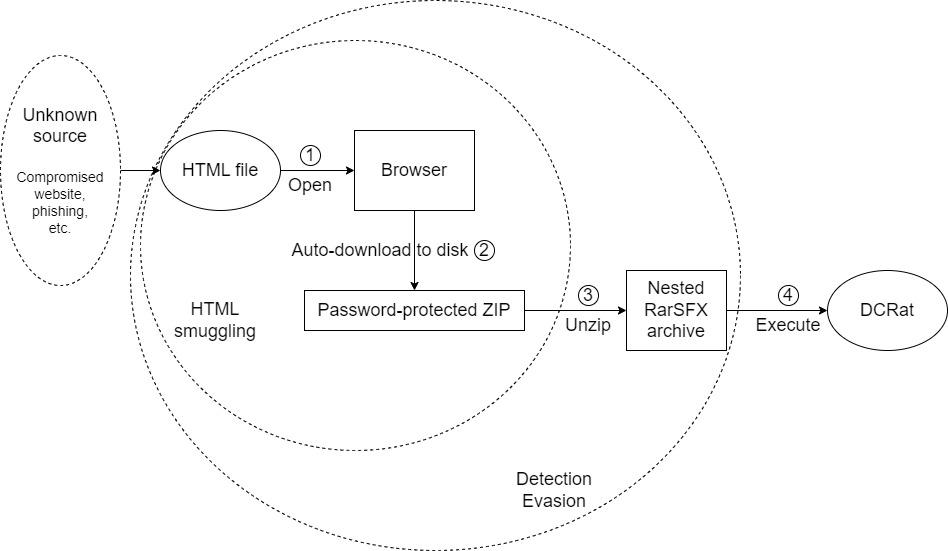
DCRat execution flow | Image: Netskope
A recent report from the Netskope team reveals that the modular remote access trojan (RAT), DCRat (also known as Dark Crystal RAT), is being deployed using a relatively new and evasive technique—HTML smuggling. This method has become increasingly popular for distributing malware, allowing threat actors to bypass traditional security defenses. While HTML smuggling has been previously linked to malware like Azorult and Pikabot, this is the first time DCRat has been observed using this approach.
Since 2018, DCRat has been a significant player in the malware-as-a-service (MaaS) space, allowing cybercriminals to rent out its capabilities to launch attacks. Written in C#, this RAT provides a comprehensive range of functionalities, including keystroke logging, file exfiltration, shell command execution, and credential theft. Historically, DCRat has been delivered through compromised websites, malicious attachments, or through popular platforms like Signal and Cobalt Strike Beacons.
HTML smuggling is a technique that embeds malicious payloads within an HTML file, which is then sent to the victim via email or other communication channels. Upon opening the HTML file in a web browser, the payload is dynamically transformed back into its original form. The payload may be delivered through a variety of obfuscation techniques, such as compression or encryption, helping it evade security mechanisms like firewalls and sandboxing.
In the case of this DCRat campaign, the HTML file impersonated Russian-language media applications such as TrueConf and VK Messenger, likely targeting Russian-speaking users. Once the file is opened, it automatically downloads a password-protected ZIP archive to the victim’s machine. To further evade detection, the HTML file provides the password (“2024”) needed to decrypt the archive, which prevents security solutions from inspecting the contents of the ZIP file.
The smuggling code used in these attacks appears to have been derived from an open-source GitHub repository known as BobTheSmuggler.
The initial ZIP archive delivered via HTML smuggling contains a self-extracting RAR file (RarSFX), which further includes a batch script and another password-protected archive. Once executed, the batch script automatically decrypts and launches the embedded archive, initiating the final DCRat payload without requiring additional user input.
The payload is packed with tools like ENIGMA and VMProtect to prevent reverse engineering, and analysis of the RAT revealed similarities with previous DCRat samples dating back to May 2022. These resemblances suggest that the attackers are reusing older builds of the malware while incorporating new delivery techniques.
By embedding the DCRat payload within multiple layers of password-protected archives, the attackers ensure that traditional security solutions, which may scan attachments, are unable to detect the actual malware. While phishing campaigns that use password-protected attachments are not new, the reliance on HTML smuggling and nested RAR archives adds an extra layer of complexity, making it harder to identify and block the malicious payload before it reaches the user’s system.
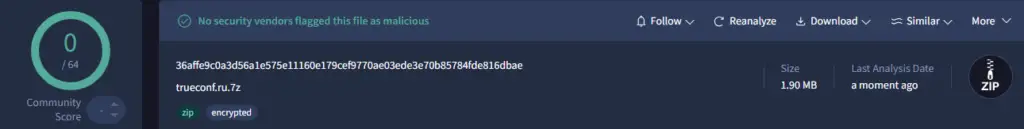
In some cases, security tools flagged the final payload as malicious, but the initial ZIP file itself had zero detections on platforms like VirusTotal. This shows how effective password protection can be in evading detection.
Related Posts:
- Vulnerable Microsoft SQL Server are being targeted by hackers
- Flax Typhoon Botnet Exploits 66 Vulnerabilities: A Global Threat to Critical Infrastructure