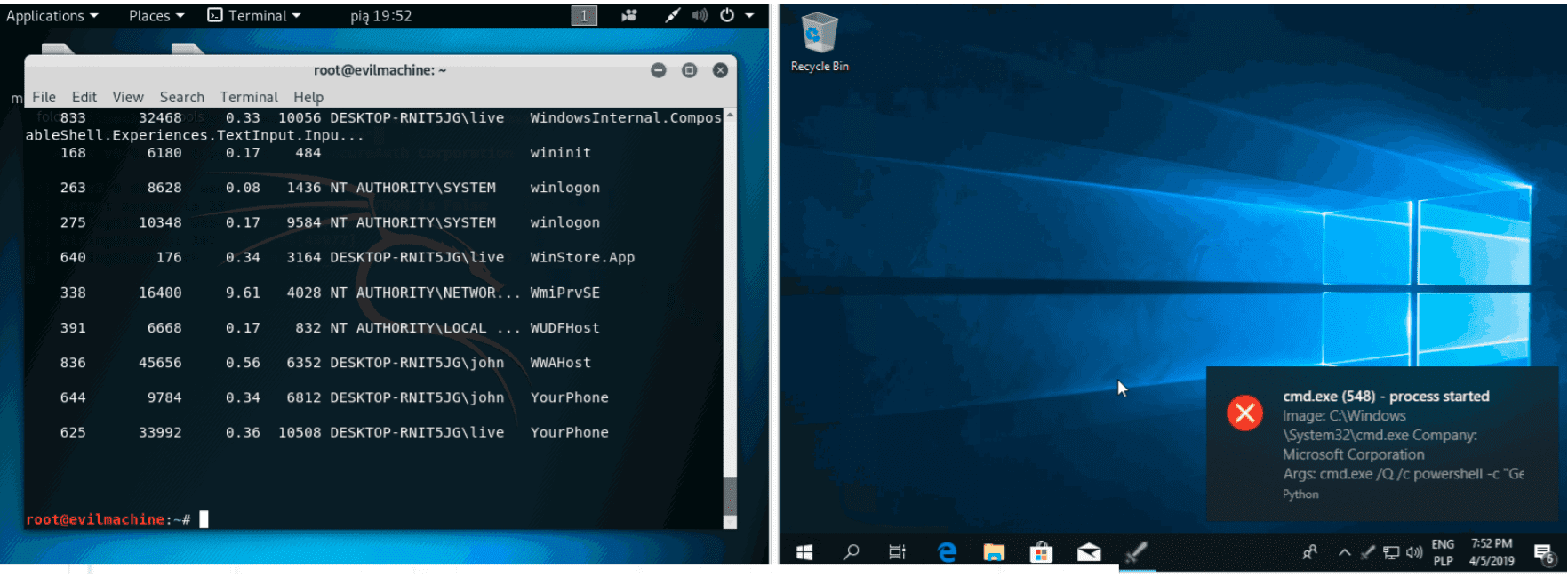
Attack Monitor
Attack Monitor is Python application written to enhance security monitoring capabilities of Windows 7/2008 (and all later versions) workstations/servers and to automate dynamic analysis of malware.

Current modes (mutually exclusive):
- Endpoint detection (ED)
- Malware analysis (on dedicated Virtual Machine)
Based on events from:
- Windows event logs
- Sysmon
- Watchdog (Filesystem monitoring Python library)
- TShark (only malware analysis mode)
How does it work?
- Alert is coming from the source (Windows Event Log, Sysmon, Filesystem change, TShark)
- Alert is checked against config\exceptions\exception.json which contains all alerts which should be ignored A) For Endpoint Detection – Predefined set of ignored alerts is delivered with software B) For Malware analysis – you need to add exceptions yourself on the live system in a clean state
- Alert is present in exception.json? Yes) Is discarded [Go to step 1] No) Go to next step
- Is learning mode enabled? (Can be enabled in tray icon, or permanently in configuration file) Yes) Alert window popup asking you if you want to ignore this alert, if yes which fields must match to consider the event as ignored? (simple comparison, substring, regex)
- If you decided to add exception for this alert – Alert is added to exceptions [Go to step 1]
- If you decided to skip exception window – Go to next step
No) Go to next step
- Alert user about capture event. Outputs:
- System tray baloon notification (Only when you are moving mouse and computer isn’t locked)
- Alert is saved to logs\.txt
Install && Use
Copyright (C) 2019 yarox24