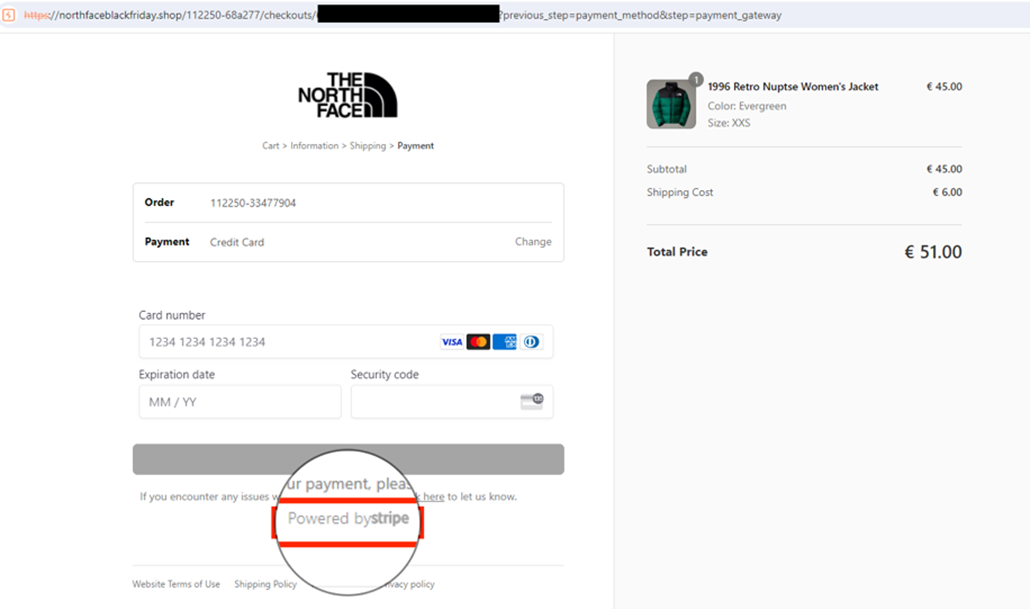
Payment prompt screen on phishing page that uses Stripe | Image: EclecticIQ
In a detailed report released by the EclecticIQ Threat Research Team, cybersecurity analysts have uncovered a well-coordinated phishing campaign targeting e-commerce shoppers in the United States and Europe during the lead-up to Black Friday. The campaign, attributed to a Chinese financially motivated threat actor dubbed SilkSpecter, demonstrates a high level of sophistication, leveraging legitimate technologies and infrastructure to deceive victims and exfiltrate sensitive data.
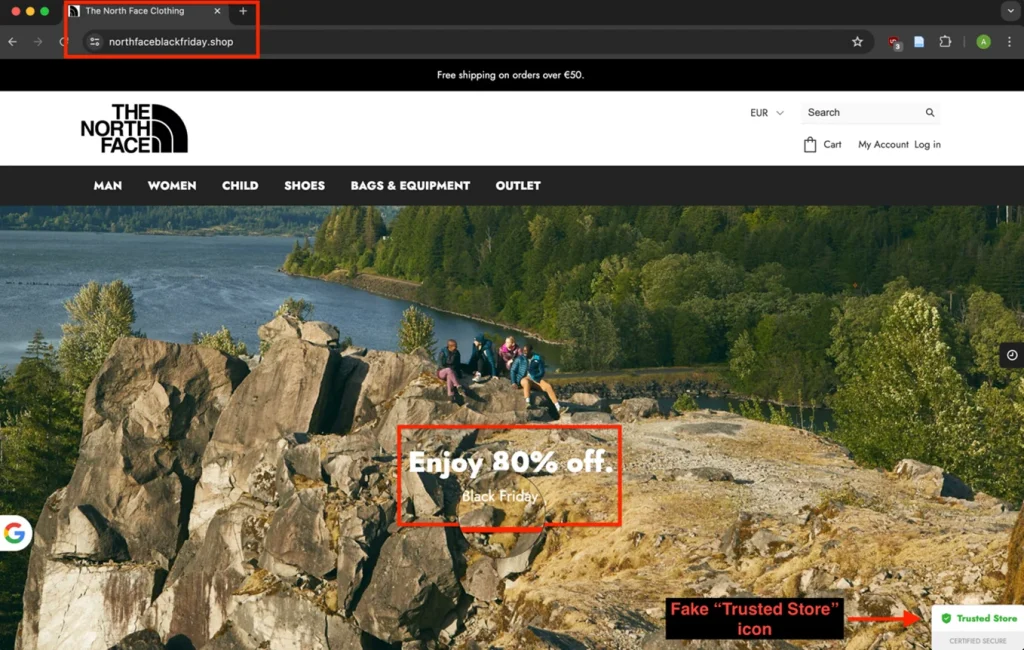
The campaign exploited the peak shopping season by offering fake Black Friday discounts to lure unsuspecting users. Victims were enticed by phishing sites promoting seemingly irresistible deals of “80% off” on popular items. According to EclecticIQ, these sites “used Google Translate to dynamically adjust the website’s language based on each victim’s IP location,” thereby enhancing credibility and broadening their reach to an international audience.
At the core of the operation was SilkSpecter’s ability to abuse Stripe, a legitimate payment processing service. Victims’ payments appeared to process normally, but their Cardholder Data (CHD) and Sensitive Authentication Data (SAD) were covertly transmitted to a server controlled by the attackers. The report states, “The [phishing] site is not only processing the payment through legitimate-looking means but is also capturing sensitive information, including card details, and relaying them to a separate server controlled by the attacker.”
SilkSpecter further incorporated OpenReplay, TikTok Pixel, and Meta Pixel trackers into their phishing kits to monitor visitor interactions, collecting detailed metadata such as IP addresses, geolocation, and browser information. This meticulous tracking enabled real-time campaign adjustments and improved effectiveness.
Analysts linked SilkSpecter’s phishing operations to over 4,000 domain names and 89 IP addresses, many of which were hosted on Chinese infrastructure. The threat actor favored Chinese registrars such as West263 International Limited and Alibaba Cloud, while masking their origin through services like Cloudflare.
The report also noted that SilkSpecter relied on oemapps, a Chinese Software-as-a-Service (SaaS) platform, to rapidly create phishing websites. EclecticIQ analysts observed JavaScript code with Mandarin comments and “zh-CN” HTML language tags on phishing pages, reinforcing the attribution to a Chinese-speaking threat actor.
SilkSpecter’s campaign doesn’t end with the theft of payment data. Victims were prompted to provide their phone numbers, which EclecticIQ suggests could be used for secondary attacks such as vishing or smishing. This layered strategy enables attackers to circumvent additional security barriers, potentially leading to further compromise of victims’ accounts.
As the report concludes, “By impersonating trusted entities, such as financial institutions or well-known e-commerce platforms, SilkSpecter could very likely circumvent security barriers, gain unauthorized access to victim’s accounts, and initiate fraudulent transactions.”
Related Posts:
- 2FA Bypass and More: Inside ONNX Store, the Phishing Threat to Your Finances
- Operation FlightNight: Indian Government and Energy Sector Breached in Targeted Cyber Espionage Campaign
- Cyberattack Halts Australian Ports, Choking Supply Chain
- Kaspersky Uncovers 10,000 Cyberattacks: Global Organizations Targeted