auth_analyzer
The Burp extension helps you to find authorization bugs. Just navigate through the web application with a high privileged user and let the Auth Analyzer repeat your requests for any defined non-privileged user. With the possibility to define Parameters the Auth Analyzer is able to extract and replace parameter values automatically. With this for instance, CSRF tokens or even whole session characteristics can be auto extracted from responses and replaced in further requests. Each response will be analyzed and tagged on its bypass status.
Why should I use Auth Analyzer?
There are other existing Burp Extensions doing basically similar stuff. However, the force of the parameter feature and automatic value extraction is the main reason for choosing Auth Analyzer. With this, you don’t have to know the content of the data which must be exchanged. You can easily define your parameters and cookies and Auth Analyzer will catch on the fly the values needed. The Auth Analyzer does not perform any preflight requests. It does basically just the same thing as your web app. With your defined user roles/sessions.
GUI Overview
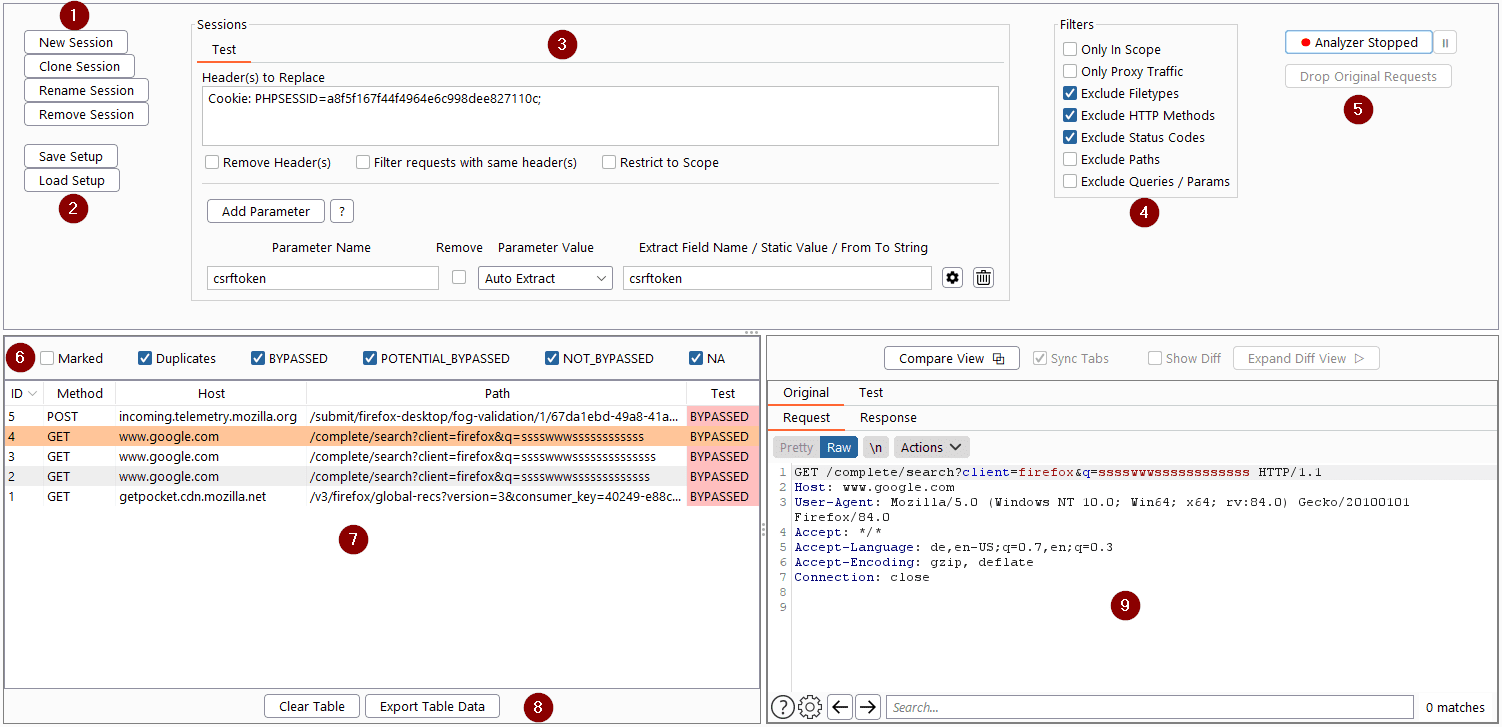
(1) Create or Clone a Session for every user you want to test.
(2) Save and load session setup
(3) Specify the session characteristics (Header(s) and / or Parameter(s) to replace)
(4) Set Filters if needed
(5) Start / Stop and Pause Auth Analyzer
(6) Specify table filter
(7) Navigate through Web App with another user and track results of the repeated requests
(8) Export table data to XML or HTML
(9) Manually analyze original and repeated requests/responses
Parameter Extraction
The Auth Analyzer has the possibility to define parameters which are replaced before the request for the given session will be repeated. The value for the given parameter can be set according to different requirements.
Auto Extract
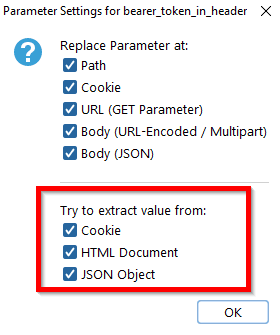
The parameter value will be extracted if it occurs in a response with one of the following constraints:
- A response with a Set-Cookie Header with a Cookie name set to the defined Extract Field Name
- An HTML Document Response contains an input field with the name attribute set to the defined Extract Field Name
- A JSON Response contains a key set to the Extract Field Name
Per default, the Auth Analyzer tries to auto-extract the parameter value from all locations. However, clicking on the parameter settings icon lets you restrict the auto-extract location according to your needs.
From To String
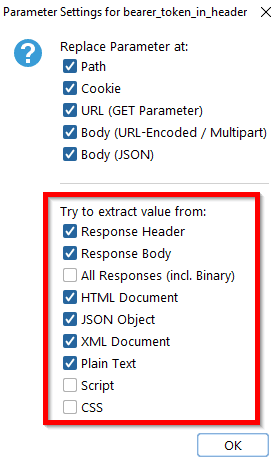
The parameter will be extracted if the response contains the specified From String and To String in a line. The From-To String can be set either manually or directly by the corresponding context menu. Just mark the word you want to extract in any response and set it as From-To Extract for the parameter you like.
By default, the Auth Analyzer tries to extract the value from the header and body at most textual responses. However, clicking on the parameter settings icon lets you restrict the From-To extract location according to your needs.
Static Value
A static parameter value can be defined. This can be used for instance for static CSRF tokens or login credentials.
Prompt for Input
You will be prompted for input if the defined parameter is present in a request. This can be used for instance to set 2FA codes.
Parameter Replacement
If a value is set (extracted or defined by the user) it will be replaced if the corresponding parameter is present in a request. The conditions for parameter replacements are:
Replacement Location
The parameter will be replaced if it is present at one of the following locations: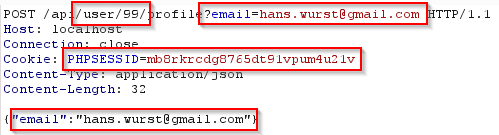
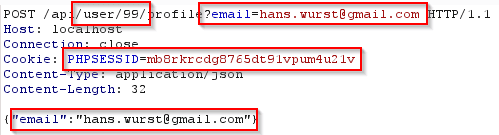
- In Path (e.g. /api/user/99/profile –> if a parameter named user is present, the value 99 will be replaced)
- URL Parameter (e.g. email=hans.wurst[a]gmail.com)
- Cookie Parameter (e.g. PHPSESSID=mb8rkrcdg8765dt91vpum4u21v)
- Body Parameter either URL-Encoded or Multipart Form Data
- JSON Parameter (e.g. {“email”:”hans.wurst[a]gmail.com”})
Per default, the parameter value will be replaced at each location. However, clicking on the parameter settings icon lets you restrict the location according to your needs.
Parameter removement
The defined parameter can be removed completely for instance to test CSRF check mechanisms.
Processing Filter
The Auth Analyzer should process two types of requests/responses:
- The response contains a value which must be extracted
- The requested resource should not be accessible by the defined session(s)
For instance, we don’t want to process a static JavaScript file because it is accessible for everyone and (hopefully) does not contain any protected data. To achieve this, we can set the following types of filters:
- Only In-Scope (only requests to the set Scope will be processed)
- Only Proxy Traffic (only requests to the “Proxy History” will be processed)
- Exclude Filetypes (specified Filetypes can be excluded)
- Exclude HTTP Methods (specified HTTP Methods can be excluded)
- Exclude Status Codes (specified Status Codes can be excluded)
- Exclude Paths (specified Paths can be excluded)
- Exclude Queries / Params (specified Queries / Params can be excluded)
Automated Response Analysis
- The Response will be declared as SAME if Both Responses have same Response Body and same Response Code
- The Response will be declared as SIMILAR if Both Responses have same Response Code and Both Responses have +-5% of response body length
- The Response will be declared as DIFFERENT in every other case
Features
- Session Creation for each user role
- Renaming and Removing a Session
- Clone a Session
- Set any amount of Headers to replace/add
- Set Headers to remove
- Set any amount of parameters to replace
- Define how the parameter value will be discovered (automatic, static, prompt for input, from to string)
- Remove a specified parameter
- Detailed Filter Rules
- Detailed Status Panel for each Session
- Pause each Session separately
- Renew Auto Extracted Parameter Value automatically
- Repeat Request by context menu
- Table Data Filter
- Table Data Export Functionality
- Start / Stop / Pause the “Auth Analyzer”
- Pause each Session separately
- Restrict session to defined scope
- Filter Requests with same header(s)
- Drop Original Request functionality
- Detailed view of all processed Requests and Responses
- Send Header(s) and/or Parameter(s) directly to Auth Analyzer by Context Menu
- Autosave current configuration
- Save to file and load from file current configuration
Changelog v1.1.13
- Drop Original Request only drops when the Request is not filtered (e.g., CORS Preflight Requests are not dropped when an OPTIONS Method filter is set)
- Improvement in File Type Filter Check
- Negative Search Function added
- Comments can now be exported as well
Download & Use
Copyright (c) 2021 Simon Reinhart