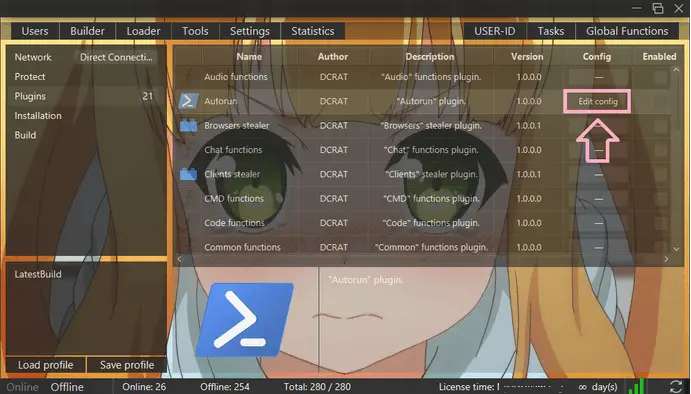
DCRat builder plugins on the attackers’ site | Image: Kaspersky Labs
Kaspersky Labs has issued a warning about a resurgence of the DCRat backdoor, a remote access trojan (RAT) that has been around since 2018. The new campaign, which has been active since the beginning of the year, is notable for its use of the Malware-as-a-Service (MaaS) model, where paid access to the backdoor is provided along with support and infrastructure setup.
The attackers are using YouTube to distribute the malware, creating fake accounts or using stolen ones to upload videos advertising cheats, cracks, gaming bots, and similar software. The video descriptions contain download links that lead to legitimate file-sharing services hosting password-protected archives containing the DCRat Trojan.
“Instead of gaming software, these archives contain the DCRat Trojan, along with various junk files and folders to distract the victim’s attention,” Kaspersky Labs said in a report.
Once installed, DCRat allows attackers to steal data, log keystrokes, access webcams, and take other malicious actions. The malware can also load extra modules to boost its functionality. Throughout its existence, DCRat has been seen with 34 different plugins, enabling a wide range of malicious activities.
Kaspersky Labs has identified at least 57 new second-level domains registered by the attackers since the start of the year, five of which already serve more than 40 third-level domains. A distinctive feature of the campaign is the appearance of certain words in the second-level domains of the malicious infrastructure, such as “nyashka”, “nyashkoon”, “nyashtyan”, etc., which are slang terms used among anime and manga fans.
Based on telemetry data, 80% of DCRat backdoor samples using such domains as C2 servers were downloaded to devices in Russia. The malware has also affected a small number of users in Belarus, Kazakhstan, and China.
Kaspersky Labs is urging users to be cautious when downloading software from the internet, especially from unofficial sources. The company also recommends using a reliable security solution to protect against malware.