Confused
A tool for checking for lingering free namespaces for private package names referenced in dependency configuration for Python (pypi) requirements.txt, JavaScript (npm) package.json, or PHP (composer) composer.json.
What is this all about?
On the 9th of February 2021, security researcher Alex Birsan published an article that touched on different resolve order flaws in dependency management tools present in multiple programming language ecosystems.
Microsoft released a whitepaper describing ways to mitigate the impact, while the root cause still remains.
Interpreting the tool output
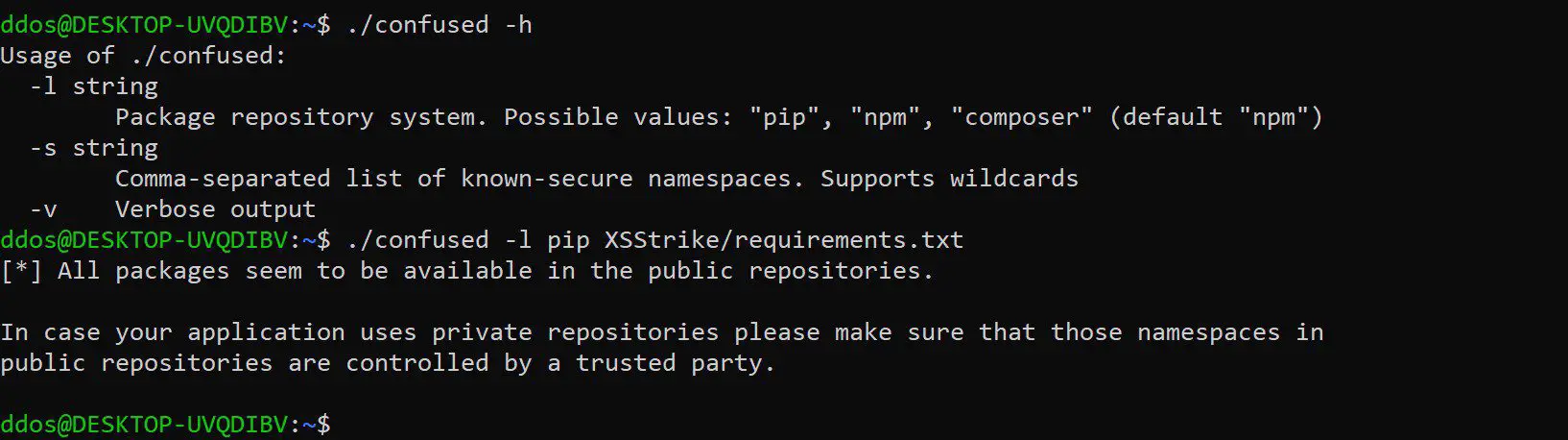
confused simply reads through a dependency definition file of an application and checks the public package repositories for each dependency entry in that file. It will proceed to report all the package names that are not found in the public repositories – a state that implies that a package might be vulnerable to this kind of attack, while this vector has not yet been exploited.
This however doesn’t mean that an application isn’t already being actively exploited. If you know your software is using private package repositories, you should ensure that the namespaces for your private packages have been claimed by a trusted party (typically yourself or your company).
Known false positives
Some packaging ecosystems like npm have a concept called “scopes” that can be either private or public. In short, it means a namespace that has an upper level – the scope. The scopes are not inherently visible publicly, which means that confused cannot reliably detect if it has been claimed. If your application uses scoped package names, you should ensure that a trusted party has claimed the scope name in the public repositories.
Use
Changelog v0.5
Installation
Copyright (c) 2021 Visma Security, Joona Hoikkala