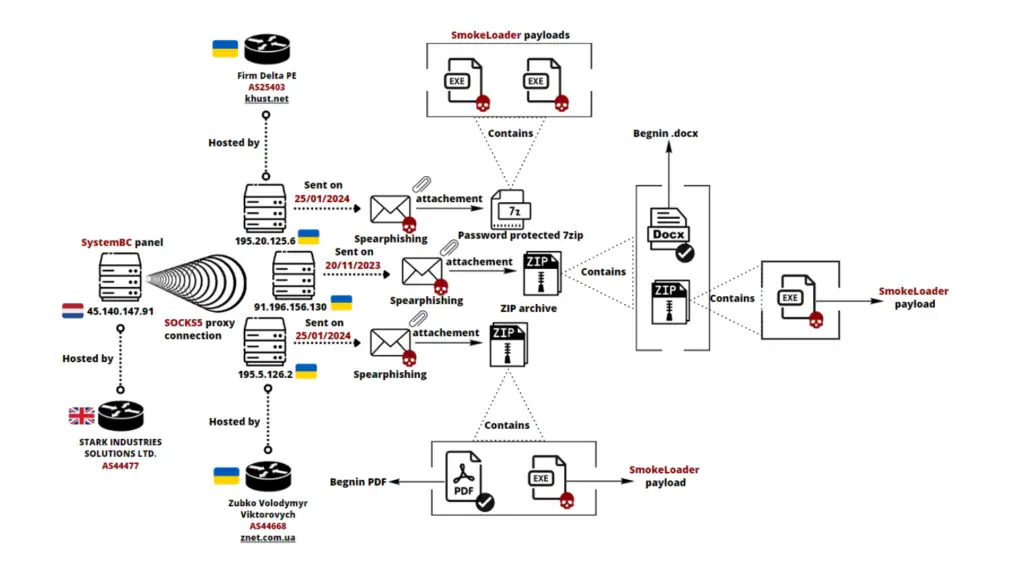
Layout of UAC-0006’s spam infrastructure by the end of 2023 and early 2024 | Image: Intrinsec
A recent report by Intrinsec has uncovered the activities of Russia-aligned intrusion sets, UAC-0050 and UAC-0006, which have been actively involved in financially and espionage motivated spam campaigns. These campaigns, observed in January and February 2025, targeted various entities worldwide, with a strong focus on Ukraine.
According to Intrinsec analysts, these groups are waging a campaign that blends cyber espionage, financial theft, and psychological warfare—primarily aimed at Ukraine and its allies. UAC-0050, described by CERT-UA as a “mercenary group associated with Russian law enforcement agencies,” has not only attempted financial theft but also launched destabilizing psychological operations.
“UAC-0050 operators are mainly focused on financial theft,” the report notes, referencing over 30 attempts to siphon millions from Ukrainian businesses via forged banking transactions.
Yet, the scope of their campaigns has expanded. In December 2024, emails containing bomb threats and calls for political violence were sent to institutions in Ukraine, Switzerland, Germany, Poland, and France. These emails were signed by a fictitious entity known as the Fire Cells Group—a psychological operation likely orchestrated by Russian intelligence operatives.
What enables these campaigns to persist is the resilience of their infrastructure. Both UAC-0050 and UAC-0006 rely heavily on bulletproof hosting providers—shadowy networks that actively enable cybercriminal activity by ignoring takedown requests and legal notices.
“IPs from Global Connectivity Solutions LLP… are routed by Stark Industries (AS44477),” the report states, linking the same infrastructure to ransomware operations by Black Basta, Cactus, and RansomHub.
Intrinsec traces much of this infrastructure back to front companies in Seychelles and offshore shell entities, including those linked to the infamous Zservers, recently sanctioned for their ties to LockBit ransomware.
UAC-0050’s malware delivery chain is a case study in adaptability. The report documents campaigns that used malware such as sLoad, Remcos, LiteManager, and NetSupport Manager, each paired with phishing lures—often masquerading as government notifications or legal documents.
One campaign impersonated the Ukrainian logistics firm Nova Pochta and embedded malware in multi-layered password-protected archives. In another, a fake Google Drive PDF linked to a Remcos payload hosted on Bitbucket, which communicated with command-and-control (C2) servers tied to previous QakBot and RansomHub activity.
Perhaps the most disturbing shift in tactics has been UAC-0050’s descent into psychological operations. The group sent threatening emails with fake bomb threats, detailed detonation plans, and photos of weaponry. Other emails threatened violence against public officials, including French President Emmanuel Macron, as part of a campaign to spread fear, disrupt public services, and sow political unrest.
In contrast, UAC-0006 continues to focus on financial motives, primarily targeting Ukrainian accountants and financial institutions with SmokeLoader malware. Their campaigns, however, use similarly resilient infrastructure, including IPs hosted on Stark Industries, Virtualine, and Railnet LLC. They too have exploited vulnerabilities such as CVE-2025-0411, a 7-Zip zero-day, to bypass Windows protections during phishing campaigns.
The 2025 operations of UAC-0050 and UAC-0006 underscore a dangerous convergence of cybercrime, state-backed espionage, and psychological warfare. These intrusion sets continue to adapt and persist by leveraging a complex network of bulletproof hosts, shell companies, and disinformation campaigns.
With ransomware affiliates, state actors, and disinformation warriors increasingly sharing infrastructure, the line between cybercrime and nation-state operations has never been blurrier—or more dangerous.
Related Posts:
- Financially Motivated Hackers UAC-0006 Resurface with New Attacks Targeting Ukraine
- UAC-0050 Phishing Steals Data from Ukrainian & Polish Agencies
- Unmasking UAC-0006: Group Behind Smoke Loader Backdoor
- RemcosRAT in Action: UAC-0050’s Stealth Campaign Against Ukraine
- The DaVinci Group: Russia’s Cyber Mercenaries Target Ukraine