LOLBITS
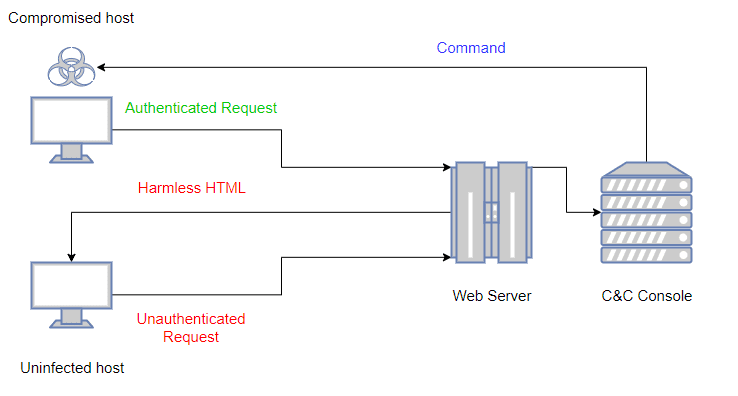
LOLBITS is a C# reverse shell that uses Microsoft’s Background Intelligent Transfer Service (BITS) to communicate with the Command and Control backend. The Command and Control backend is hidden behind an apparently harmless flask web application and it’s only accessible when the HTTP requests received by the app contain a valid authentication header.
LOLBITS is composed of 3 main elements:
- The C# agent that is in charge of executing the commands in the compromised host, sending back the output to the C&C server once the process is done.
- The flask web application that acts as a dispatcher. This element is the one that allows hiding the C&C infrastructure behind a harmless website at the same time that supplies the new commands to the agent when an authenticated request is received.
- The C&C console used to control the agent.
In order to deny proxies content inspection, all the relevant content sent between the agent and the C&C server is encrypted using RC4 with a preshared secret key. A high-level diagram of the infrastructure behavior would be as it’s shown in the following diagram:
To avoid that the Blue Team could reproduce some of the old requests and discover the C&C infrastructure, each authentication header is generated randomly and is valid only for one single cycle (a cycle is composed of a POST request followed by a GET request). Old authentication headers will be ignored and the harmless website will be displayed for those requests.
Install & Use
Copyright (C) 2020 Kudaes