
Researchers from ReversingLabs have highlighted a malicious campaign that bridges two critical ecosystems: Visual Studio Code (VSCode) Marketplace and npm, the popular JavaScript package repository.
The campaign, first observed in October 2024, began with malicious VSCode extensions disguised as legitimate tools. These extensions targeted the cryptocurrency community and later impersonated widely recognized applications like Zoom. By November, the campaign expanded to the npm ecosystem, introducing a malicious package named etherscancontracthandler. According to the report, “This proliferation changed direction,” extending the attack surface significantly.
VSCode extensions, though often overlooked as security risks, became a prime target for threat actors. The report notes that “VSCode extensions aren’t usually perceived as a potential source of compromise since they are only plugins for IDE, nothing is being added to the code base.” However, these extensions are developed using Node.js and can include npm dependencies, creating a pathway for compromise.
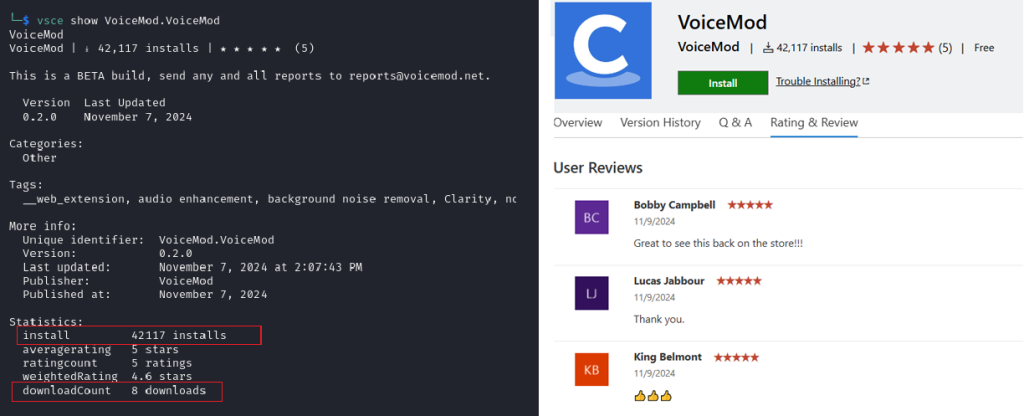
Threat actors exploited this by publishing extensions like EVM.Blockchain-Toolkit and VoiceMod.VoiceMod, which featured artificially inflated install counts and fabricated reviews. These extensions downloaded second-stage payloads from domains such as hxxps://microsoft-visualstudiocode[.]com and hxxps://captchacdn[.]com, some with suspicious TLDs like .lat and .ru.
In November 2024, the campaign’s focus shifted to npm. The etherscancontracthandler package closely mirrored the malicious VSCode extensions in functionality and design. Researchers observed that the package included obfuscated JavaScript code and downloaded payloads from the same endpoints used by the VSCode extensions. The report highlights, “ Another very similar feature was the structure of the code between malicious payloads that were obfuscated. The only difference was that one was made to be a VSCode extension, and the other as an npm package.”
Although the package was promptly removed by npm maintainers, it was downloaded approximately 350 times. As noted in the report, “The compromise of an IDE can be a landing point for further compromise of the development cycle in the enterprise.” The cascading effects of such compromises can lead to the inclusion of malicious code in larger projects, amplifying the impact.
Related Posts:
- Stealthy Cyberattack Turns Visual Studio Code into a Remote Access Tool
- Malicious VSCode extensions steal PII and enable backdoors
- Chinese APT Stately Taurus Exploits Visual Studio Code in Cyberespionage Attacks
