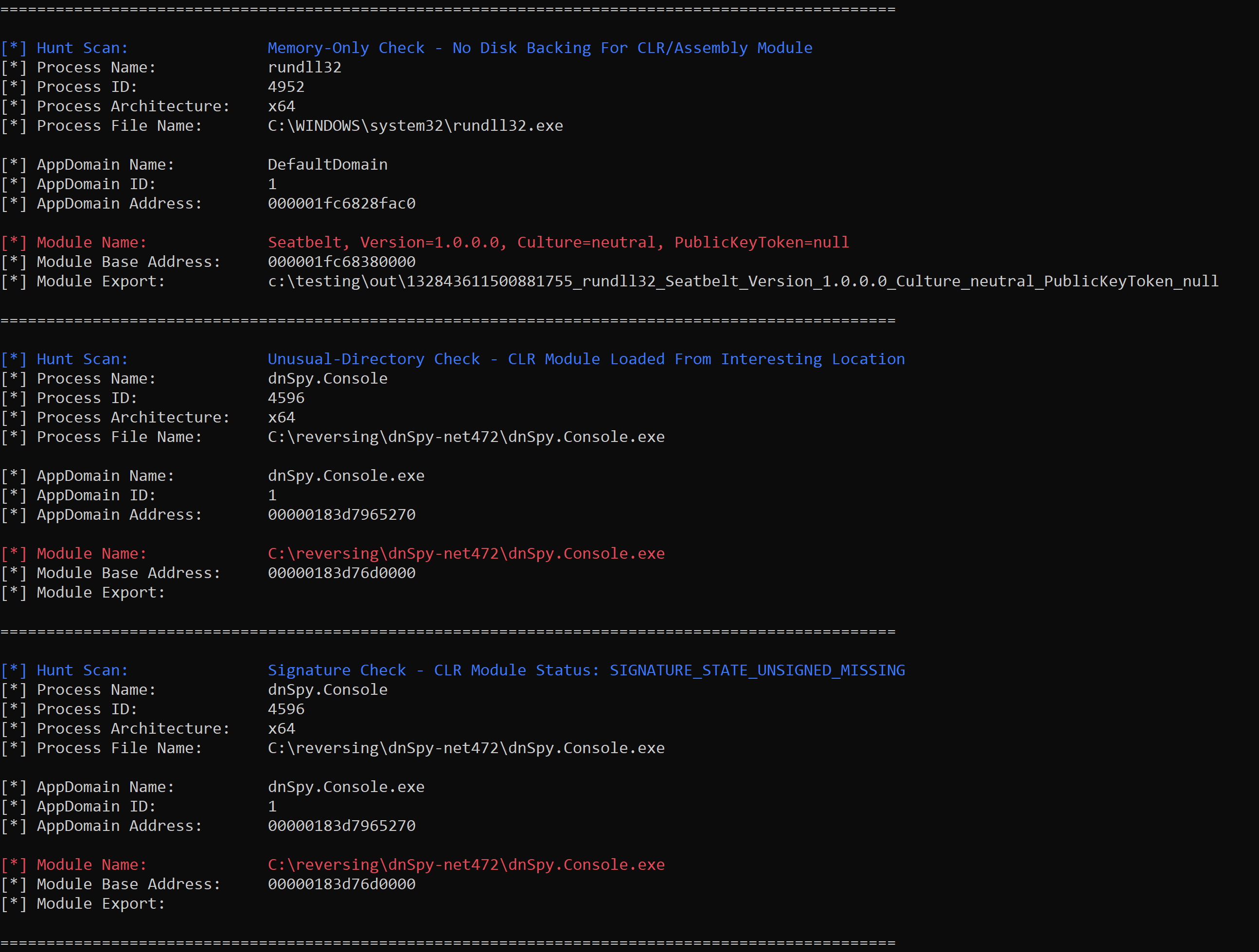
Zircolite v2.10 releases: fast SIGMA-based detection tool for EVTX or JSON Logs
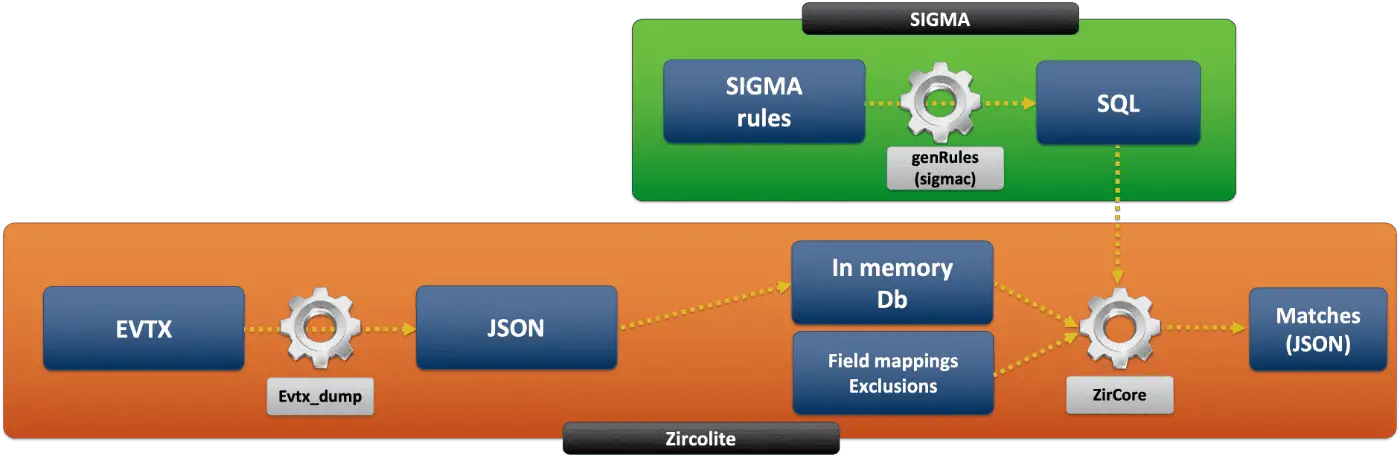
Zircolite Zircolite is a standalone tool written in Python 3. It allows to use SIGMA rules on MS Windows EVTX (EVTX and JSON format) Zircolite can be used directly on the...