SentryPeer v3.0.1 releases: distributed list of bad IP addresses and phone numbers
SentryPeer
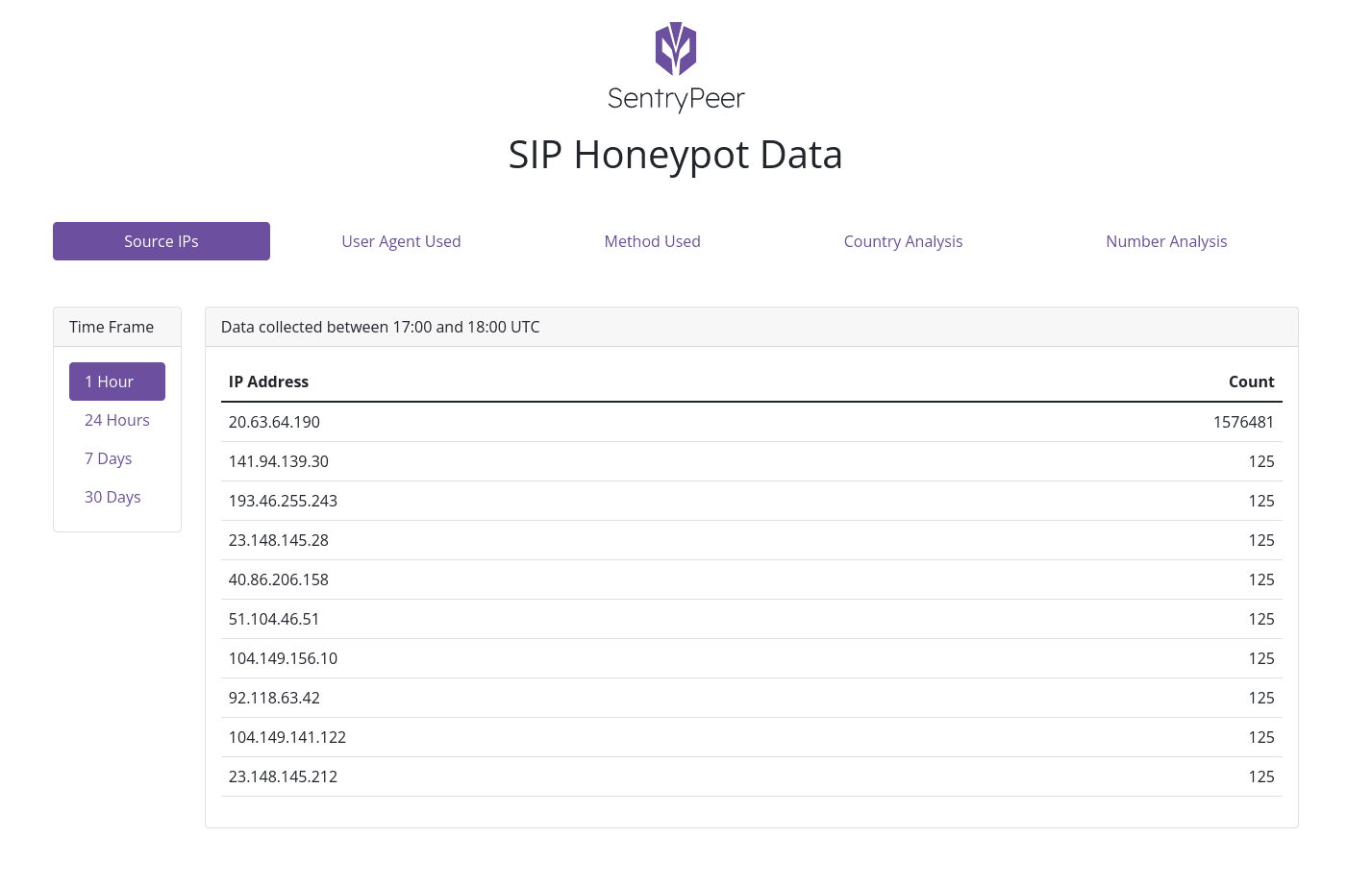
A distributed list of bad IP addresses and phone numbers was collected via a SIP Honeypot.
This is basically a fraud detection tool. It lets bad actors try to make phone calls and saves the IP address they came from and the number they tried to call. Those details are then used to block them at the service provider’s network and the next time a user/customer tries to call a collected number, it’s blocked.
Traditionally this data is shipped to a central place, so you don’t own the data you’ve collected. This project is all about Peer to Peer sharing of that data. The user owning the data and various Service Provider / Network Provider-related feeds of the data is the key bit for me. I’m sick of all the services out there that keep it and sell it. If you’ve collected it, you should have the choice to keep it and/or opt in to share it with other SentryPeer community members via p2p methods.
Of course, if you don’t want to run any of this and just buy access to the data that users have opted in to share, then that’s a choice too. One day, maybe.
The sharing part…you only get other users’ data if you share yours. That’s the key. It could be used (the sharing of data logic/feature) in many projects too if I get it right 🙂
Goals
- All code Free/Libre and Open Source Software
- FAST
- User owns their data
- User can submit their own data if they want to (you need to enable p2p mode –
-p) - User gets other users’ data ONLY IF they opt in to submit their data to the pool
- Embedded Distributed Hash Table (DHT) node using OpenDHT (
-pcli option) - Peer to Peer sharing of collected bad_actors using OpenDHT (default on)
- Peer to Peer data replication to receive collected bad_actors using OpenDHT (default on)
- Multithreaded
- UDP transport
- TCP transport
- TLS transport
- JSON logging to a file
- SIP mode can be disabled. This allows you to run SentryPeer in API mode or DHT mode only etc. i.e. not as a honeypot, but as a node in the SentryPeer community or to just serve replicated data
- SIP responsive mode can be enabled to collect data – cli / env flag
- Local data copy for fast access – cli / env db location flag
- Local API for fast access – cli / env flag
- Local Web GUI for fast access – cli / env flag
- Query API for IP addresses of bad actors
- Query API for IPSET of bad actors
- Query API for a particular IP address of a bad actor
- Query API for attempted phone numbers called by bad actors
- Query API for an attempted phone number called by a bad actor
- Fail2Ban support via
syslogas per feature request - Local sqlite database – feature / cli flag
- Analytics – opt in
- SDKs/libs for external access – CGRateS to start with or our own firewall with nftables
- Small binary size for IoT usage
- Cross-platform
- Firewall options to use distributed data in real time – DHT?
- Container on Docker Hub for latest build
- BGP agent to peer with for blackholing collected IP addresses (similar to Team Cymru Bogon Router Server Project)
- SIP agent to return 404 or default destination for SIP redirects
Changelog v3.0.1
- Add a check for a response code of 403 to trigger a new access token request for WebHooks in addition to a 401
Changes
-pedantic-errorsis now enabled by default inMakefile.am
Fixes
- Switch to
getsockname()to correctly get destination IP address for SIP TCP mode - Check for a blank
User-agentSIP header and add a test case. Only a missing one was catered for before.