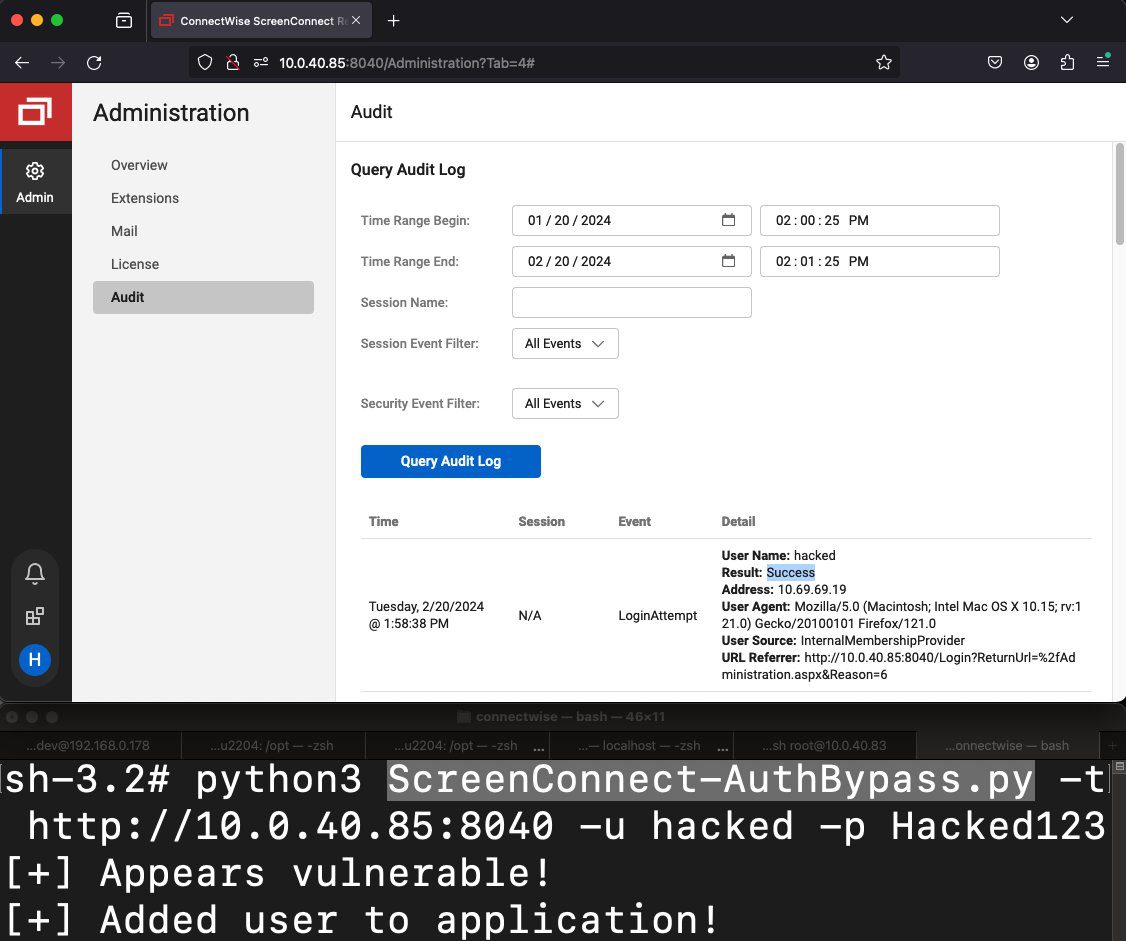
PoC | Image: @Horizon3Attack
In a chilling development, ConnectWise issued a critical security advisory on February 19, 2024, exposing two gaping security vulnerabilities in its popular ScreenConnect remote access software. The most severe of these bugs, an authentication bypass vulnerability, could leave systems open to devastating attacks, even without any need for user involvement.
Exploit in the Wild
ConnectWise has shared publicly that there are users affected by the recent ScreenConnect vulnerabilities, confirming in-the-wild exploitation. “We received updates of compromised accounts that our incident response team have been able to investigate and confirm. The following IP addresses were recently used by threat actors that we are making available for protection and defense,” the company warned.
They share 3 observed IPs exploiting & installing persistence
- 155.133.5.15
- 155.133.5.14
- 118.69.65.60

Compounding the seriousness of the issue, security researchers at Huntress warn of a rapidly developed proof-of-concept (PoC) exploit for this authentication bypass, indicating that attackers are already on the prowl. An alarming scan via the Censys platform revealed over 8,800 servers still vulnerable to attack.
The Nature of the Threat
- Authentication Bypass: Attackers can bypass the standard login requirements of ScreenConnect servers, granting them free rein to execute malicious code or steal sensitive data.
- Path Traversal (Elevated Privileges): This bug, though less severe, gives attackers already inside a system an easy path to escalate their privileges and cause even more damage.
What’s Affected
All versions of ScreenConnect up to 23.9.7 are vulnerable. If your organization uses ScreenConnect, particularly in an on-premises setup, you are at risk! ConnectWise has, thankfully, moved quickly to address the situation.
What You MUST Do
-
Update Immediately! If you run ScreenConnect on-premises, patch your servers to version 23.9.8 right away. ConnectWise is also providing patches for older versions (22.4 through 23.9.7), but they strongly recommend a full upgrade to 23.9.8.
-
Stay Vigilant: Even after patching, remain alert for signs of intrusion. Thoroughly audit logs and monitor for abnormal activity.
-
Heed Best Practices: This incident underscores the importance of:
- Timely patching of critical software.
- Minimizing exposure of internet-facing services.
- Defense-in-depth strategies that layer security controls.