BeaconHunter
Behavior-based monitoring and hunting tool built-in C# tool leveraging ETW tracing. Blue teamers can use this tool to detect and respond to potential Cobalt Strike beacons. Red teamers can use this tool to research ETW bypasses and discover new processes that behave like beacons.
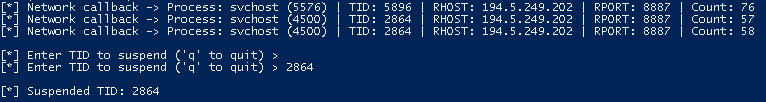
Beacon implants injected in a benign process live in a thread with a Wait:DelayExecution state (probably related to Cobalt Strike’s sleep). Find all processes that contain a thread in a Wait:DelayExecution state. Then, leverage ETW tracing to specifically monitor suspicious thread activity:
- HTTP/HTTPS callbacks
- DNS queries
- File system (cd,ls,upload,rm)
- Process termination (kill)
- Shell commands (run,execute)
Score suspicious behavior. Log, display, and take action against them.
Running BeaconHunter
- Open Powershell or CMD as an Administrator
- .\BeaconHunter.exe
MONITOR
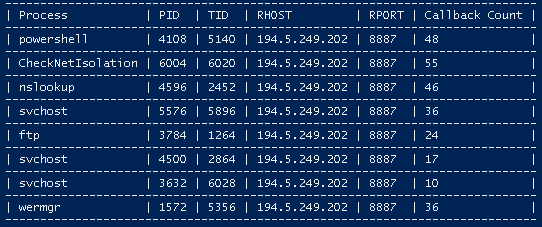
Network Beacon Score
- The score is determined by calculating the time difference between beacon callbacks (delta), then calculating the 1st derivative of the delta, and then feeding the answer to an inverse function
100/xwhere x is the 1st derivative of the delta. (Note: There is probably a better way, but it works)
IP and PORT stats
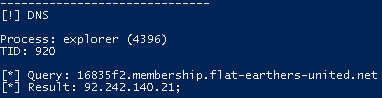
DNS Queries
Directory Change
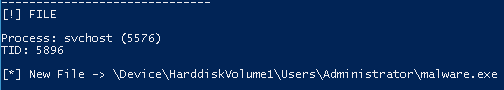
New Uploaded Files
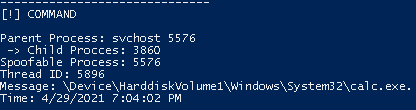
Shell Commands
- Detects PPID spoofing
ACTION
Suspend Thread ID – Manual
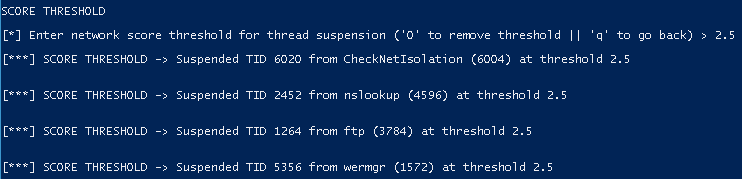
Suspend Thread ID – Automated
- Set a score threshold. If Network Beacon Scores goes above the threshold, BeaconHunter will automatically suspend the thread.
Download
Author: Andrew Oliveau (@AndrewOliveau)