Command Line Spoofer
An example of using C# to inject a meterpreter shell, whilst spoofing the command line. The command line is stored in the Process Environment Block, is logged when a new process starts and is displayed in tools such as Process Hacker and Task Manager.
Introduction
This code is based on the How to Argue like Cobalt Strike blog by Adam Chester/XPN, the blog explains how cobalt strike spoofs the command line of a process when injecting a beacon.
I used this as a basis to create a C# version that spawns a PowerShell process and injects a meterpreter reverse shell. Granted there is no need for a .Net binary to do this but it demonstrates how commands can be spoofed.
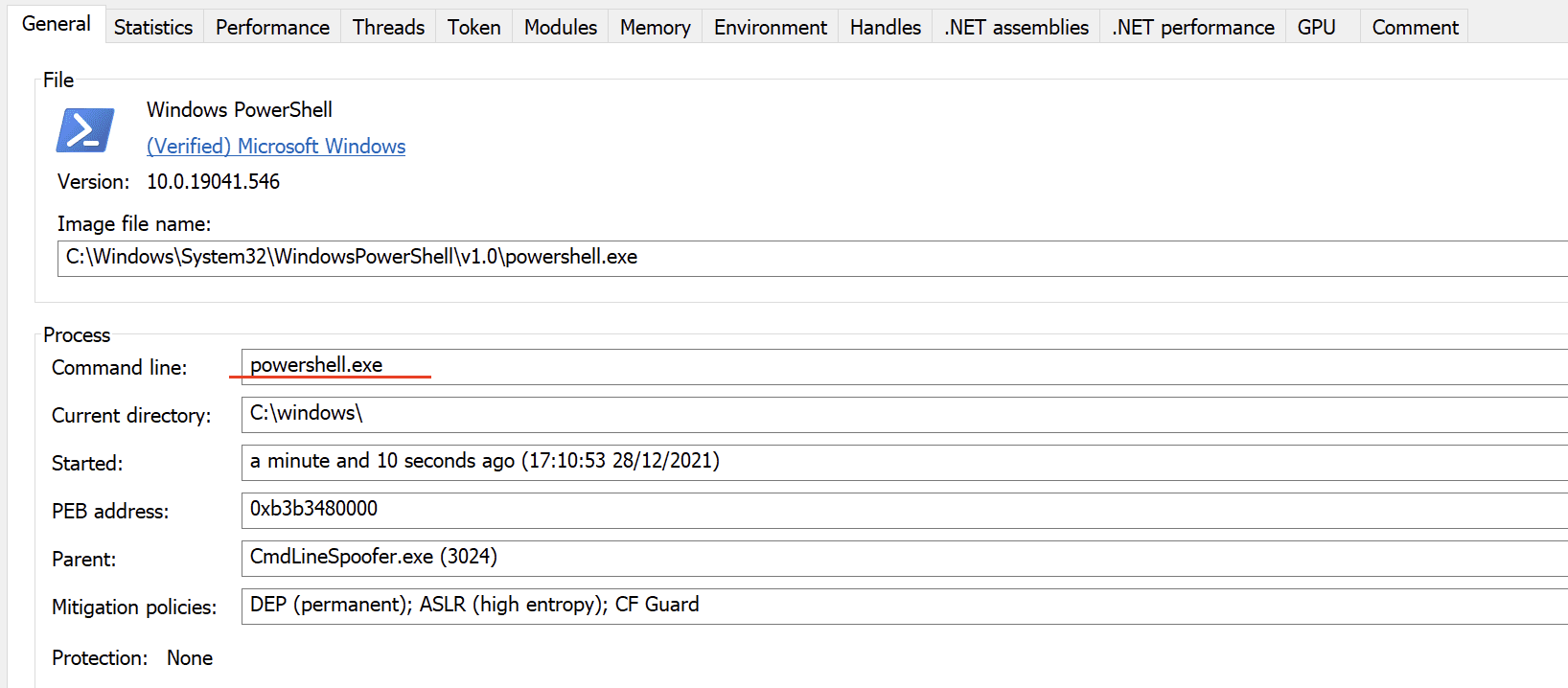
A new process is started in a suspended state with a spoofed command-line argument.
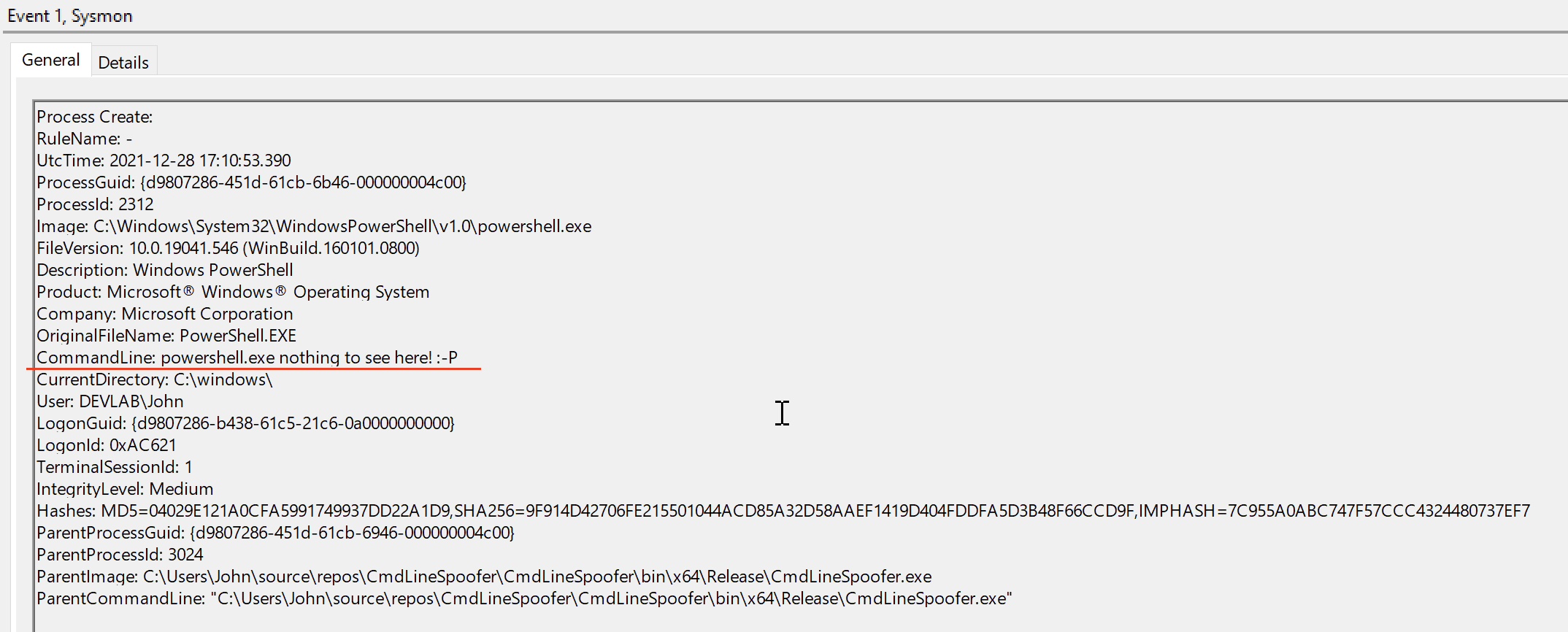
The spoofed command is logged but we are able to change the command line in the process PEB. When the main thread is resumed the process uses the new command line in the PEB.
Example
Execution of the code is shown below:
This example injects a meterpreter reverse shell using PowerShell but it gets logged with a spoofed command-line argument.
Proof of Concept
Sysmon logs the original (spoofed) command line:
Process Hacker does not reveal the executed command:

Download