qiling v1.4.6 releases: Advanced Binary Emulation framework

Qiling – Advanced Binary Emulation framework
Qiling is an advanced binary emulation framework, with the following features:
- Cross-platform: Windows, MacOS, Linux, BSD
- Cross architecture: X86, X86_64, Arm, Arm64, Mips
- Multiple file formats: PE, MachO, ELF
- Emulate & sandbox machine code in an isolated environment
- Provide high-level API to setup & configure the sandbox
- Fine-grain instrumentation: allow hooks at various levels (instruction/basic-block/memory-access/exception/syscall/IO/etc)
- Allow dynamic hotpatch on-the-fly running code, including the loaded library
- True framework in Python, make it easy to build customized security analysis tools on top
Qiling is backed by Unicorn engine.
Changelog v1.4.6
- Fix ELF argv encoding by @elicn in #1303
- Qdb improvements by @ucgJhe in #1311
- added a history tracker to get coverage information about the execution of the binary by @anotherdish in #1313
- remove tab and replace with 4 spaces by @xwings in #1320
- Fix __CreateFile implmentation to include access mask and creation disposition by @kbsec in #1309
- Add interactive pipe to simulate pwntools
interactivefunction by @anotherdish in #1307 - fixed get_ins_exclude_lib not handling multiple shared objects properly by @anotherdish in #1317
- Fix improper signaling of emulation termination in gdb single step by @elicn in #1322
- Delete legacy object before reloading custom_script by @DiamondHunters in #1327
- fix #1325 by @DiamondHunters in #1326
- Fix struct packing logic associated with calls to
getdents64by @Z1pburg3r in #1334 - Improve afl_fuzz wrapper by @gnbon in #1330
- Periodic maintenance PR by @elicn in #1336
- Added qltui in setup.py by @river-li in #1354
- feat(os): add posix message queue syscalls by @chinggg in #1363
- Improved handling of export table for invalid export address and removed GandCrab workaround in GetProcAddress by @clairelevin in #1358
- Fix bug: qdb load address error by @ltlly in #1364
- Periodic maintenance PR by @elicn in #1355
- update return register accordingly for all arch by @ucgJhe in #1367
- Getting ready for 1.4.6 by @xwings in #1368
Install
git clone https://github.com/qilingframework/qiling.git
cd qiling
python3 setup.py install
Use
- Below example shows how to use Qiling framework to emulate a Windows EXE on a Linux machine.
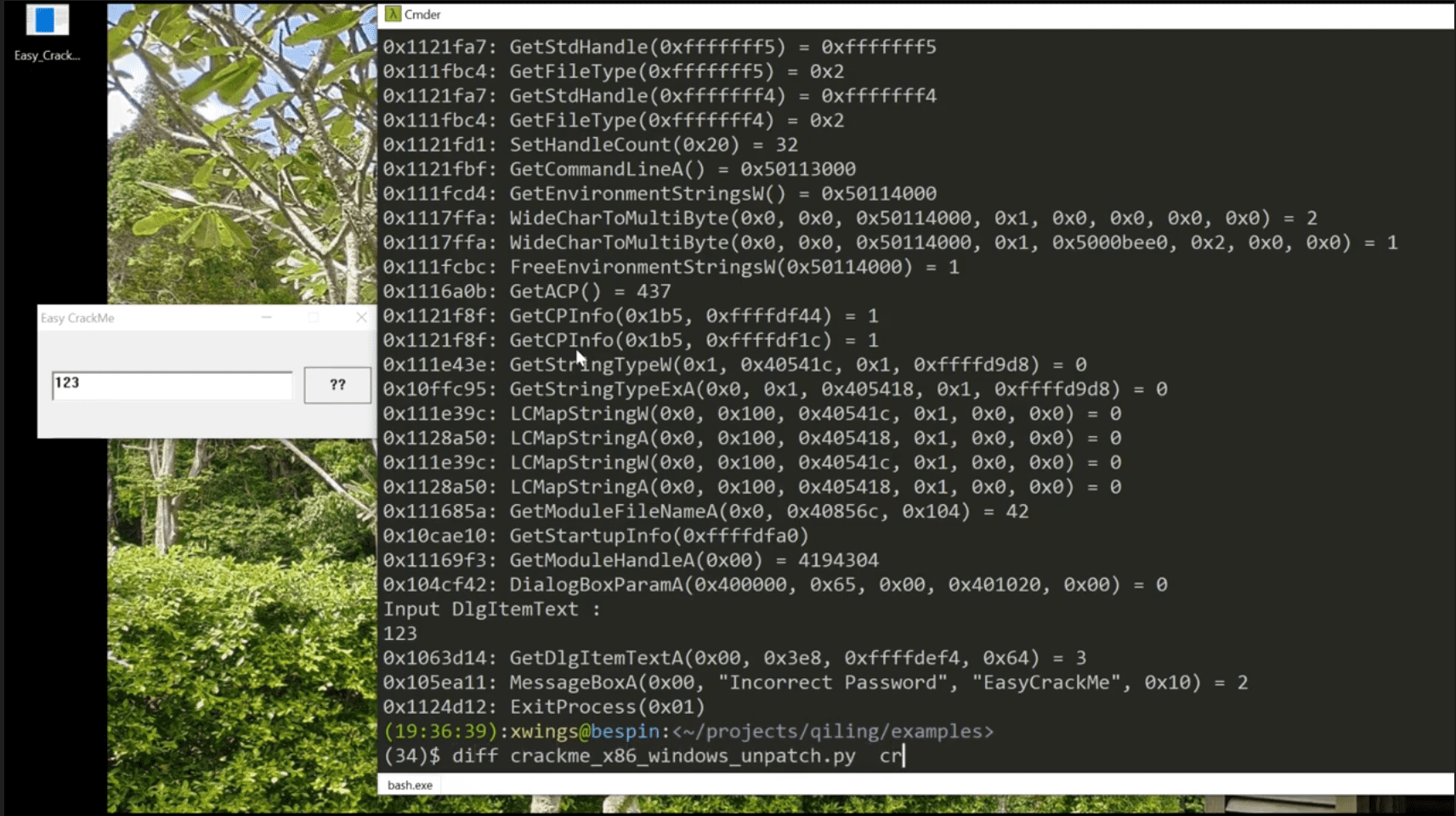
- Below example shows how to use Qiling framework to dynamically patch a Windows crackme, make it always display “Congratulation” dialog.
Qltool
Qiling also provides a friendly tool named qltool to quickly emulate shellcode & executable binaries.
To emulate a binary, run:
$ ./qltool run -f examples/rootfs/arm_linux/bin/arm32-hello --rootfs examples/rootfs/arm_linux/
To run shellcode, run:
$ ./qltool shellcode --os linux --arch x86 --asm -f examples/shellcodes/lin32_execve.asm
Demo
https://www.youtube.com/watch?v=p17ONUbCnUU
https://www.youtube.com/watch?v=gVtpcXBxwE8
Copyright (C) 2019
- kaijern (xwings) Lau kj@qiling.io
- Nguyen Anh Quynh aquynh@gmail.com
- tianze (Dliv3) Ding dddliv3@gmail.com
- bowen (w1tcher) Sun w1tcher.bupt@gmail.com
- huitao (null) Chen null@qiling.io