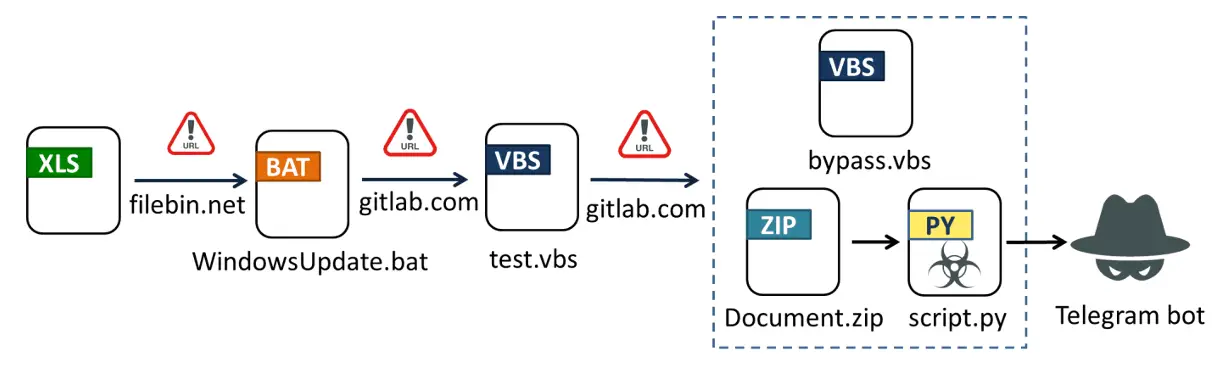
In January 2024, FortiGuard Labs uncovered a disturbing Excel document that served as the initial gateway to a sinister malware campaign. This campaign, tied to a Vietnamese-based hacking group previously identified in August and September 2023, poses a significant cybersecurity threat. This Python info-stealer malware campaign is anything but ordinary. What’s particularly troubling is the deployment of multi-stage downloaders, making detection increasingly challenging.
At the heart of this campaign is an Excel document armed with a VBA script, orchestrating the execution of a PowerShell command. The aim is to download a seemingly innocuous file, Windows Update.bat, from filebin.net. Uncover the intricacies of this devious VBA script and the cloak of obfuscation it deploys.

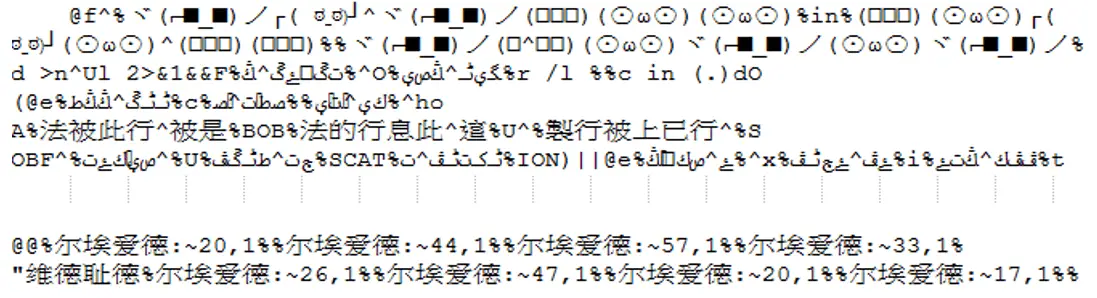
The below image reveals the secretive world of Windows Update.bat, hidden beneath layers of obfuscation. Abobus obfuscator, non-English characters, and “^” escape characters obscure its true intentions. But what’s concealed within? A malicious code designed to download and execute the next stage, test.vbs.
Test.vbs, reminiscent of an earlier campaign in August 2023, sets the stage for a triple download. Discover how it retrieves script.py (the info-stealer), Document.zip (Python 3.11 with required libraries), and bypass.vbs (the Python executor).
Unlike its predecessor from August 2023, script.py has a more focused mission – stealing browser cookies and login data. Dive into its capabilities as it targets a wide range of browsers, from mainstream to localized ones like the Cốc Cốc browser. Witness how it compresses the stolen data and dispatches it to an attacker-controlled Telegram bot.
The malware campaign draws from open platforms, offering a unique opportunity to gain insights into the hacker group. Explore repositories and files that share striking similarities with the campaign, unearthing other malware like XWorm, VenomRat, and RedLine.
The investigation unravels clues about an emerging campaign, where threat actors lure victims into enabling macros in Word documents. Discover the clever use of cookies as bait and examine how dll files are concealed within images, further highlighting the threat actor’s evolving tactics.