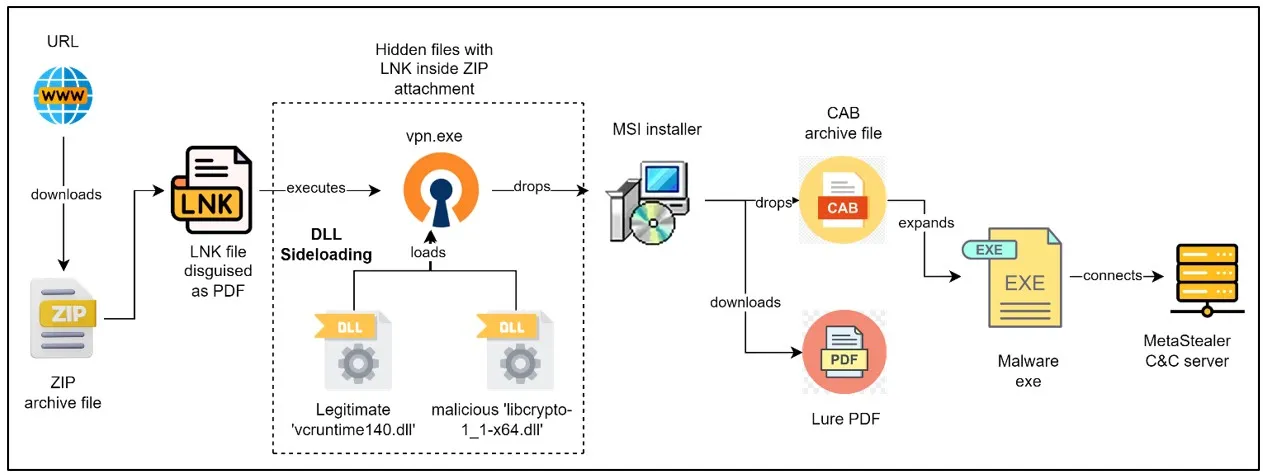
Infection chain
Recently, Cyble Research and Intelligence Labs (CRIL), in a meticulous investigation, has unveiled a chilling campaign that preys upon individuals seeking refuge and hope—those applying for asylum in the United States. The actors behind this campaign deploy a cunning weapon: the MetaStealer malware, a menace hidden within what appears to be a beacon of aid.
The deceit begins with a ZIP archive, seemingly innocuous, available through a link that might as well have been scattered across the digital winds via spam emails. This ZIP harbors not just files but a trap: a shortcut LNK file masquerading as a PDF document. This disguise is the first step in a meticulously crafted deception, leading the unwary down a path paved with malicious intent.

Upon the execution of this shortcut, a sequence unfurls—a VPN application springs to life, employing DLL sideloading techniques to inject a hidden, malicious DLL. This act is but the prelude to the main event: the deployment of an MSI installer that, while presenting a decoy PDF to the victim, quietly unleashes the MetaStealer malware.
The lure is crafted with chilling precision—an “I-589, Application for Asylum and for Withholding of Removal” document, a facade that preys on the hopes and vulnerabilities of those seeking a haven. This document is nothing but a mirage, a ploy employing social engineering to lower the guard of its targets, making the infiltration all the more insidious.
MetaStealer, once deployed, is a thief in the night. It reaches into the very heart of the victim’s digital life, pilfering information that should be sacrosanct: browser data, autofill information, cookies, and login credentials. But its reach does not end there; MetaStealer communicates with a Command-and-Control server, ready to be used for purposes dark and unknown.
MetaStealer is the product of continuous development, with roots entwined with the RedLine info-stealer malware. Its dissemination through malicious spam and malvertising campaigns reveals a threat that is both adaptable and persistent, signaling a clear and present danger to the security domain.
The use of official documents as bait exploits emotions establishes a veneer of legitimacy, and attracts a wide audience, amplifying the malware’s effectiveness. CRIL’s revelations serve as a stark reminder of the importance of vigilance. In a landscape where attackers camouflage their intentions with the trappings of legitimacy, the ability to discern the genuine from the deceitful becomes paramount.