Zeek Network Security Monitor v6.0.1 releases: powerful network analysis framework
Zeek Network Security Monitor
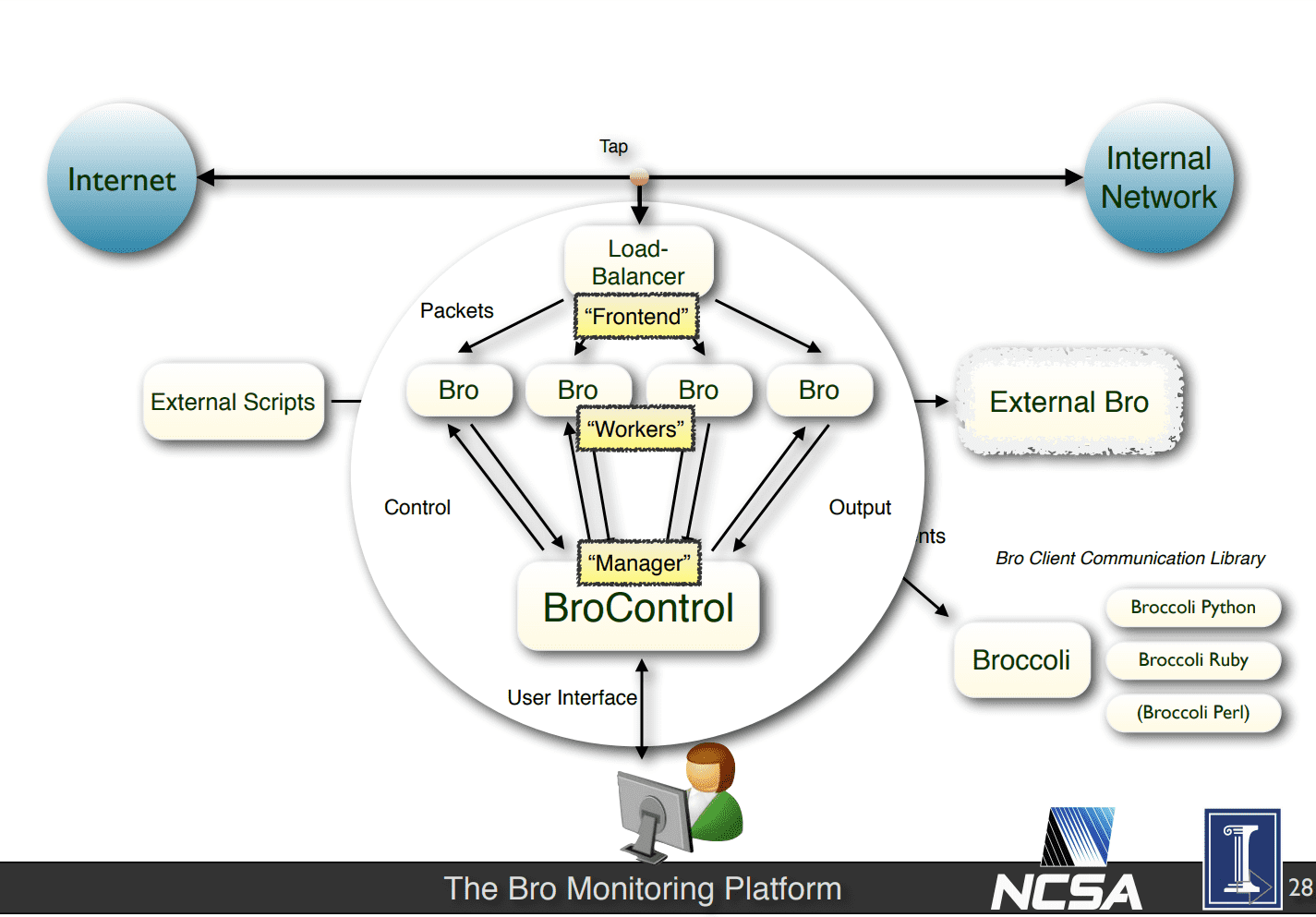
Zeek is a powerful framework for network analysis and security monitoring. It is a powerful system that on top of the functionality it provides out of the box, also offers the flexibility to customize analysis pretty much arbitrarily

Feature
-
Adaptable
Zeek’s domain-specific scripting language enables site-specific monitoring policies.
-
Efficient
Zeek targets high-performance networks and is used operationally at a variety of large sites.
-
Flexible
Zeek is not restricted to any particular detection approach and does not rely on traditional signatures.
-
Forensics
Zeek comprehensively logs what it sees and provides a high-level archive of a network’s activity.
-
In-depth Analysis
Zeek comes with analyzers for many protocols, enabling high-level semantic analysis at the application layer.
-
Highly Stateful
Zeek keeps extensive application-layer state about the network it monitors.
-
Open Interfaces
Zeek interfaces with other applications for real-time exchange of information.
-
Open Source
Zeek comes with a BSD license, allowing for free use with virtually no restrictions.
While focusing on network security monitoring, Zeek provides a comprehensive platform for more general network traffic analysis as well. Well-grounded in more than 20 years of research, Zeek has successfully bridged the traditional gap between academia and operations since its inception. Today, it is relied upon operationally by both major companies and numerous many educational and scientific institutions for securing their cyberinfrastructure.
Zeek was originally developed by Vern Paxson. Robin Sommer now leads the project, jointly with a core team of researchers and developers at the International Computer Science Institute in Berkeley, CA; and the National Center for Supercomputing Applications in Urbana-Champaign, IL.
Changelog v6.0.1
This release fixes the following security issues:
- File extraction limits were not correctly enforced for files containing large
amounts of missing bytes. Crafting files with large amounts of missing bytes
in them could cause Zeek to spend a long time processing data, allocate a lot
of main memory, and write a lot of data to disk. Due to the possibility of
receiving these packets from remote hosts, this is a DoS risk. The fix
included makes Zeek correctly enforce file size limits. We also added a new
option (default_limit_includes_missing) which allows to customize the behavior
when encountering large amounts of missed bytes in file. This issue was
discovered by Luca Cigarini. - Sessions are sometimes not cleaned up completely within Zeek during shutdown,
potentially causing a crash when using the -B dpd flag for debug logging. This
is low priority because it only happens at shutdown and only when using that
flag. The fix included is to reorder shutdown to cleanup all the sessions
prior to tearing down the analyzers. - A specially-crafted HTTP packet can cause Zeek’s filename extraction code to
take a long time to process the data. Due to the possibility of receiving
these packets from remote hosts, this is a DoS risk. The fix included adjusts
the regular expression used in the extract_filename_from_content_disposition()
script function to more-correctly match the data. - A specially-crafted series of FTP packets made up of a CWD request followed by
a large amount of ERPT requests may cause Zeek to spend a long time logging
the commands. Due to the possibility of receiving these packets from remote
hosts, this is a DoS risk. The fix included is to prevent logging of pending
commands for FTP packets. - A specially-crafted VLAN packet can cause Zeek to overflow memory and
potentially crash. Due to the possibility of receiving these packets from
remote hosts, this is a DoS risk. The fix included is to add some additional
length checking to the VLAN analyzer.
This release fixes the following bugs:
- Fixed a base64 decoding issue with the authorization field of HTTP request
headers that was sometimes causing Zeek to output error messages. Thank you
to GitHub user @progmboy for reporting and providing a fix for this issue. - Ensure that Zeek builds use the internal version of Spicy instead of external
installations, unless specifically configured for that mode. - Support was added for
switchfields when exporting Spicy types to Zeek. - A number of fixes were added to protect against potential unbounded state
growth with the SMB and DCE-RPC analyzers. SMB close requests will properly
tear down an related DCE-RPC analyzers. A newSMB::max_dce_rpc_analyzers
script variable was added that allows finer control of how many DCE-RPC
analyzers are allowed to be created per SMB connection. Thanks to Zeek Slack
user Takomi Sugawara for reporting this issue. - Fixed a regression in the UDP and TCP analyzers that was causing more data
than necessary to be forwarded to the next analyzer in the chain. Thanks to
Zeek Slack user Hiep Long Tan for reporting this issue. - A connection’s value is now updated in-place when its directionality is
flipped due to Zeek’s heuristics (for example, SYN/SYN-ACK reversal or
protocol specific approaches). Previously, a connection’s value was discarded
when flipped, including any values set in anew_connection()handler. A
newconnection_flipped()event is added to allow updating custom state in
script-land. - Fixed undefined symbols being reported from Spicy when building some of the
binary packages for Zeek. - Loading
policy/frameworks/notice/community-id.zeeknow also automatically
community ID logging. In the past, loading the script had no effect unless
policy/protocols/conn/community-id-logging.zeekwas loaded before. This
was fairly unusual and hard to debug behavior. - Spicy no longer registers an extra port for every port registered in a
plugin’s .evt file. - Timeouts in DNS resolution no longer cause uncontrolled memory growth.
- Fix check to skip DNS hostname lookups for notices that are not delivered via
email inpolicy/frameworks/notice/extend-email/hostnames. Due to that
policy script being loaded in the Zeek’s defaultlocal.zeek, this
previously caused unneeded DNS lookups for every generated notice instead of
just those delivered via email.
Download & Install & Tutorial
Copyright (c) 1995-2016, The Regents of the University of California through the Lawrence Berkeley National Laboratory and the International Computer Science Institute. All rights reserved.





