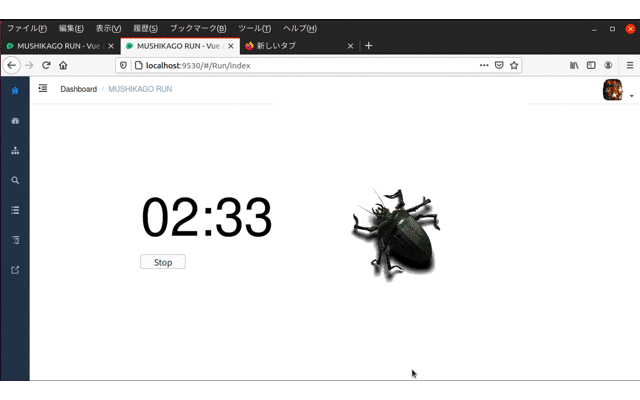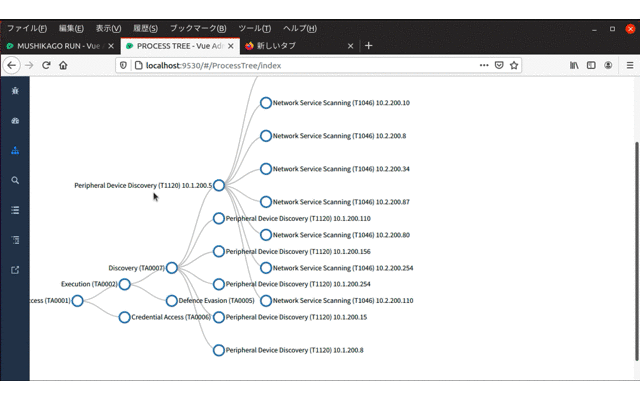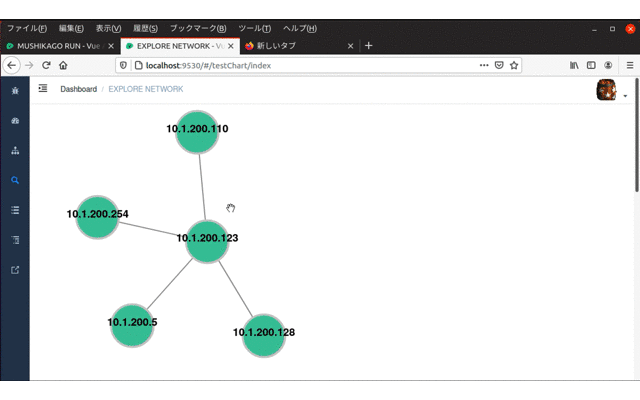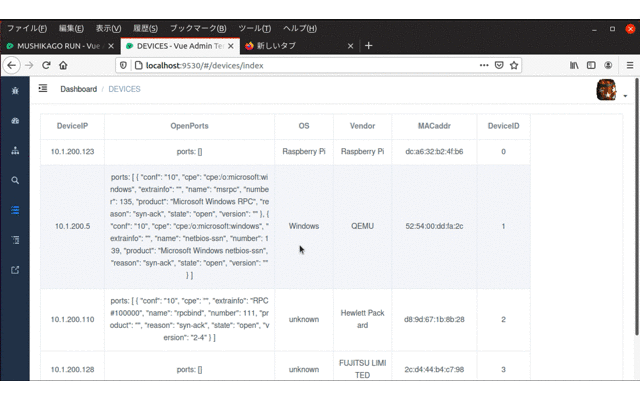
mushikago Mushikago is an automatic penetration testing tool using game AI, which focuses on the verification of...
Machine Learning
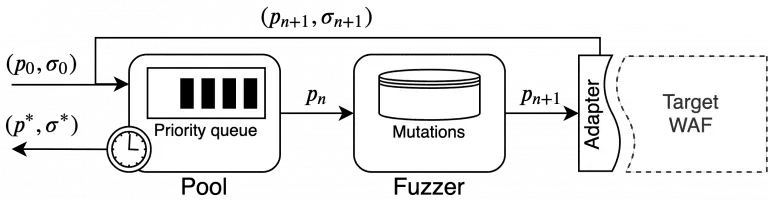
WAF-A-MoLE A guided mutation-based fuzzer for ML-based Web Application Firewalls, inspired by AFL and based on the FuzzingBook by Andreas Zeller...
AutoPentest-DRL: Automated Penetration Testing Using Deep Reinforcement Learning AutoPentest-DRL is an automated penetration testing framework based on...
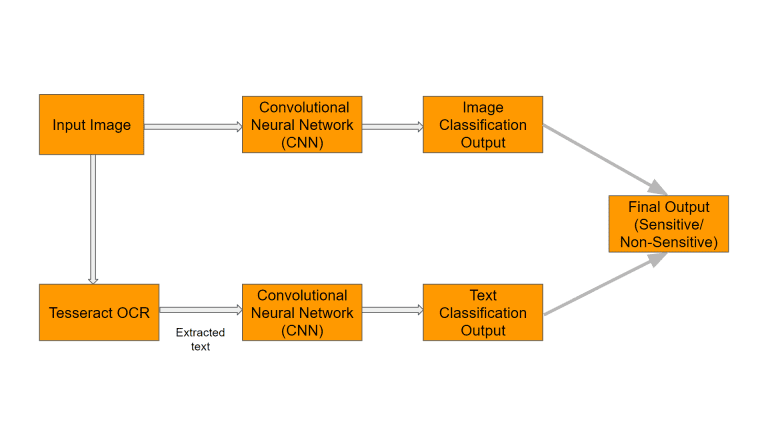
Detection of Sensitive Data Exposure in Images In the current age of smart devices and smartphones, any...
The idea of artificial intelligence (AI) has captured human imagination ever since it was first conceived. Nowadays...
Adversarial Threat Detector Adversarial Threat Detector makes AI development Secure. In recent years, deep learning technology has...
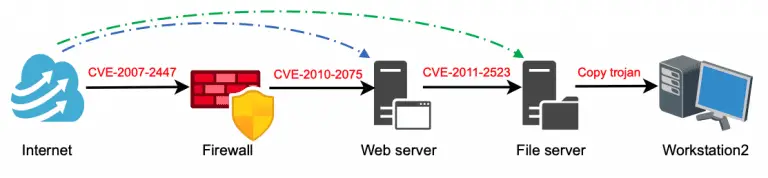
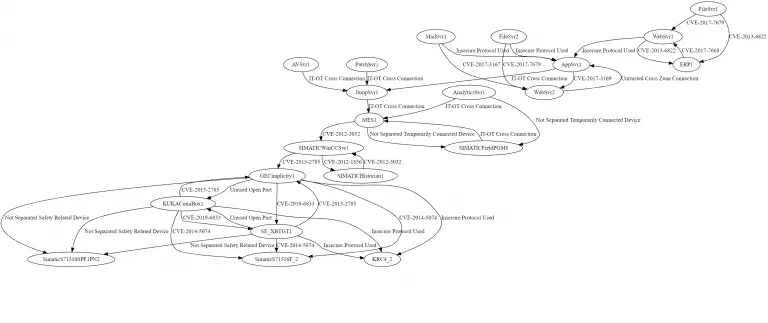
Automated Security Risk Identification Using AutomationML-based Engineering Data This prototype identifies security risk sources (i.e., threats and...
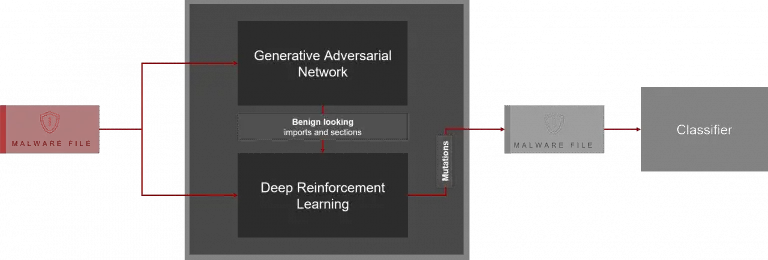
Pesidious – Malware Mutation using Deep Reinforcement Learning and GANs Pesidious is an open-source tool that uses...
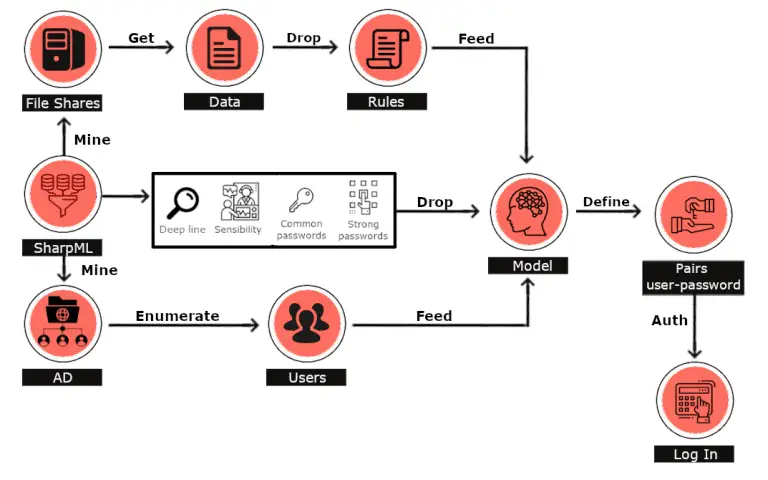
SharpML SharpML is a proof of concept file share data mining tool using Machine Learning in Python...
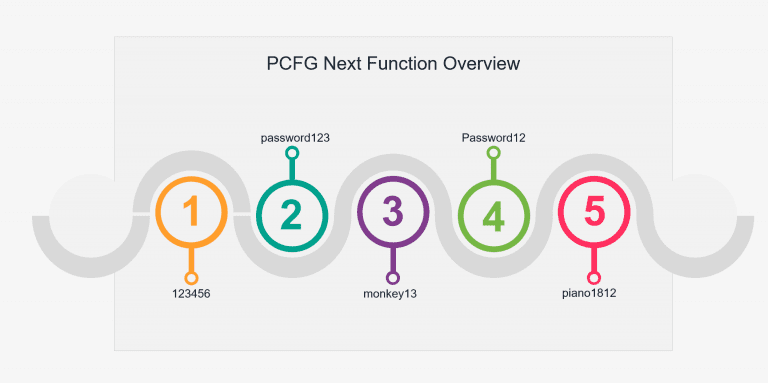
pcfg_cracker This project uses machine learning to identify password creation habits of users. A PCFG model is...
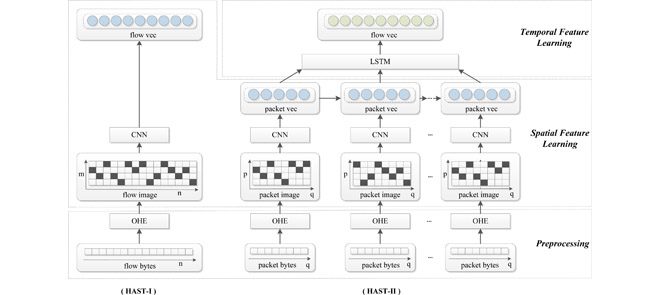
Deep Learning models for network traffic classification The development of an anomaly-based intrusion detection system (IDS) is...
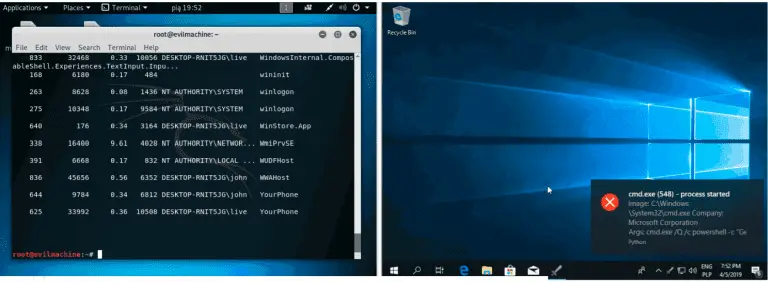
Attack Monitor Attack Monitor is Python application written to enhance security monitoring capabilities of Windows 7/2008 (and...
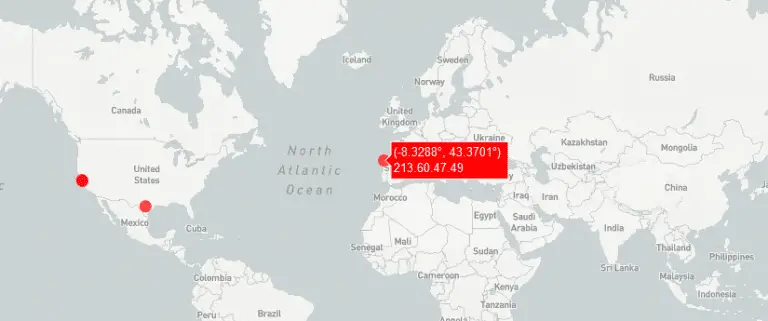
A-Detector A-Detector is a software developed to automate the analysis of network anomalies in large dataframes. Thanks...
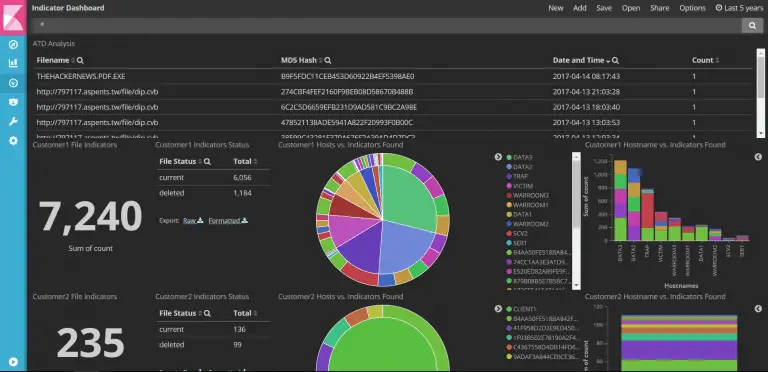
ManaTI Project Machine Learning for Threat Intuitive Analysis The ManaTI project consists of a front-end web application...
Automated Threat Intelligent System An improvised automated threat intelligent system with advanced vulnerability scanners and Opensource Intelligence...