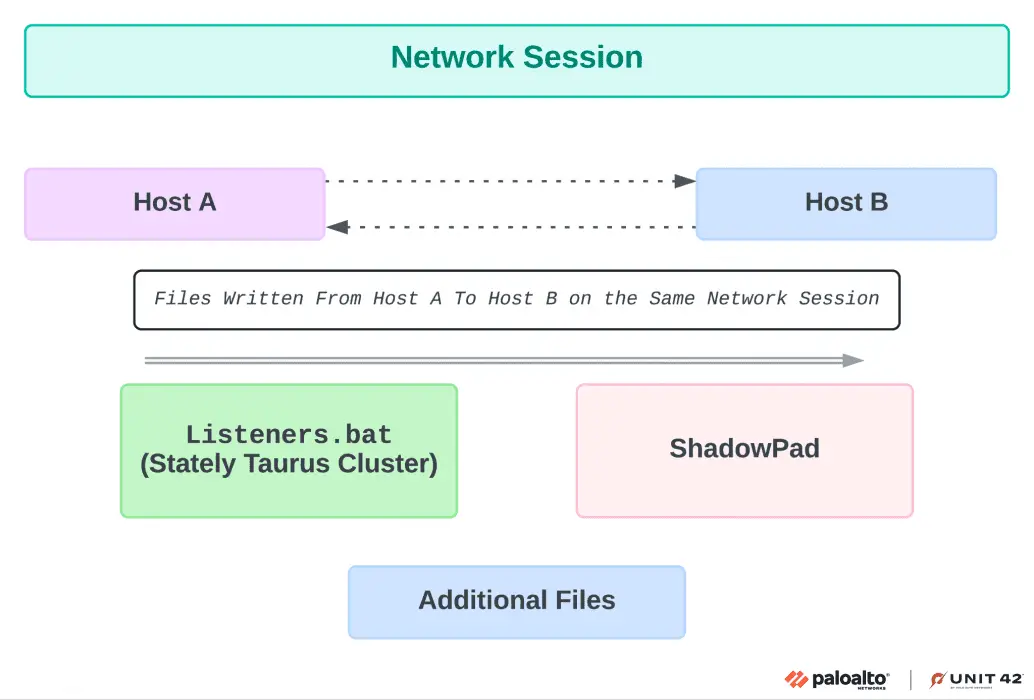
The observed connection between Listener.bat of Stately Taurus and ShadowPad | Image: Unit 42
In a recent report, cybersecurity researchers at Unit 42 have uncovered a novel and concerning tactic employed by the Chinese advanced persistent threat (APT) group Stately Taurus. This group, known for its cyberespionage campaigns targeting government entities in Southeast Asia, has been observed abusing the popular Visual Studio Code software to gain unauthorized access to sensitive networks.
What sets this attack apart is the first-known exploitation of VSCode’s embedded reverse shell feature in the wild. A technique originally described by security researcher Truvis Thornton in 2023, the APT group used VSCode to infiltrate target networks and gain persistent access. By abusing this relatively obscure feature, attackers managed to bypass traditional defenses and deliver additional malware payloads.
VSCode, whether in its portable or already installed form, allows attackers to run commands and create new files in compromised environments. Leveraging the code.exe tunnel command, attackers received access to the compromised machine via a web environment after logging into GitHub. This entry point allowed Stately Taurus to deliver malicious payloads, conduct reconnaissance, and exfiltrate sensitive data without raising suspicion.
The campaign further used a scheduled task to maintain persistent access through a reverse shell, delivering their malicious code stealthily through a script named startcode.bat. This technique represents a growing trend of abusing legitimate tools to evade detection in sophisticated cyberespionage operations.
This latest campaign is believed to be a continuation of Stately Taurus’ prior operations. In 2023, the APT group was linked to an espionage campaign that used the ToneShell backdoor, known for encrypting exfiltrated files with a unique 13-character password. By tracing this specific password, Unit 42 researchers connected the current VSCode abuses to the same APT group. They noted similarities in tactics, techniques, and procedures (TTPs), as well as in the targeted victimology—primarily government entities in Southeast Asia.
While investigating Stately Taurus’ activity, Unit 42 researchers uncovered another threat cluster in the same environment, leveraging the ShadowPad backdoor, a tool long associated with Chinese threat actors since at least 2017. This second campaign occurred concurrently with Stately Taurus’ VSCode abuse and even shared network sessions on targeted machines. While forensic evidence suggests possible collaboration between these two clusters, the exact relationship remains unclear. The overlap could point to either a joint operation between two Chinese APT groups or separate actors leveraging each other’s access.
During their espionage operations, Stately Taurus used various tools to exfiltrate sensitive information. By executing the widely used file archiver rar.exe over SMB, attackers attempted to archive and steal data from drives across the infected network. To blend in with legitimate network traffic, they used curl to upload exfiltrated data to Dropbox, a legitimate cloud storage service.
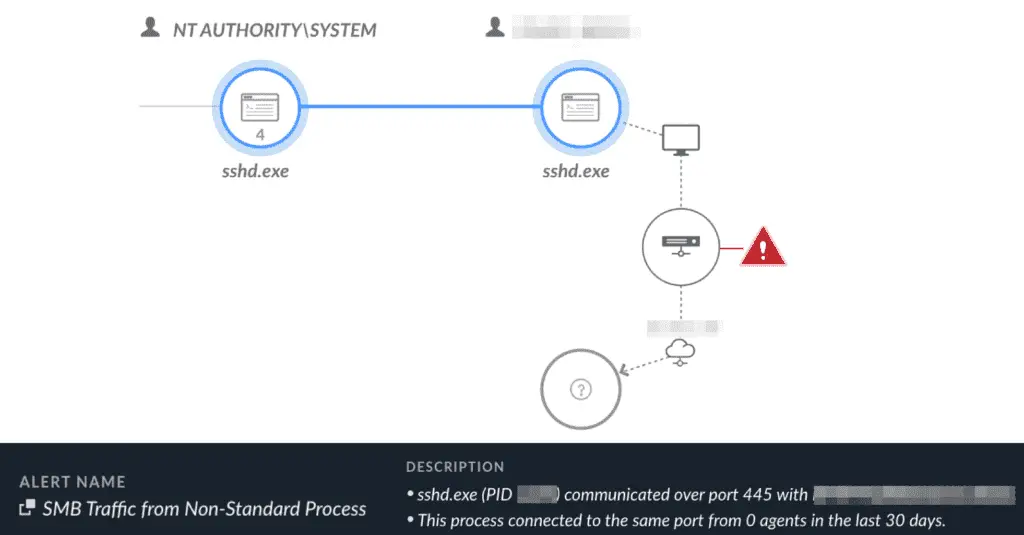
The group also employed the OpenSSH executable (sshd.exe) to transfer files and execute commands remotely, while SharpNBTScan (renamed as win1.exe) was used for network scanning. Notably, batch files such as Listeners.bat were deployed to archive and prepare files for exfiltration, further obfuscating their malicious activities.
Organizations, particularly those in government sectors, are urged to monitor for unusual VSCode activity and review persistence mechanisms such as scheduled tasks that could indicate compromise.
Related Posts:
- Chinese APTs Target ASEAN Entities, Stealing Sensitive Diplomatic and Economic Data
- Persistent Espionage Attacks on National Infrastructure Raising Alarm
- Malicious VSCode extensions steal PII and enable backdoors
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger