checkov
Checkov is a static code analysis tool for infrastructure-as-code. It scans cloud infrastructure provisioned using Terraform, Cloudformation, or kubernetes and detects security and compliance misconfigurations.
Checkov is written in Python and provides a simple method to write and manage policies. It follows the CIS Foundations benchmarks where applicable.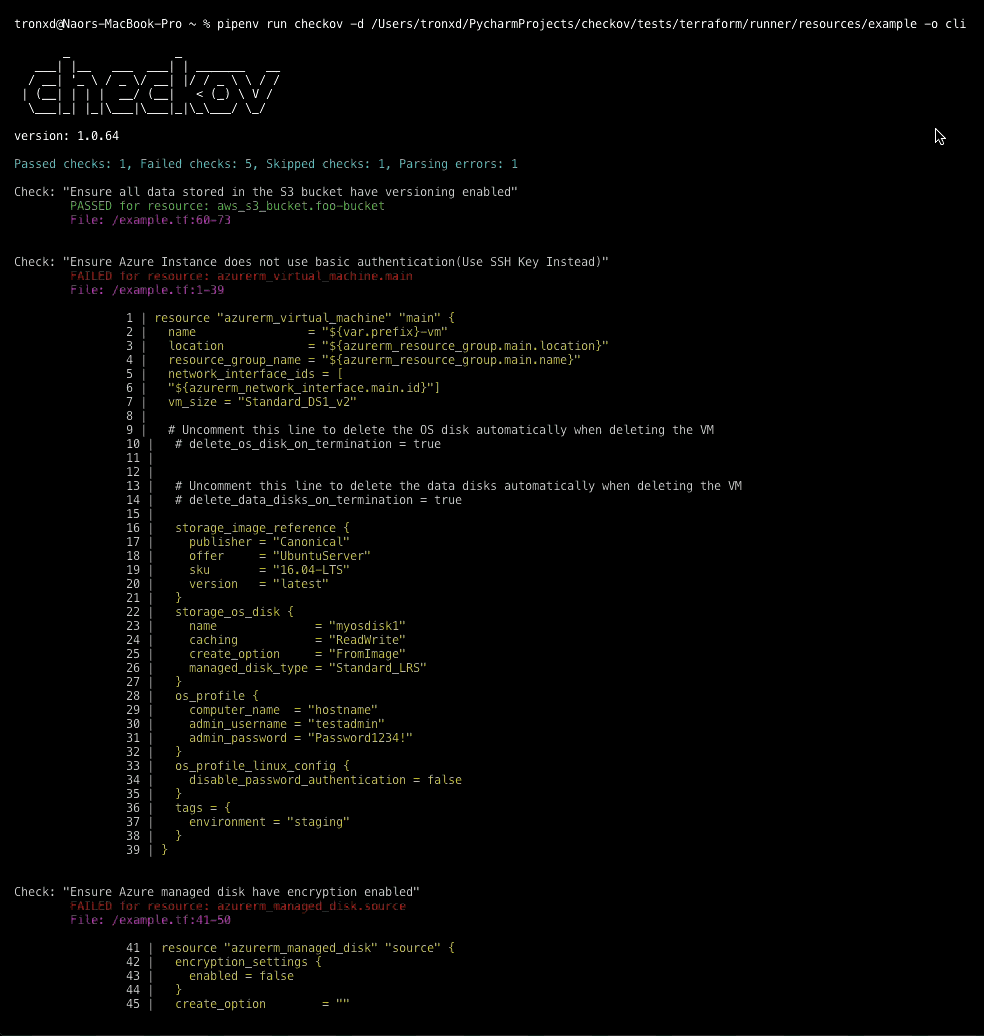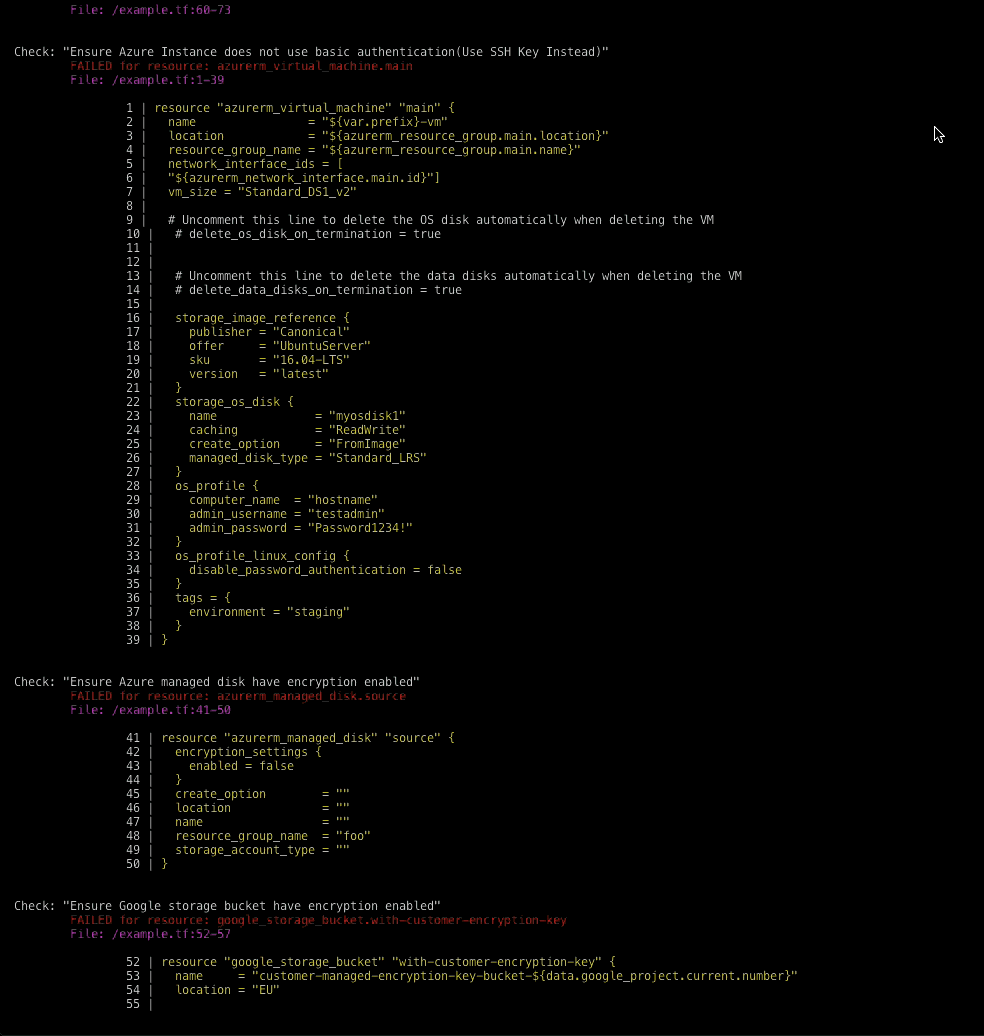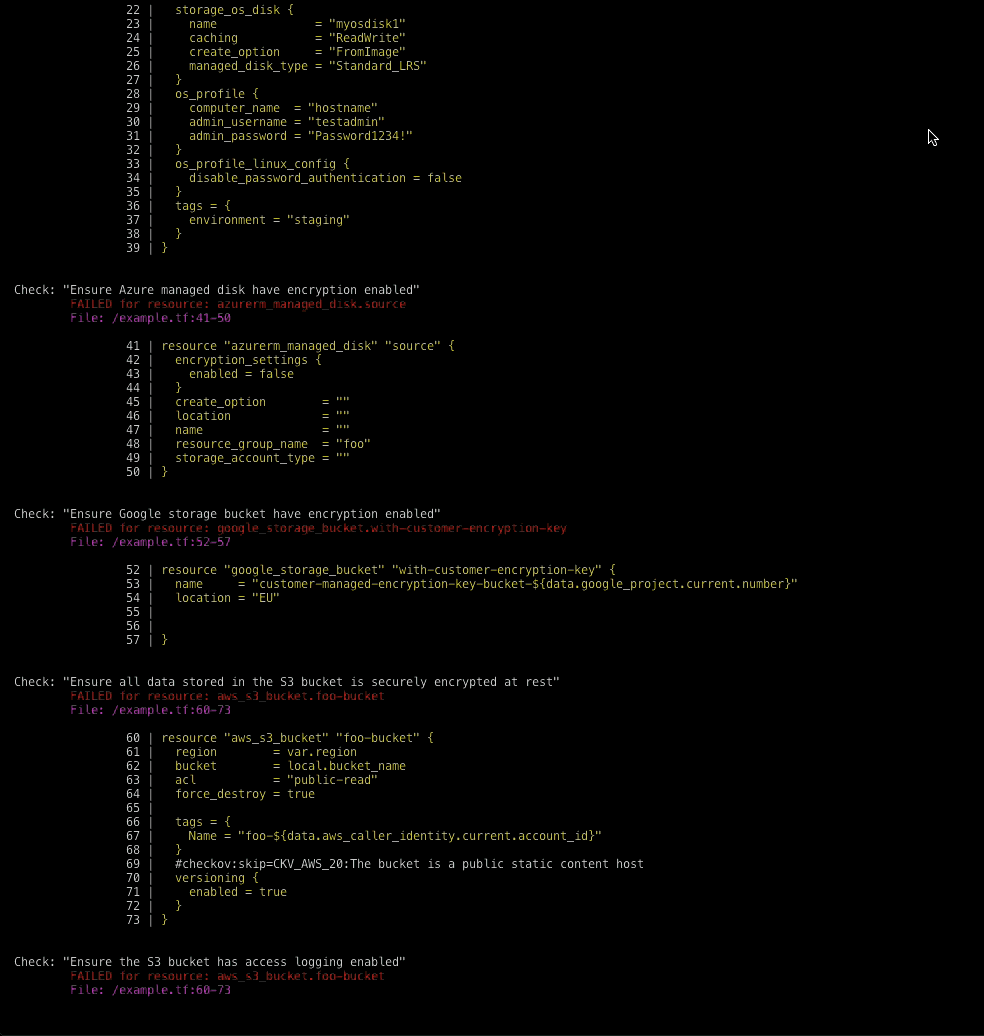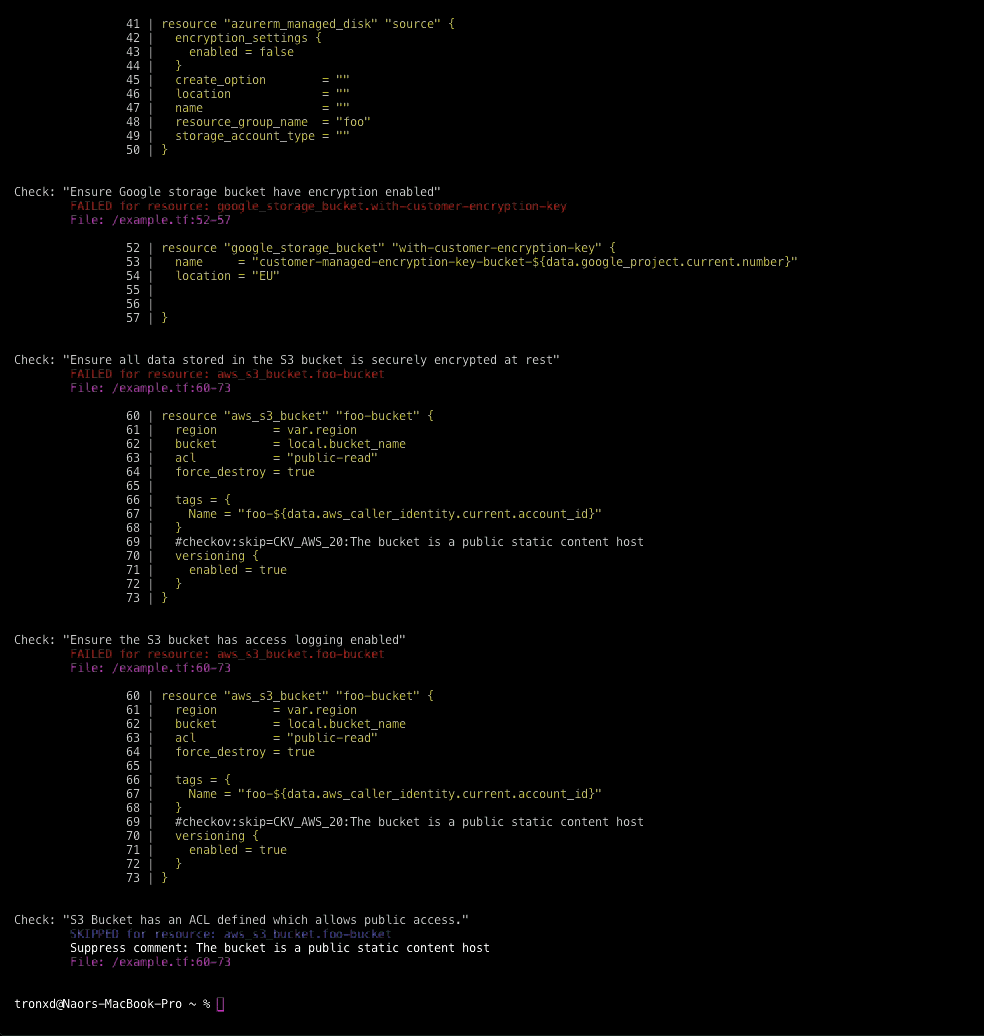
Features
- Over 1000 built-in policies cover security and compliance best practices for AWS, Azure, and Google Cloud.
- Scans Terraform, Terraform Plan, CloudFormation, Kubernetes, Dockerfile, Serverless framework, and ARM template files.
- Supports Context-awareness policies based on in-memory graph-based scanning.
- Supports Python format for attribute policies and YAML format for both attribute and composite policies.
- Detects AWS credentials in EC2 Userdata, Lambda environment variables, and Terraform providers.
- Identifies secrets using regular expressions, keywords, and entropy-based detection.
- Evaluates Terraform Provider settings to regulate the creation, management, and updates of IaaS, PaaS or SaaS managed through Terraform.
- Policies support the evaluation of variables to their optional default value.
- Supports in-line suppression of accepted risks or false positives to reduce recurring scan failures. Also supports global skip from using CLI.
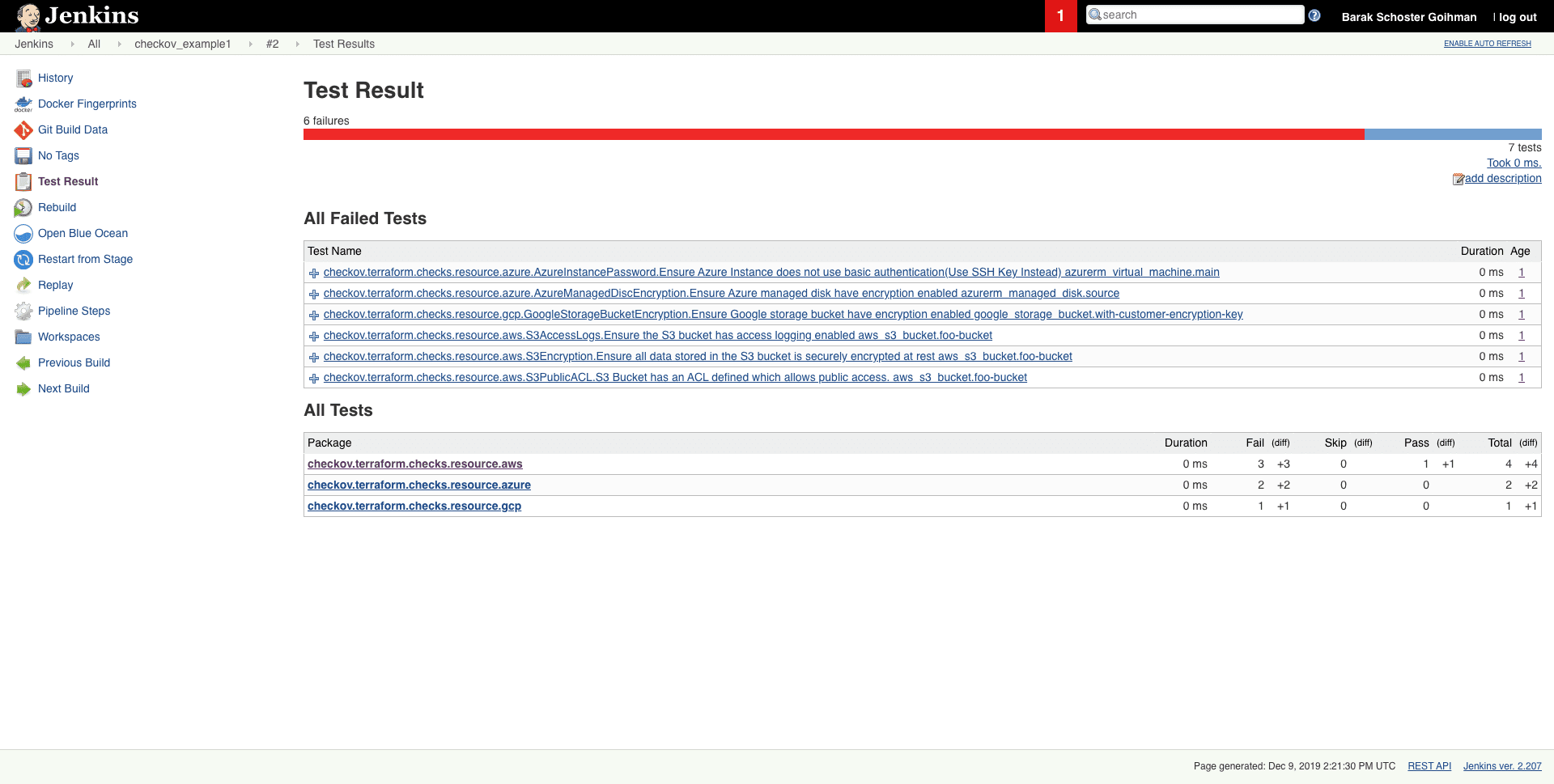
- Output currently available as CLI, JSON, JUnit XML, and github markdown and link to remediation guides.
Changelog v3.1.43
Feature
- terraform: add CKV2_AZURE_47, ensure storage account is configured without blob anonymous access – #5888
- terraform: Ensure SES Configuration Set enforces TLS usage – #5891
Bug Fix
- terraform: pod security policy removed in GKE 1.25 – #5675
Install && Use
Copyright 2019 Bridgecrew