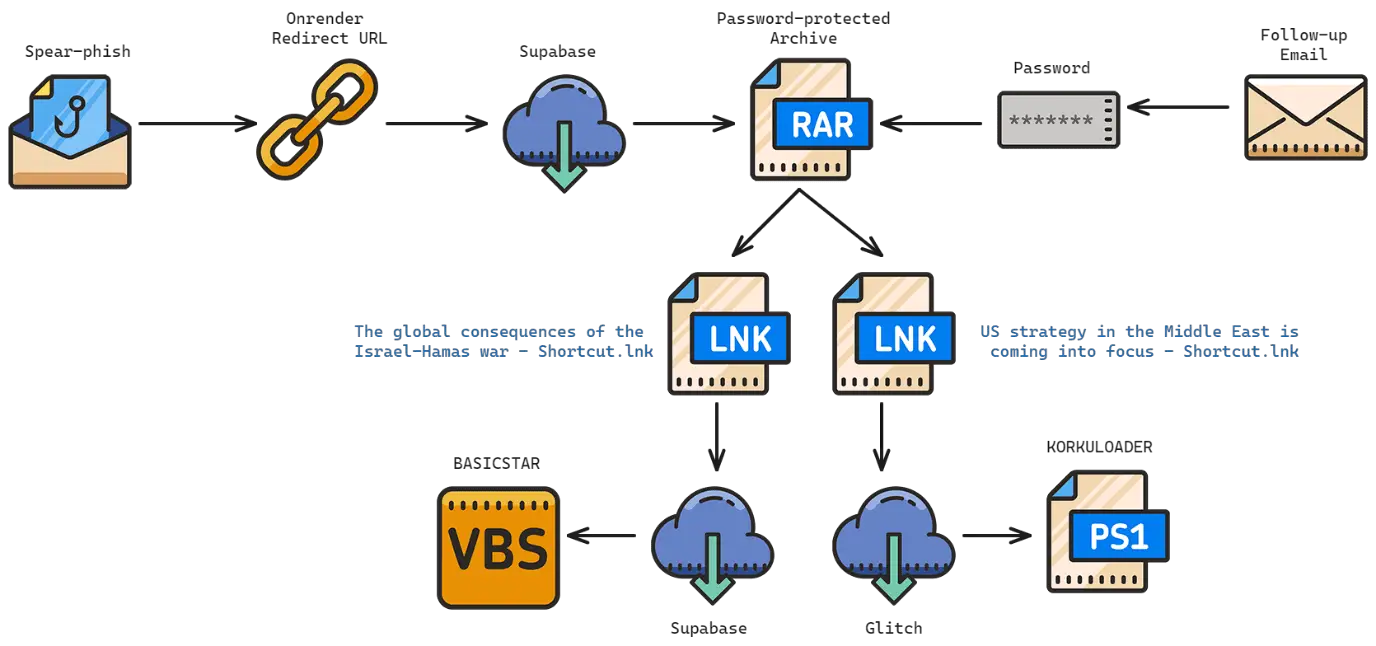
RAR + LNK Combo
CharmingCypress, also known as Charming Kitten, APT42, and TA453, is an Iranian-origin threat actor that has been observed engaging in sophisticated spear-phishing campaigns targeting various organizations, including think tanks, NGOs, and journalists. Volexity, a provider of managed security services, has extensively monitored the activities of CharmingCypress and identified several malware families associated with them, including POWERSTAR, POWERLESS, NOKNOK, BASICSTAR, and EYEGLASS.
One notable aspect of CharmingCypress’s tactics is their use of unusual social-engineering tactics in their phishing campaigns. For example, they have been known to engage targets in prolonged email conversations before sending links to malicious content. In a particularly remarkable campaign, CharmingCypress even created a fake webinar platform to lure targets, demonstrating a high level of sophistication in their operations.
In their malware distribution techniques, CharmingCypress often relies on spear-phishing, using tactics such as URL redirection chains culminating in the download of malicious files. They have also been observed using compromised webmail accounts belonging to real contacts of the target and employing multiple threat-actor-controlled email accounts within the same phishing chain.

One notable method employed by CharmingCypress is the use of RAR archives containing LNK files to deliver malware during spear-phishing campaigns. These LNK files, disguised as legitimate documents, ultimately lead to the execution of malware components.
Furthermore, CharmingCypress has been observed using malware-laden VPN applications as part of their spear-phishing campaigns. These applications are used to deploy malware onto the target’s system, with different malware payloads being delivered depending on the target’s operating system.
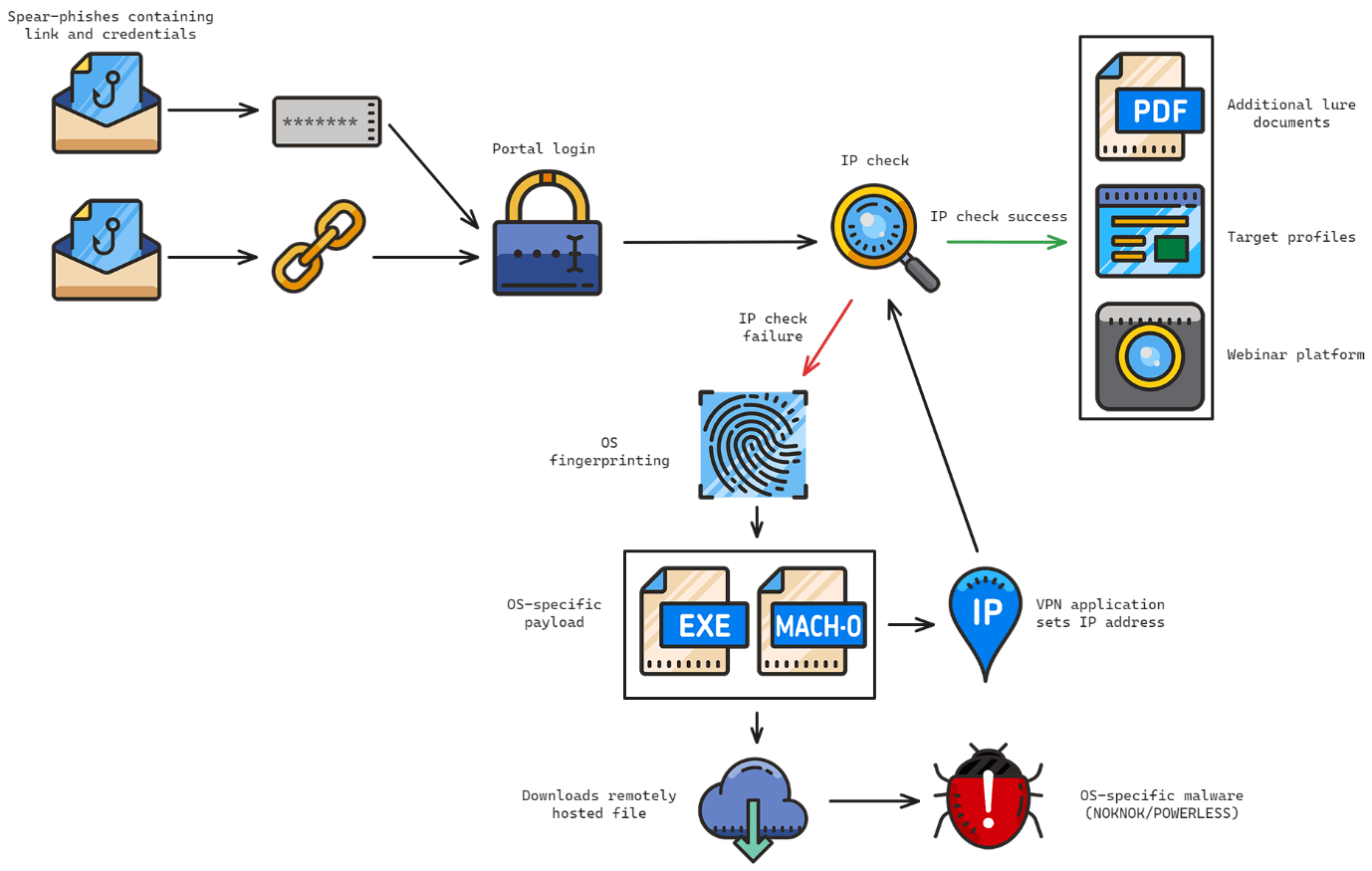
The backdoors deployed by CharmingCypress include POWERLESS, NOKNOK, and BASICSTAR, each with its own set of functionalities aimed at stealing information, maintaining persistence, and facilitating further compromise of the target’s system.
In one incident response case, Volexity gained valuable insight into CharmingCypress’s post-exploitation activities by analyzing memory from a compromised endpoint. This analysis revealed additional tools used by CharmingCypress, including Nirsoft Chrome History Viewer, RATHOLE, SNAILPROXY, CommandCam, and command-line copies of WinRAR and 7-Zip.
Overall, CharmingCypress represents a significant threat to organizations targeted in their spear-phishing campaigns, and their use of sophisticated social-engineering tactics and malware distribution techniques underscores the need for robust cybersecurity measures to mitigate the risk posed by such threat actors.