Visual workflow for data exfiltration via AWS SNS | Image: Elastic
A new report from Elastic details how threat actors are abusing Amazon Web Services (AWS) Simple Notification Service (SNS) for malicious activities, including data exfiltration and phishing campaigns. The research, born from an internal collaboration involving the use of SNS for data exfiltration in a whitebox exercise, sheds light on potential abuse techniques and detection opportunities.
AWS SNS is a web service that enables users to send and receive notifications from the cloud. Think of it as a “pub/sub” service, where users can subscribe to a digital topic and receive notifications via email, Slack, etc., when data is published to that topic. While versatile, its capabilities also make it susceptible to abuse. “This research was the result of a recent internal collaboration that required us to leverage SNS for data exfiltration during a whitebox exercise. During this collaboration, we became intrigued by how a simple publication and subscription (pub/sub) service could be abused by adversaries to achieve various actions on objectives,” the report states.
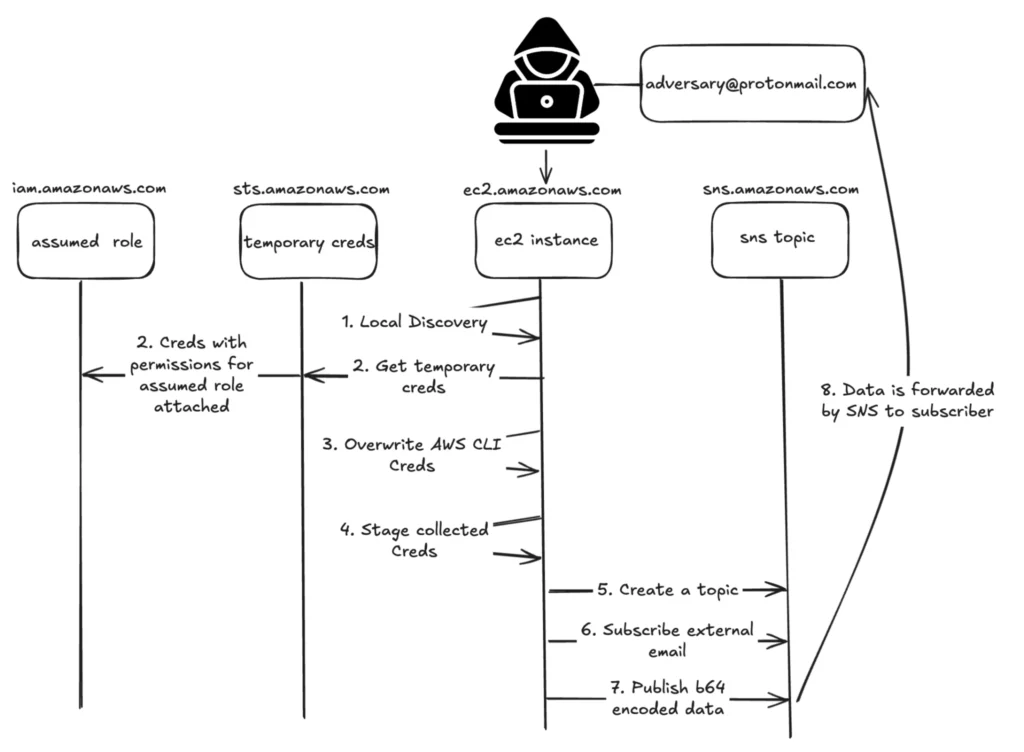
The report details how adversaries can use SNS for data exfiltration, bypassing traditional data protection mechanisms. This involves creating an SNS topic as a proxy for receiving stolen data and subscribing an external media source, such as email, to the topic. “Adversaries would then subscribe that media source to the topic so that any data received is forwarded to them,” the report explains. Once the data is packaged and published to the SNS topic, SNS handles the distribution.
The report provides an example workflow:
-
An attacker gains access to an EC2 instance and discovers sensitive data.
-
They leverage IMDSv2 and STS with the AWS CLI to obtain temporary credentials.
-
The attacker creates a topic in SNS and attaches an external email address as a subscriber.
-
Sensitive information is published to the topic, often encoded in Base64.
-
The external email address receives the exfiltrated data.
The report also highlights how compromised AWS environments with pre-configured SNS services can be exploited for smishing (SMS phishing) or phishing attacks. Attackers can leverage legitimate SNS topics and subscribers to distribute fraudulent messages, both internally and externally.
The report references a Python-based tool known as SNS Sender, which adversaries can use to conduct bulk SMS phishing campaigns. “This script enabled bulk SMS phishing campaigns by interacting directly with AWS SNS APIs using compromised AWS credentials,” the report notes. The tool leverages valid AWS access keys and secrets to establish authenticated API sessions via the AWS SDK, allowing attackers to bypass safeguards and send mass phishing messages.
The report details the challenges adversaries face, such as gaining initial access, establishing an active session, and the need for appropriate IAM role permissions. However, it also points out the advantages they have, including blending in with native AWS services, identity impersonation via IAM roles, bypassing egress monitoring, and the lack of dedicated detections for SNS abuse.
“By leveraging AWS SNS for data exfiltration, the adversary’s activity appears as legitimate usage of a native AWS flagship service,” the report states.
The report emphasizes the importance of understanding how cloud services like SNS can be abused and provides insights into detection opportunities. It also highlights the need for security best practices, such as hardening roles and access, to mitigate these threats.