would be to make it look like legitimate traffic. The HTTP protocol is the most used by a standard user. Moreover, it is almost never filtered so as not to block access to websites.
How it works?
- The client app is executed on the target machine.
- The client initiates the connection with the server.
- The server accepts the connection.
Then:
-The client queries the server until it gets instructions.
-The attacker provides instructions to the server.
-When a command is defined, the client executes it and returns the result.
And so on, until the attacker decides to end the session. 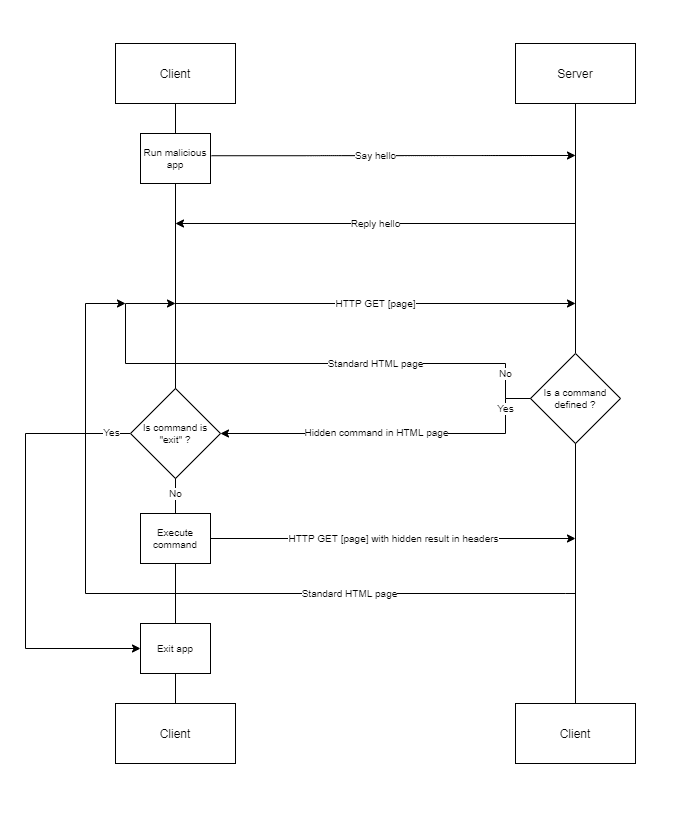
Disclaimer
This tool is only intended to be a proof of concept demonstration tool for authorized security testing. Make sure you check with your local laws before running this tool.
Features
Today, as a poc, the following functionalities are implemented:
- Fake HTTP traffic to appear as searches on bing.com.
- Commands are base64 encoded in the HTML response.
- The result of the commands is encoded in base64 as a cookie by the client.
- SSL support; by default, it is a fake bing.com certificate.
- Random delay between each customer call to avoid triggering IDSs.
- Random template is used for each response from the server.
- Re-use of the same powershell process to avoid triggering EDRs.
- Support for all Cmd and Powershell commands.
- The client displays a fake error message at startup.
- The client is hidden from the tasks manager.
- The client can be run as an administrator.
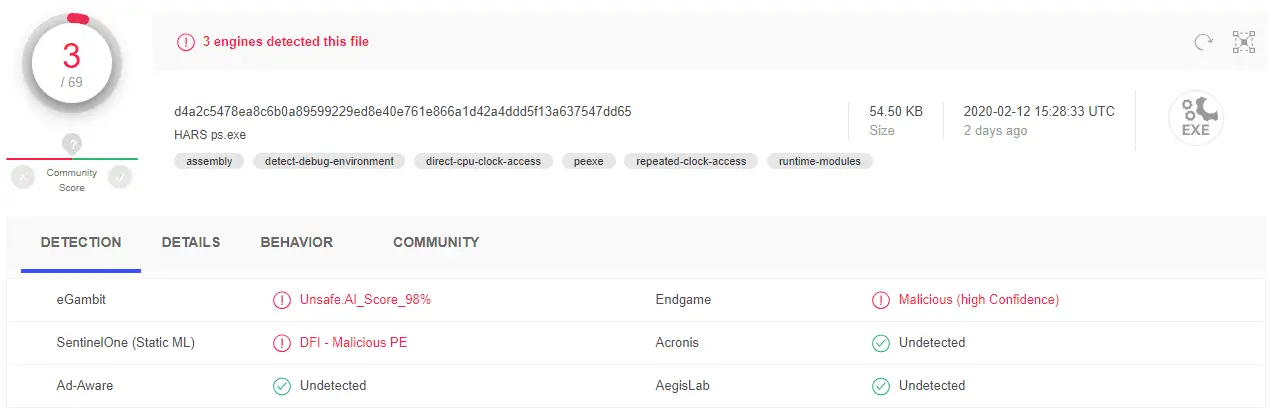
AV Detection
Only 3 out of 69 products were able to detect the client as malicious, without applying any evasive or obfuscation techniques.
Download && Use
Copyright (c) 2020 onSec-fr