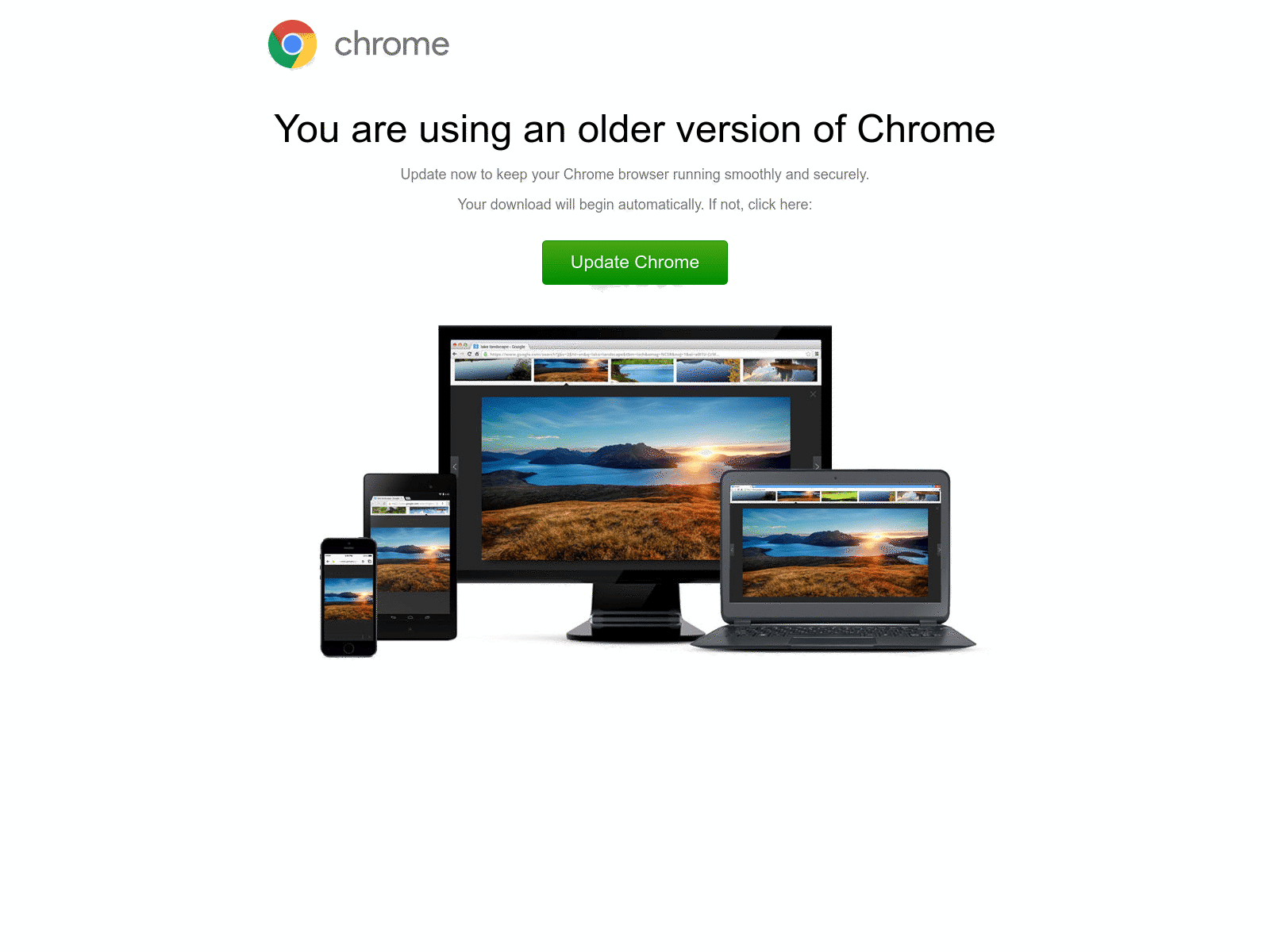
Fake Chrome update
eSentire’s Threat Response Unit (TRU) has issued a critical warning about a new wave of cyberattacks utilizing fake browser updates to deliver malicious payloads. The attacks involve injecting malicious JavaScript code into compromised webpages, redirecting unsuspecting users to a fraudulent update page that automatically downloads a ZIP archive containing malware.

The attack begins when a user visits an infected webpage containing malicious JavaScript. Upon loading the page, the script redirects the user to a fake update page, leading to the automatic download of a ZIP archive named Update.zip. This archive, hosted on Discord’s Content Distribution Network (CDN), contains several malicious files, including Update.js, which acts as the initial downloader.
In the specific incident investigated by eSentire TRU, the fake update delivered two dangerous malware strains: BitRAT and Lumma Stealer. BitRAT is a powerful remote access tool that grants attackers extensive control over infected systems, enabling them to steal sensitive data, monitor user activity, and even deploy additional malware. Lumma Stealer, on the other hand, focuses on harvesting valuable information, such as cryptocurrency wallet data, browser credentials, and other sensitive details.
The infection chain involves multiple stages, starting with the execution of a JavaScript file within the downloaded ZIP archive. This script then downloads additional PowerShell scripts that bypass security mechanisms, establish persistence, and ultimately deliver the BitRAT and Lumma Stealer payloads. The malware utilizes sophisticated techniques like AMSI bypass and reflection in .NET to evade detection and execute within legitimate processes.