If you were born in the last thirty years, you have lived through a time when vendors...
Technique
As we all know too well, iOS is not exactly open when it comes to handling various...
When working online, cyberattacks pose a threat to your business. Businesses are essential data-intensive. This data contains...
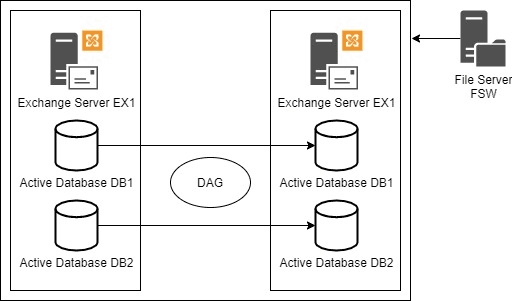
Exchange Server provides high availability and disaster recovery using Database Availability Group (DAG). This provides replication of...
Stellar® is a well-known data care company known for its data recovery, data erasure, file repair, and...
A malware infection can be devastating. Whether it happens to your personal devices or to your business...
While Linux proves itself to be the best OS for modifying your desktop settings, the story becomes...
Popular terms that come to mind in discussions about security testing are the so-called red team and...
As technology evolves, many businesses are revolutionizing their operations by leveraging online platforms and software that offer...
The benefits of hiring freelance websites specialists far outweigh any one-off costs. When you have a business...
You do not necessarily have to be a cybersecurity specialist to enjoy a good escape game. With...
Building a PC is a dream for everyone and if you’re looking to build your first gaming...
Cyberattacks are a bigger problem today than they have ever been. This might come as a surprise...
A recently discovered issue in the encryption algorithm GEA-1, which is used to encrypt data connections in...
GCP vs Azure vs AWS: In the latest times, we see a rapid increase in the demand...