AtlasC2
C# C2 Framework centered around Stage 1 operations
Atlas is based around gaining a foothold within an environment and further utilizing it to smuggle in C# (currently strictly C#) weaponry utilizing an HTTP-based implant. Isn’t exactly very OPSEC safe in its current state…at all. Currently targets only windows environments
Note: Default connection settings on the implant are set to connect to localhost on port 8080, this can be changed here
Feature
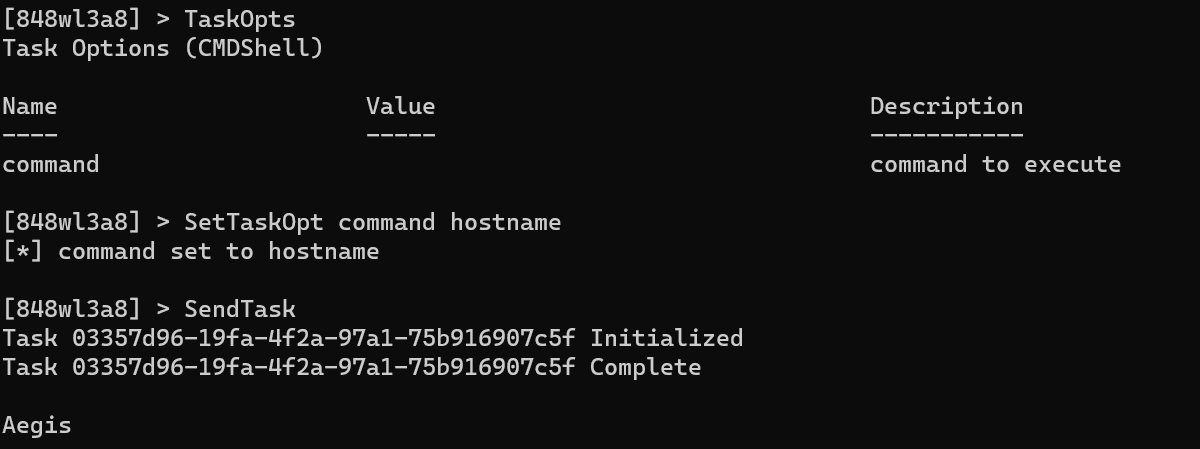
CMDShell
Atlas allows operators the option to execute shell commands just like any other modern C2. To Execute a command from cmd.exe, there’s the CMDShell task. This task isn’t exactly the most OPSEC safe out there as it opens up a new cmd.exe process and plugs in arguments passed into the command to execute.
PSShell
psshell is a bit more OPSEC safe in the sense that it leverages the Automation DLLs to create a new runspace and execute PowerShell code. In the future, there’ll be the option to send the command encoded.
Load
The Load task is broken down into a few sections. There is the Load command that will push a file as a byte array down to the implant where it will be loaded into the implant process for further operations and then the Query and Execute “sub” tasks. To use the Load task, we must first use the ByteConvert util to fetch a file (either remote or local) and convert the file to a byte array which will then be stored in the assemBytes option.
Query tasks
The Query tasks consist of AssemQuery and AssemMethodQuery. These tasks serve to return data on loaded assemblies on the implant process. AssemQuery will return all loaded assemblies located in the implant process and AssemMethodQuery will list the methods of a specified assembly.

As we can see at the very end, the NetCredHunter assembly was indeed loaded into the current implants process. Next, we’ll use AssemMethodQuery to return information on exposed methods we can use to execute methods outside this assembly’s entry point. This task takes a single option: the name of the assembly we want to return data on.
Execute tasks
The Execute tasks consist of the ExecuteAssem and ExecuteAssemMethod tasks. These tasks are what are used to execute assemblies loaded onto the implant process. ExecuteAssem will execute an assembly from the Main and ExecuteAssemMethod will allow for the execution of a specified method within an assembly. The latter task requires some modification to the C# code which will be covered in the documentation.
The NetCredHunter assembly is a “plugin” I wrote initially for SharpAtlas that searches for cached network credentials in hopes to leverage them for password spraying attacks. The entry point searches for and returns any creds if found. ExecuteAssem takes the name of the assembly and any parameters. In this case, the entry point takes no params so we’ll leave that one blank.
The other Execute task we can use is ExecuteAssemMethod. This one allows us to execute any of the methods listed in the output of AssemMethodQuery and takes a few more options. These options include the following:
- assemType – Class whose member we want to use
- assemMethod – Method we want to execute
- assemParams – Any parameters we want to pass to the executing method
Install & Use
Copyright (c) 2022 Grimmie