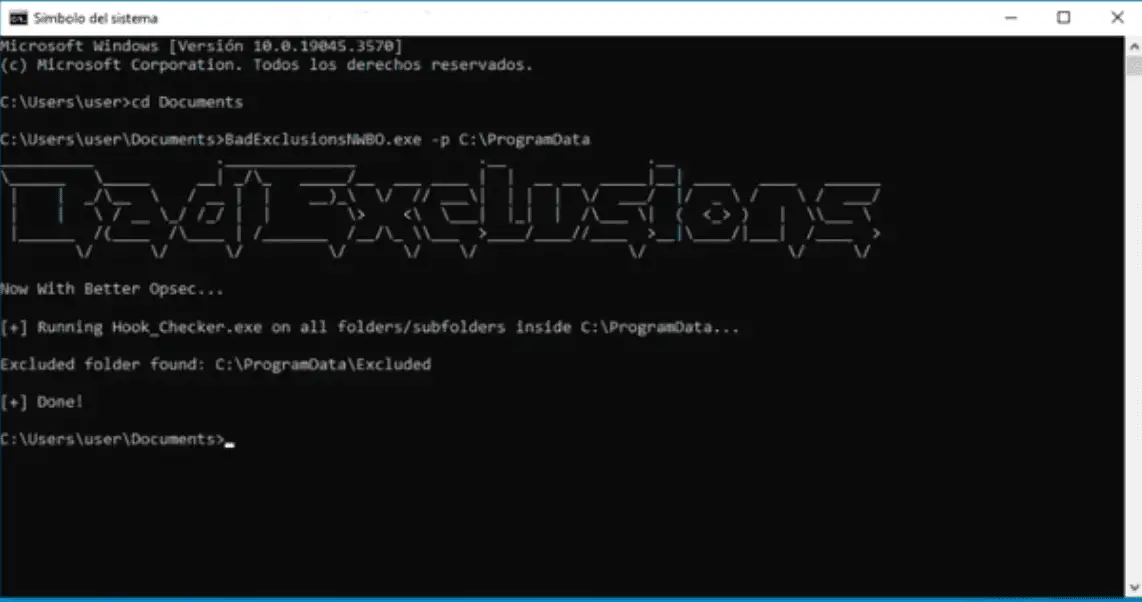
BadExclusions Now With Better Opsec
BadExclusionsNWBO is an evolution from BadExclusions to identify folder custom or undocumented exclusions on AV/EDR.

How it works?
BadExclusionsNWBO copies and runs Hook_Checker.exe in all folders and subfolders of a given path. You need to have Hook_Checker.exe in the same folder as BadExclusionsNWBO.exe.
Hook_Checker.exe returns the number of EDR hooks. If the number of hooks is 7 or less means folder has an exclusion otherwise the folder is not excluded.
Original idea?
Since the release of BadExclusions, I’ve been thinking about how to achieve the same results without creating that much noise. The solution came from another tool.
If you download Probatorum-EDR-Userland-Hook-Checker and you run it inside a regular folder and on a folder with a specific type of exclusion you will notice a huge difference. All the information is on the Probatorum repository.
Requirements
Each vendor applies exclusions differently. To get the list of folder exclusions a specific type of exclusion should be made. Not all types of exclusion and not all the vendors remove the hooks when they exclude a folder.
The user who runs BadExclusionsNWBO needs to write permissions on the excluded folder to write the Hook_Checker file and get the results.